Over the past 3-4 weeks I have spent some time using Samsung DeX (shortened from “Desktop eXperience”) as my primary desktop environment. DeX has been around for a number of years, and I have dabbled with it from time-to-time – but I have never really taken it seriously. My (incorrect!) opinion was that a mobile chipset isn’t powerful enough for a PC-like experience. But for most of the last year, I have been using a Samsung Galaxy Book S laptop as my primary computing device – and this Windows 10 laptop runs an ARM processor which is the very same processor that powers many Samsung and other Android phones. Microsoft also has an ARM-based PC that I have used successfully (the Surface Pro X) which prompted me to rethink the opportunities for DeX. A number of clients also asked for my thoughts on DeX so I figured it is time to take it seriously as a potential end-user computing environment.
This Ecosystm Insight is a summary of the client report and is the first of a few Insights into DeX. In future, I plan to trial the dual-monitor ability for DeX (developed by VoIP – an Australian ICT consultancy). These Ecosystm Insights won’t cover how to use Samsung DeX. If you are looking for this information, Gizmodo has published a good piece here.
The Trial
In trialling Samsung DeX I attempted to cover all usage scenarios, including:
- Native DeX with the phone connected to a DeX station and both wired and wireless keyboard/mouse, using both wi-fi and 4G (I live literally 50 metres outside of 5G coverage!)
- DeX through Windows 10 using both wi-fi and 4G and a wired mouse and keyboard
- Native DeX connected to a monitor using the Microsoft wireless display adapter (again using both wi-fi and 4G)
In the native DeX environment I worked in the traditional Microsoft productivity apps, collaboration apps (such as Teams, Zoom, Webex, Google Meet), Google productivity apps, web applications (sales, CRM & ERP), file sharing applications (OneDrive, Google Drive), imaging applications (photos, video, image sharing), social applications (Twitter, LinkedIn, Facebook, Instagram etc) and other native Android apps – some of which were optimised for DeX, and some of which were not. I tried to imitate the information worker’s experience; and that of a site or specialist user. I used it as a primary computing environment for most of my work for 3-4 weeks. I didn’t just consume content, but also created content – I needed to be able to sign and attach Adobe documents, create new reports, conduct deep data analysis in Excel and create figures and move them between Excel, Word and PowerPoint. I created and shared leads in CRM systems, did company accounting in a financial application and even had some time to try out some gaming applications.
I have also trialled a Citrix and Amazon virtual desktop in all environments – running productivity applications, finance applications, graphics intensive applications and web apps.
Findings
My broad finding is that DeX is not a desktop replacement for power users – but there are plenty of roles within your business who would find that DeX is a capable environment that will allow them to get their job done.
I was planning to discuss the positive features of DeX, but the reality is that it is simpler to understand its limitations. And, most limitations are related to the Android applications or network lag introduced in virtual desktop environments using 4G.
- The Microsoft productivity applications in Android are all scaled back versions of the desktop applications. They do not contain many of the features and functions that the desktop versions have. For example, when I needed to format headings in a report, the fast format options (e.g. to make text a “heading 2”) don’t exist in the Android version of Microsoft Word. Power users will find these applications don’t deliver all of the functions they need to get their job done.
- Those who need broader functionality beyond the Android applications will benefit from a virtual desktop environment. Both Citrix Workspace and Amazon Workspaces delivered a very usable Windows 10 experience (although I found the base configuration to be a little slow). For existing users of virtual desktops, it is a no-brainer to roll them out to mobile devices if required. But would you add a virtual desktop environment to your existing desktop fleet just to enable DeX? I can’t answer that – as it is another environment to manage and support for your end-user computing and IT support teams. But again, for power users, this is not an ideal environment. It does EVERYTHING you want it to do – but it might not do it fast enough to satisfy all users.
- It’s not a mobile environment. This isn’t something you use on your phone (although I believe you can use it on some Samsung tablets). You need a monitor, keyboard, and ideally a separate mouse for DeX to work. It doesn’t replace a laptop for a mobile worker.
- DeX does not natively support dual screens or monitors. I found that I would switch back to my PC when I needed the productivity of two screens, as I personally find application switching on a single screen to be a productivity killer. BUT – this is changing – VoIP has developed a capability to run DeX across dual monitors (I will be testing this shortly and will post the results).
- When using DeX natively and not using a virtual desktop, the screen sharing features of collaboration apps don’t work in the way you expect. The screen that is shared is NOT the DeX desktop screen but the horizontal mobile phone screen. This is a significant issue if you want to share a Word, PowerPoint, or Excel file or another “full desktop screen” application. DeX users can view other people’s shared screens, but not share the screen effectively themselves.
