
What used to be commonly known by names such as computer security or IT security is now most commonly referred to as cybersecurity. The techniques of securing computers, applications, networks, programs and data have evolved and so has the terminology. The change in the jargon reflects the progression from discrete to interconnected devices and networks. It is only when the computers and devices became connected with each other – and with the Internet – that the issues and attempts of unauthorised access became prominent.
Simply put, cybersecurity is the protection of computer systems from cyber-attacks. This is made possible with multiple layers of security across the system, individual devices, enterprises and even nations against unauthorised access and exploitation.
Cybersecurity is a constant battle
Preventing cyberattacks is a challenging task for security professionals and to accomplish that, cybersecurity experts should stay ahead of cyber attackers and cybercriminals. A range of effective methods and technologies have been devised to strengthen cybersecurity. One important aspect of cybersecurity is identity and access management (IDAM). IDAM allows various defined levels of access on the basis of individual roles, administrator levels and even at a system level. The common IDAM methods include single sign-on systems, multi-factor authentication, privileged access management (PAM), biometrics, voice or facial recognition, and other distinctive physical attributes to verify and identify individuals. IDAM procedures are being implemented at all levels of businesses, enterprises and even for national-level security with the growth of eGovernment systems.
Another common security measure is Security Information and Event Management (SIEM) software and services. The term combines security information management (SIM) and security event management (SEM) and is provided by vendors as software or appliance. SIEM works by collecting log data and delivering real-time insights and generates security alerts using a range of techniques. SIEM is used by enterprises where compliance to a set, or sets, of rules is a strong factor. In addition, it also prevents interferences from individual attackers, organised crime groups, or other actors.
SIEM systems comprise three major components:
- Data collection. SIEM system collects logs and data from system activity, access, firewalls, application monitors, operating system layers and network traffic and generates an event every time activity happens.
- Data analysis. The SIEM system is tasked with correlating and analysing data in a format. The analysis is performed in various ways: log management and retention, event correlation, user activity monitoring, and predictive and forensic analysis.
- Another major step is reporting in the form of real-time alerts, dashboards, email and SMS notifications of events, analytical reporting, auditing and governance, and compliance.
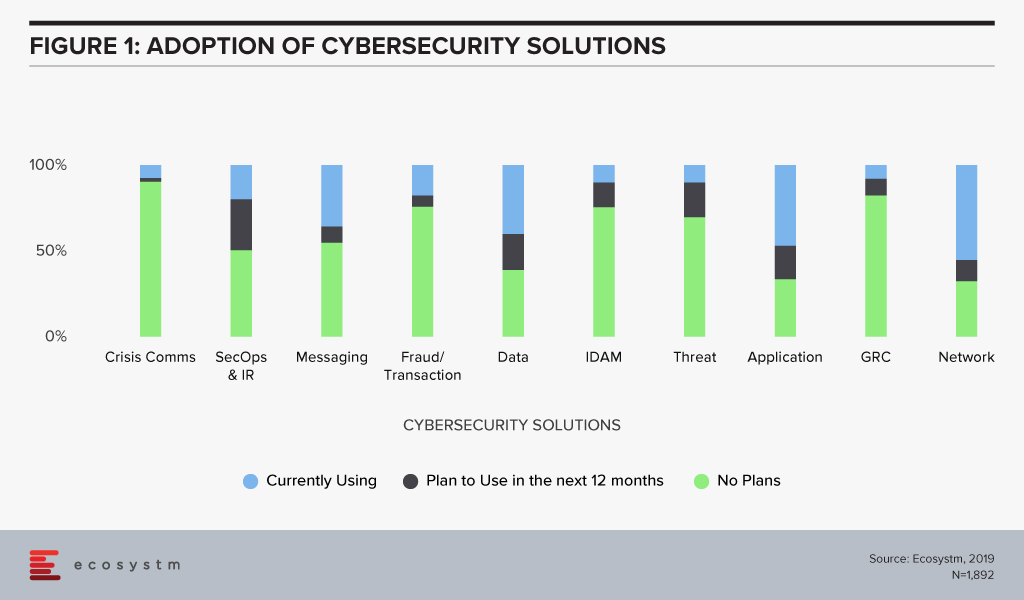
The global Ecosystm Cybersecurity Study covers various cybersecurity solutions such as Crisis Communication solutions; Security Operations & Incident Response, IDAM and more. The study shows that organisations are primarily focusing more on Application, Data and Network level security, whereas, the other cybersecurity fields such as Crisis communication, Fraud transaction, IDAM, Threat Analysis and Reporting are looked down.
National Cybersecurity and Safety
Countries across the globe are accelerating their cybersecurity efforts to address risks, enhance public safety, protect communications, safeguard mission-critical applications and prevent threats. Cybersecurity is important to governments, where it is increasingly seen as an area of international conflict. Most countries have now setup their dedicated national cybersecurity centres, drawing on the capabilities of private industry, government and academic specialists in the area.
As cybersecurity threats have proliferated and computer technology has advanced, government data security compliance has become increasingly complex. The governments of various nations have set up compliances with a wave of new privacy regulations.
Security is an ongoing and constant effort which should be adopted at an individual, business, organisation, enterprise and national level. To strengthen cybersecurity there are many excellent solutions, a range of comprehensive suites and products. However, malicious parties and criminals are constantly employing new techniques and technologies. It is a new arms race, and there is no one size fits all solution.






