Trust in the Banking, Financial Services, and Insurance (BFSI) industry is critical – and this amplifies the value of stolen data and fuels the motivation of malicious actors. Ransomware attacks continue to escalate, underscoring the need for fortified backup, encryption, and intrusion prevention systems. Similarly, phishing schemes have become increasingly sophisticated, placing a burden on BFSI cyber teams to educate employees, inform customers, deploy multifactor authentication, and implement fraud detection systems. While BFSI organisations work to fortify their defences, intruders continually find new avenues for profit – cyber protection is a high-stakes game of technological cat and mouse!
Some of these challenges inherent to the industry include the rise of cryptojacking – the unauthorised use of a BFSI company’s extensive computational resources for cryptocurrency mining.
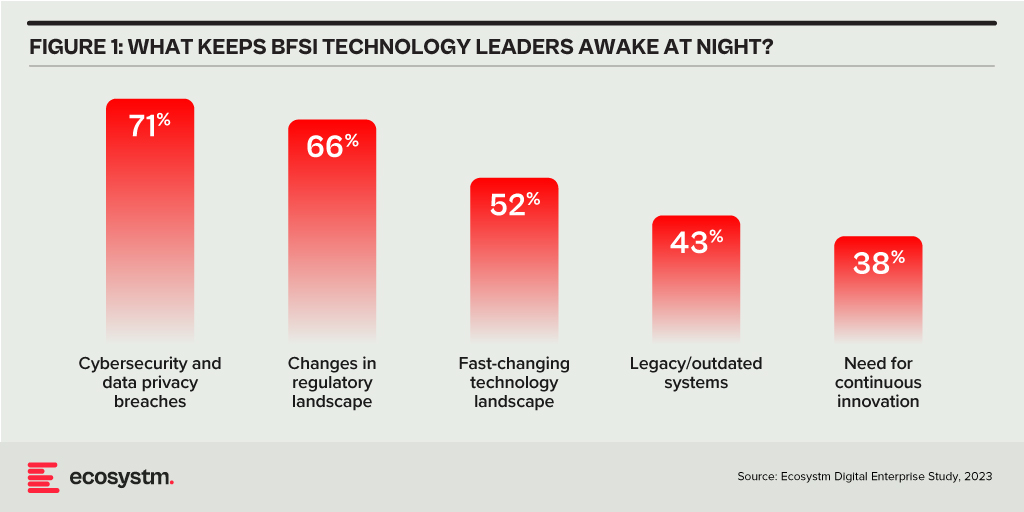
Building Trust Amidst Expanding Threat Landscape
BFSI organisations face increasing complexity in their IT landscapes. Amidst initiatives like robo-advisory, point-of-sale lending, and personalised engagements – often facilitated by cloud-based fintech providers – they encounter new intricacies. As guest access extends to bank branches and IoT devices proliferate in public settings, vulnerabilities can emerge unexpectedly. Threats may arise from diverse origins, including misconfigured ATMs, unattended security cameras, or even asset trackers. Ensuring security and maintaining customer trust requires BFSI organisations to deploy automated and intelligent security systems to respond to emerging new threats.
Ecosystm research finds that nearly 70% of BFSI organisations have the intention of adopting AI and automation for security operations, over the next two years. But the reality is that adoption is still fairly nascent. Their top cyber focus areas remain data security, risk and compliance management, and application security.