- DeX introduces a new environment for your helpdesk to support. DeX isn’t Windows, it isn’t cloud, and it isn’t exactly native Android. Your tech support team will need to be trained on DeX and be required to learn a new user environment. It introduces an additional OS into the mix. That means at least some service desk technicians will need to be trained on the environment. As it is still running in Android, it doesn’t particularly require specific QA or testing for your business mobile applications. But to take full advantage of the larger screen real estate that DeX facilitates, you may need to make some changes to how applications perform in DeX.
Despite these challenges, DeX is a very capable environment. Running a virtual desktop was a breeze and performed far better than I would have imagined. I was worried about lag and had introduced many opportunities for it to run slowly – a wireless mouse and keyboard, wireless display adapter, running over wi-fi, and 4G using a virtual desktop in the cloud – and the lag was barely noticeable. I was impressed with this and understand how DeX could even be used to support legacy applications and environments too.
The convenience of having your phone at your fingertips – being able to respond to text messages on the large screen, taking calls using the same Bluetooth headphones that you use to watch video content on the larger screen, not to mention the security of taking your “PC” with you in your pocket when you head out to lunch or home for the day – adds to the value of DeX. The concept of a “PC in your pocket” has been around for a while – however most Samsung mobile users don’t realise that they have one there already!
Target Roles

Who are the business roles or personas who could benefit from it? The simple answer is that anyone who uses a desktop part-time would benefit from DeX. Many businesses have shared PCs for multiple users or dedicated PCs for users who don’t use a PC full-time. These might be site managers in constriction, store managers in retail, nurses, security staff, librarians, government or council workers. The significant factors that define potential DeX users are:
- They spend a fair amount of time away from a PC
- They still need a PC for reporting, document sharing, content creation etc
- They return to a fixed site regularly (like a store, office, site office etc)
Again, it is worth noting that DeX doesn’t replace a laptop or tablet. It is not for mobile computing – it replicates fixed computing environments in a more mobile and potentially cost-effective form factor. Remember that the employees need a screen, mouse, and keyboard (you can use the phone as a mouse, but it is not ideal). They also need the charging cable to connect to the computer. If they are making regular video calls then I suggest a phone holder that allows the charging cable to stay connected and the phone to be angled so as others can see their face (wireless chargers tend to sit too far back).
And while DeX is a secure solution, and can benefit from Samsung’s Knox security platform and capabilities, pairing DeX with a secure branch of one style solution – such as that offered by Asavie, now a part of Akamai – has the ability to add end-to-end security and secure application/data access that your employees desire and your business needs.
The opportunities for DeX outweigh the challenges. I am certain that most businesses have potential DeX users – employees who reluctantly carry around a laptop, or who have to come back to a location for their computing. They might be employees who use their phones for image capture and spend much of their time transferring photos to a PC to store them into a corporate system (such as an OH&S team member, or a repair and maintenance provider for a company). It could be a brand salesperson who spends time in various retailers or on the road but still need computing for product training, entering sales figures, and other administrative tasks.
If your business already offers Samsung devices to your employees, switching on DeX is a no-brainer. Start with a trial in a limited employee pool to determine the specific challenges and opportunities within your business. If you are already using virtual desktops, then this is the easiest way to start – roll out the app to your Samsung mobile devices and you have a ready-made portable computer in your employees’ pockets.
Ecosystm recently partnered with Asavie to conduct a study on the opportunity and outlook for the “Branch of One“. The results of the study make us question whether organisations’ mobile security strategies are appropriate for the evolving business priorities, the ever-changing threat landscape, and a seamless employee experience.
To answer this question, organisations will need to examine their security frameworks.
COVID-19 has forced organisations to realise that cybersecurity is not only a business enabler – it is a business prerequisite. Our research shows that businesses world-wide no longer see the pandemic as something that we need to get through to get back to “business as usual”. Most acknowledge that remote working and access from anywhere will be the new normal for many employees and that means they need to revisit and reprioritise their spending and their focus.
In many cases, existing procedures and policies are not sufficient to cover this new working environment – and often the policies have not been clearly communicated to all employees. Moreover, many organisations still rely on legacy WAN technologies that make secure and flexible access difficult – something that my colleague, Tim Sheedy touched upon in his recent blog post.
The choice of WAN technology is an important part of any mobile security strategy, but so is the approach to securing endpoints on the WAN and – what is perhaps the weakest link – the behaviour of employees.
The Global CxO Study 2020: The Future of Secure Office Anywhere showed us that when it came to mobile security, organisations were mostly worried about phishing and malware – but 4 out of the top 5 mobile security concerns involved human error and failure to follow corporate IT security policies and guidelines (Figure 1).
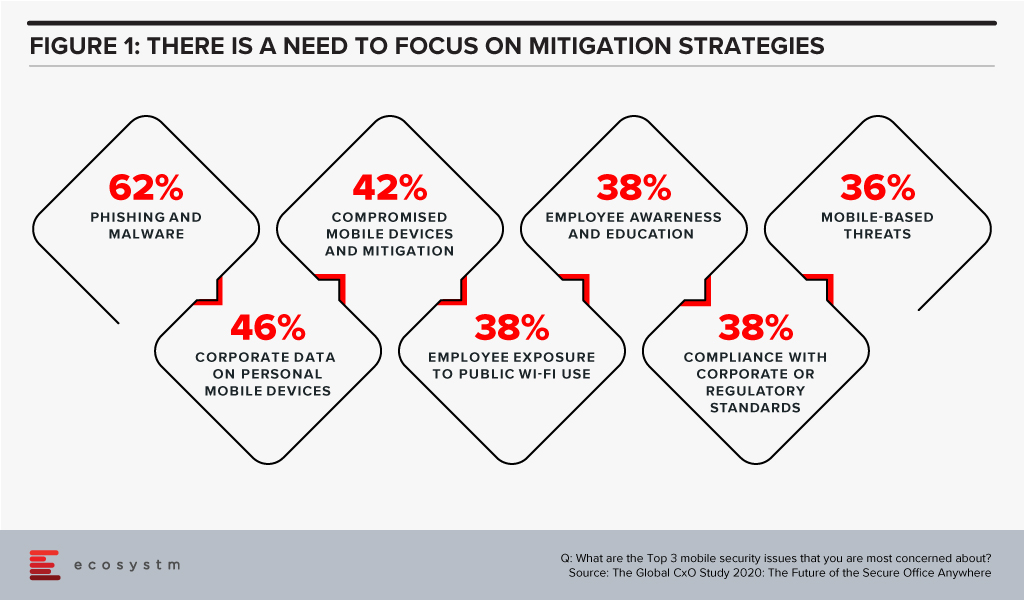
Time to Evaluate New Mobile Security Features
This highlights the importance of a couple of “security features” that many IT organisations still tend to overlook – convenience and ease-of-use. When employees ignore IT policies, bypass security steps, use unsanctioned personal devices to process work data etc., they tend to do so for mainly one reason: because it is convenient for them. Employees just want to get the work done and following security protocols, making sure that devices have the right security software installed etc. is simply seen as too cumbersome or as slowing down the work process.
To counter this, ease-of-use and convenience need to an integral part of any security framework – especially when employees are no longer working in the office. IT managers tend to be a bit ego-centric when they think of these terms, i.e. for them ease-of-use relates to their experience in implementing and running the systems, but they really need to be extending the ease to their users – the employees – as well.
This is where Branch of One comes to the fore. It offers the convenience of employees not having to install or connect software or hardware on the mobile device and it allows administrators to easily scale and manage their mobile security framework. Security frameworks do not have to be in the way of getting the work done. Branch of One shows us that comprehensive mobile security can be nearly seamless.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

Ecosystm recently partnered with Asavie to conduct a study into the opportunity and outlook for the “Branch of One”. One of the challenges was actually defining what the Branch of One is. Here’s what we came up with:
Branch of One enables Office Anywhere by delivering secure, frictionless access to all business resources, with full mobility – meeting the security and manageability requirements of CIOs and CISOs.
Basically it is all the data and systems you need to get your job done, in your pocket. Secure. Easy to manage.
What I really like about the idea is that it describes what business is trying to achieve and it gives a common language and outcome for IT and business leaders. Consider all the things that IT and security teams need to do to enable access to applications and data in remote branches – from connectivity to security to data and system access. Often it takes days, weeks or months to open a new office or branch, or to provision a new retail store. Now, imagine having the ability to roll out all of these systems and services in seconds. To a single user or to thousands. Without consideration for location. Business leaders will understand this benefits and will support it.
It also has the opportunity to help nearly every business today. Of the 1005 businesses we interviewed across the globe in our Global CxO Study 2020, 44% admitted to suffering cyber-attack incidents during COVID-19 due to employees working from home – and over half of these attacks were on mobile devices. Compromised devices were the number one target for cyber-attacks in 2020.