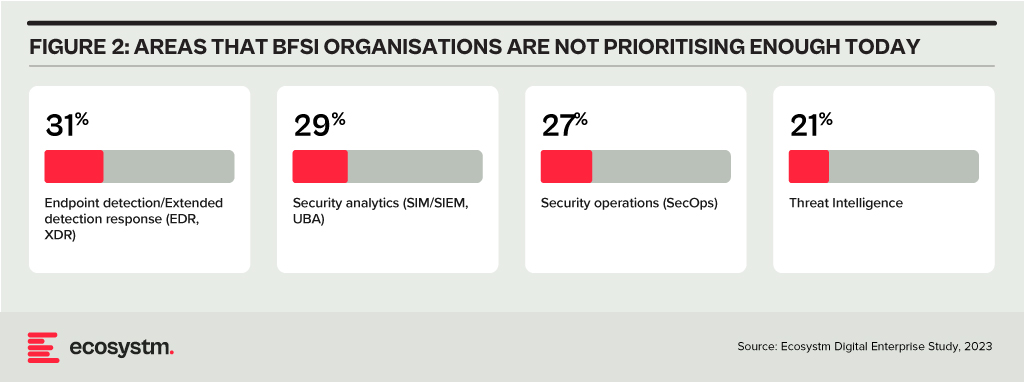
Addressing Alert Fatigue and Control Challenges
According to Ecosystm research, 50% of BFSI organisations use more than 50 security tools to secure their infrastructure – and these are only the known tools. Cyber leaders are not only challenged with finding, assessing, and deploying the right tools, they are also challenged with managing them. Management challenges include a lack of centralised control across assets and applications and handling a high volume of security events and false positives.
Software updates and patches within the IT environment are crucial for security operations to identify and address potential vulnerabilities. Management of the IT environment should be paired with greater automation – event correlation, patching, and access management can all be improved through reduced manual processes.
Security operations teams must contend with the thousands of alerts that they receive each day. As a result, security analysts suffer from alert fatigue and struggle to recognise critical issues and novel threats. There is an urgency to deploy solutions that can help to reduce noise. For many organisations, an AI-augmented security team could de-prioritise 90% of alerts and focus on genuine risks.
Taken a step further, tools like AIOps can not only prioritise alerts but also respond to them. Directing issues to the appropriate people, recommending actions that can be taken by operators directly in a collaboration tool, and rules-based workflows performed automatically are already possible. Additionally, by evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where security operations are completely automated.
Threat Intelligence and Visibility for a Proactive Cyber Approach
New forms of ransomware, phishing schemes, and unidentified vulnerabilities in cloud are emerging to exploit the growing attack surface of financial services organisations. Security operations teams in the BFSI sector spend most of their resources dealing with incoming alerts, leaving them with little time to proactively investigate new threats. It is evident that organisations require a partner that has the scale to maintain a data lake of threats identified by a broad range of customers even within the same industry. For greater predictive capabilities, threat intelligence should be based on research carried out on the dark web to improve situational awareness. These insights can help security operations teams to prepare for future attacks. Regular reporting to keep CIOs and CISOs informed of the changing threat landscape can also ease the mind of executives.
To ensure services can be delivered securely, BFSI organisations require additional visibility of traffic on their networks. The ability to not only inspect traffic as it passes through the firewall but to see activity within the network is critical in these increasingly complex environments. Network traffic anomaly detection uses machine learning to recognise typical traffic patterns and generates alerts for abnormal activity, such as privilege escalation or container escape. The growing acceptance of BYOD has also made device visibility more complex. By employing AI and adopting a zero-trust approach, devices can be profiled and granted appropriate access automatically. Network operators gain visibility of unknown devices and can easily enforce policies on a segmented network.
Intelligent Cyber Strategies
Here is what BFSI CISOs should prioritise to build a cyber resilient organisation.
Automation. The volume of incoming threats has grown beyond the capability of human operators to investigate manually. Increase the level of automation in your SOC to minimise the routine burden on the security operations team and allow them to focus on high-risk threats.
Cyberattack simulation exercises. Many security teams are too busy dealing with day-to-day operations to perform simulation exercises. However, they are a vital component of response planning. Organisation-wide exercises – that include security, IT operations, and communications teams – should be conducted regularly.
An AIOps topology map. Identify where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of threats, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
A trusted intelligence partner. Extend your security operations team by working with a partner that can provide threat intelligence unattainable to most individual organisations. Threat intelligence providers can pool insights gathered from a diversity of client engagements and dedicated researchers. By leveraging the experience of a partner, BFSI organisations can better plan for how they will respond to inevitable breaches.
Conclusion
An effective cybersecurity strategy demands a comprehensive approach that incorporates technology, education, and policies while nurturing a culture of security awareness throughout the organisation. CISOs face the daunting task of safeguarding their organisations against relentless cyber intrusion attempts by cybercriminals, who often leverage cutting-edge automated intrusion technologies.
To maintain an advantage over these threats, cybersecurity teams must have access to continuous threat intelligence; automation will be essential in addressing the shortage of security expertise and managing the overwhelming volume and frequency of security events. Collaborating with a specialised partner possessing both scale and experience is often the answer for organisations that want to augment their cybersecurity teams with intelligent, automated agents capable of swiftly

Privileged accounts are gold mines for malicious actors. They offer persistent access to valuable corporate resources and pose massive risk to organisations. Once authentication has been breached and credentials are obtained by an adversary, moving laterally, and accessing multiple resources, is too easy.
The most privileged access is not always granted to the most senior employees. Administrative and personal assistants often have the greatest access to corporate resources. They are low hanging fruit for attackers -usually among the least well-prepared to deal with breaches or attacks like phishing emails. Privilege promiscuity like this creates challenges around not only Privileged Access Management (PAM), but also other digital risk controls.
Scaling PAM is Complex
Think of PAM as a way of stopping people from abusing privilege. Imagine that you need a handyman for some repairs. The handyman is granted access to your house through the front door and is guided to the kitchen. The handyman is monitored and exits the kitchen as soon as the job is completed. The handyman then leaves the house. The worst outcome is a shoddy job or perhaps the theft of small pieces of cutlery or a few fridge magnets. In other words, the handyman’s access has been managed and privilege was only granted as needed. This is good PAM.
Bad PAM is a scenario where the handyman is granted access to your home and nobody is in to monitor the handyman’s activities. The handyman could be honest do the job and then depart. But, there is a significant risk that the handyman takes advantage of the privileged access granted. The handyman has access to all the rooms in the house and all the items in the house. The handyman can invite other people into the house, including a friend who can remove and copy data from all resident hard drives in the house. This access enables the handyman to steal credit cards, jewelry, PII, credentials and more.
Now, imagine that there are hundreds of handymen and other workers entering and exiting a house at varying times and for different purposes – each with distinct tasks and a need for access to different rooms and items, 24/7. This is the challenge faced by security operations – there are often hundreds or thousands of users with differing privileges to manage. Organisations are struggling to keep up with the sheer scale of the PAM challenge with all its moving parts. PAM also needs to consider the ongoing change in roles and responsibilities of staff, which directly impacts requirements for privileged access.
Privilege Sprawl and Privilege Overkill is Rife In Asia
Once an adversary breaches a privileged account, and is able to move laterally, they can access email accounts, intellectual property, employee data, customer data, sales data, invoicing approvals, expense approvals, and many other systems and processes. In addition to being exposed to short-term financial risk, an organisation also faces operational, legal, and reputational risk from such a breach. The attacker can unload ransomware or other malware to sabotage operations. They can steal PII and credentials, to sell them or use them to cause reputational and legal damage to the victim.
Privilege sprawl is common in Asian organisations. IT departments often struggle to keep track of who has access to what. Worse, IT departments typically over-provision their stakeholders with access. They are usually more concerned with getting positive feedback for the IT resources they provide from the business, than in aggressive risk management.
Specialised PAM solutions have emerged to mitigate the risk associated with unauthorised account access. The term privileged access management is a bit of misnomer. Today’s organisations need to ensure that all access is managed correctly. With an expanding number of devices, bots and people accessing corporate resources, the scope of PAM solutions is much broader than managing privileged accounts alone.
A Zero Trust Approach to PAM is Necessary
Organisations need to take a zero trust approach to PAM. Just-in-time access (JITA) needs to become the norm, ending persistent privileged access. Access needs to be granted for the minimum amount of time with the minimum rights required, ending privilege promiscuity. Zero standing privilege needs to be the default state of systems and networks. Access must be denied as soon as necessary work is complete and only provisioned when needed again. This approach is needed for risk management but few organisations in Asia have achieved this goal. The sheer number of moving parts involved in such an exercise makes it particularly onerous – this is where PAM solutions play a role.
Here’s a list of Ecosystm’s top five predictions that will affect enterprises, cybersecurity leaders, remote workers and the security posture in 2021. Signup for Free to download the report.