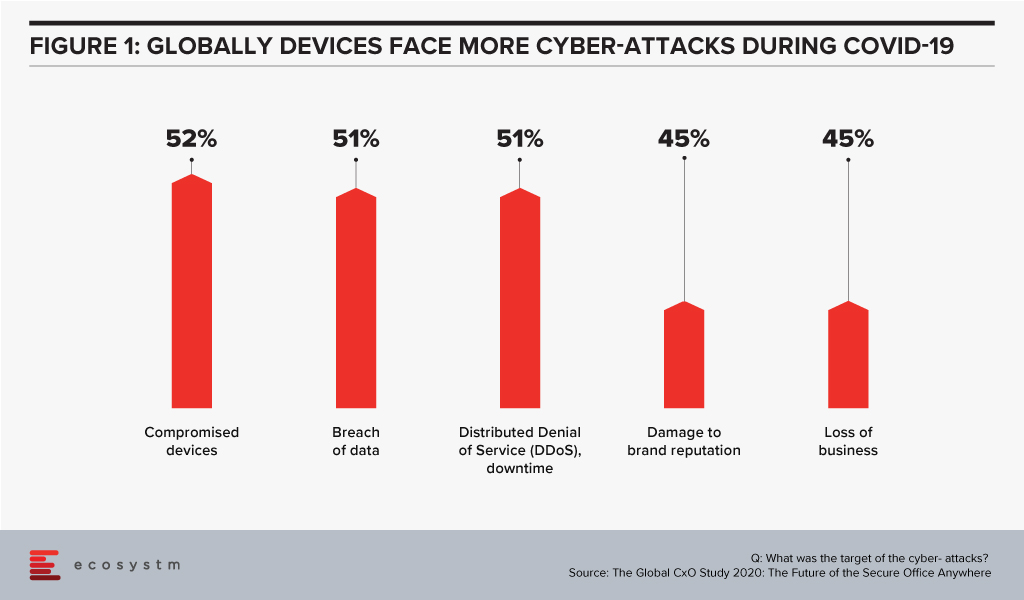
Businesses need a new way to manage the devices and applications of their remote employees. They need to be able to extend the benefits of the WAN to them without the downsides of VPNs. Every business we interviewed saw benefits of bringing devices, locations and offices inside the WAN. Turning every device and office into a Branch of One.
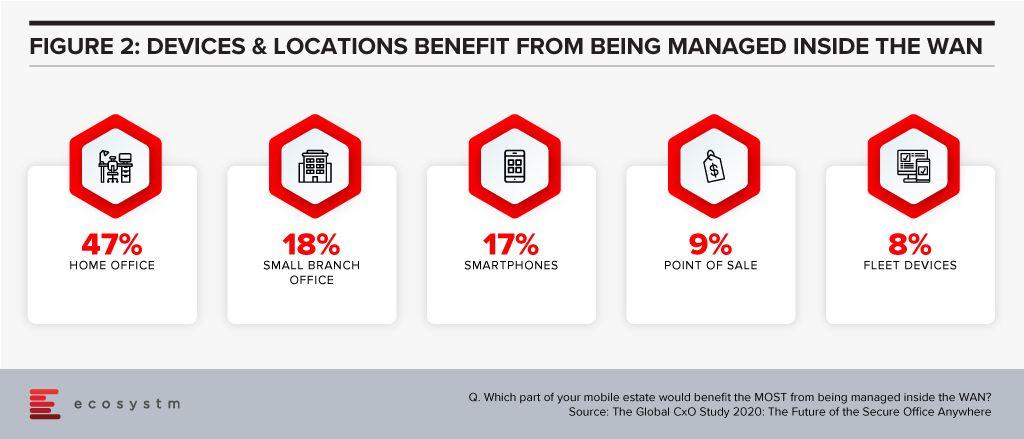
A few security and network technologies have promised this capability – SDNs can offer a similar service, but they require client software to be installed. 78% of businesses we interviewed are using VPNs to bring devices inside the WAN – but again, they require client software, and can be inconsistent (and insecure!) on mobile devices.
Companies that embrace the Branch of One can provision new users in a few clicks. No software to install, no cables to connect, no hardware to provision – it makes life easier for technology and security professionals. The Branch of One gives your employees the systems and data they need to get their job done – delivered securely across the mobile network.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

Ecosystm research finds that 47% of organisations re-evaluated cybersecurity risks and management making it the biggest measure undertaken by IT Teams when COVID-19 hit. There is no denying any more that cybersecurity is a key business enabler. This year witnessed cybercrime escalating in all parts of the world and several governments issued advisories warning enterprises and citizens of the increase in the threat landscape, during and post COVID-19. Against this backdrop, Ecosystm Advisors, Alex Woerndle, Andrew Milroy, Carl Woerndle and Claus Mortensen present the top 5 Ecosystm predictions for Cybersecurity & Compliance in 2021.
This is a summary of the predictions, the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Cybersecurity & Compliance Trends for 2021
- There will be Further Expansion of M&A Activities Through 2021 and Beyond
As predicted last year, the market is set to witness mergers and acquisitions (M&As) to consolidate the market. The pandemic has slowed down M&A activities in 2020. However, the market remains fragmented and there is a demand for consolidation. As the cyber market continues to mature, we expect M&A activities to ramp up over the next couple of years especially once we emerge from COVID-19. Some organisations that understand the full impact of the shift to remote working and the threats it creates have embraced the opportunity to acquire, based on perceived value due to COVID-19. The recent acquisition of Asavie by Akamai Technologies is a case in point. Asavie’s platform is expected to strengthen Akamai’s IoT and mobile device security and management services.
- After a Year of Pandemic Leniency, Regulators will Get Stricter in 2021
The regulators in the EU appear to have gone through a period of relative leniency or less activity during the first few months of the pandemic and have started to increase their efforts after the summer break. Expect regulators – even outside the EU – to step up their enforcement activities in 2021 and seek larger penalties for breaches.
Governments continue to evolve their Compliance policies across broader sectors, which will impact all industries. As an example, in Australia, the Federal Government has made changes to its definition of critical infrastructure, which brings mandates to many more organisations. Governments have shown an acute awareness of the rise in cyber-attacks highlighted by several high-profile breaches reported in mainstream media. Insider threats – highlighted by Tesla, where an employee raised the allegations of bribery by unknown third parties in exchange for exfiltrating corporate information – will also lead regulators to double down on their enforcement activities.
- The Zero Trust Model Will Gain Momentum
Remote working has challenged the traditional network security perimeter model. The use of personal and corporate devices to access the network via public networks and third-party clouds is creating more opportunity for attackers. Organisations have started turning to a Zero Trust security model to mitigate the risk, applying advanced authentication and continuous monitoring. We expect the adoption of the Zero Trust model to gain momentum through 2021. This will also see an increase in managed services around active security monitoring such as Threat Detection & Response and the increased adoption of authentication technologies. With an eye on the future, especially around quantum computing, authentication technologies will need to continually evolve.
- The Endpoint Will be the Weakest Link
The attack surface continues to grow exponentially, with the increase in remote working, IoT devices and multicloud environments. Remote endpoints require the same, if not higher levels of security than assets that sit within corporate firewalls, and it will become very clear to organisations that endpoints are the most vulnerable. Remote workers are often using unsecure home Wi-Fi connections and unpatched VPNs, and are increasingly vulnerable to phishing attacks. IoT device passwords are often so weak that brute-force attackers can enter networks in milliseconds.
Although endpoint security can be dealt with through strict policies together with hardware or software authentication, the difficult part is to adopt an approach that retains a relatively high level of security without having a too negative an impact on the employee experience. Experience shows that if the security measures are too cumbersome, employees will find ways to circumvent them.
- Hackers Will Turn the Table on AI Security
Cybersecurity vendors are increasingly offering solutions that leverage AI to identify and stop cyber-attacks with less human intervention than is typically expected or needed with traditional security approaches. AI can enhance cybersecurity by better predicting attacks enabling more proactive countermeasures, shortening response times, and potentially saving cybersecurity investment costs. The problem is that the exact same thing applies to the hackers. By leveraging AI, the costs and efforts needed to launch and coordinate large hacker attacks will also go down. Hackers can automate their attacks well beyond the use of botnets, target and customise their attacks with more granularity than before and can effectively target the biggest weakness of any IT security system – people.
Already, phishing attacks account for many of the breaches we see today typically by employees being tricked into sharing their IT credentials via email or over the phone. As we move forward, these types of attacks will become much more sophisticated. Many of the deepfake videos we see have been made using cheap or free AI-enabled apps that are easy enough for even a child to use. As we move into 2021, this ability to manipulate both video and audio will increasingly enable attackers to accurately impersonate individuals.






