A lot gets written about cybersecurity – and organisations spend a lot on it! Ecosystm research finds that 63% of organisations across Asia Pacific are planning to increase their cyber budget for the next year. As budgets continue to rise, the threat landscape continues to get more complex and difficult to navigate. Despite increasing spend, 69% of organisations believe a breach is inevitable. And breaches can be EXPENSIVE! Medibank, in Australia, was breached in (or around) October, 2022. The cost of the breach is expected to reach around USD 52 million when everything is done and dusted – and this does not include the impacts of any potential findings or outcomes from regulatory investigations or litigation.
Recovering Strong
While cybersecurity is still crucially important, the ability to recover from breaches quickly and cost-effectively is also imperative. How you recover from a breach will ultimately determine your organisation’s long-term viability and success. The capabilities needed to recover quickly include:
- A well-documented and practices incident response plan. The plan should outline the roles and responsibilities of all team members, communication protocols, and steps to be taken in the event of a breach.
- Backup and Disaster Recovery (DR) solutions. Regular backups of critical data and systems are essential to quickly recover from a breach. Backup solutions should include offsite or cloud-based options that are isolated from the main network. DR solutions ensure that critical systems can be quickly restored and made operational after a breach.
- Cybersecurity awareness training. Investing in regular training for all employees is crucial to ensure they are aware of the latest threats and know how to respond in the event of a breach.
- Automated response tools. Automation can help speed up the response time during a breach by automatically blocking malicious IPs, quarantining infected devices, or taking other predefined actions based on the nature of the attack.
- Threat intelligence. This can help organisations stay ahead of the latest threats and vulnerabilities and frame quicker responses if a breach occurs.
Backup and Disaster Recovery is Evolving
Most organisations already have backup and disaster recovery capabilities in place – but too often they are older systems, designed more as a “just in case” versus a “will keep us in business” capability. Backup and DR systems are evolving and improving – and with the increased likelihood of a breach, it is a good time to consider what a modern Backup and DR system can provide to your organisation. Here are some of the key trends and considerations that technology leaders should be aware of:
- Cloud-based solutions. More organisations are moving towards cloud-based backup and DR solutions. Cloud solutions offer several advantages, including scalability, cost-effectiveness, and the ability to access data and systems from anywhere. However, technology leaders need to consider data security, compliance requirements, and the reliability of the cloud service provider.
- Hybrid options. As hybrid cloud becomes the norm for most organisations, hybrid solutions backup and DR that combine on-premises and cloud-based backups are becoming more popular. This approach provides the best of both worlds – the security and control of on-premises backups with the scalability and flexibility of the cloud.
- Increased use of automation. Automation is becoming more prevalent in backup and DR solutions. Automation helps reduce the time it takes to backup data, restore systems, and test DR plans. It also minimises the risk of human error. Technology leaders should look for solutions that offer automation capabilities while also allowing for manual intervention when necessary.
- Cybersecurity integration. With the rise of cyberattacks, especially ransomware, it is crucial that backup and DR solutions are integrated with an organisation’s cybersecurity strategy. Backup data should be encrypted and isolated from the main network to prevent attackers from accessing or corrupting it. Regular testing of backup and DR plans should also include scenarios where a cyberattack, such as ransomware, is involved.
- More frequent backups. Data is becoming more critical to business operations, so there is a trend towards more frequent backups, even continuous backups, to minimise data loss in the event of a disaster. Technology leaders need to balance the need for frequent backups with the cost and complexity involved.
- Super-fast data recovery. Some data recovery platforms can recover data FAST – in as little as 6 seconds. The ability to recover data faster than the bad actors can delete it makes organisations less vulnerable and buys more time to plug the gaps that the attackers are exploiting to gain access to data and systems.
- Monitoring and analytics. Modern backup and DR solutions offer advanced monitoring and analytics capabilities. This allows organisations to track the performance of their backups, identify potential issues before they become critical, and optimise their backup and DR processes. Technology leaders should look for solutions that offer comprehensive monitoring and analytics capabilities.
- Compliance considerations. With the increasing focus on data privacy and protection, organisations need to ensure that backup and DR solutions are compliant with relevant regulations, often dictated at the industry level in each geography. Technology leaders should work with their legal and compliance teams to ensure that their backup and DR solutions meet all necessary requirements.
The sooner you evolve and modernise your backup and disaster recovery capabilities, the more breathing room your cybersecurity team has, to improve the ability to repel threats. New security architectures and postures – such as Zero Trust and SASE are emerging as better ways to build your cybersecurity capabilities – but they won’t happen overnight and require significant investment, training, and business change to implement.

There are two types of organisations – those that know that they have had a cybersecurity breach and those that don’t. With ransomware accounting for a rapidly growing proportion of breaches, not knowing you have been breached is less likely. In the last two months, we have seen a series of devastating ransomware attacks. These have included attacks on critical infrastructure, Colonial Pipeline and JBS, and the more recent supply chain attack on Kaseya, infecting its customers’ customers with ransomware. We’ve also seen an increase in attacks on soft targets such as schools and hospitals.
What is ransomware? Well, it’s a type of malware that specialises in encrypting the victim’s data and demands a ransom for a decryption key which may or may not work. If the victim fails to pay, their data could be sold or published online. More worryingly, if the victim pays, their data could still be sold or published online, prolonging the agony. Common ransomware families include REvil, Locky, Wannacry, Cerber, NotPetya, Maze and Darkside.
Why is Ransomware Becoming more Widespread?
Increased digitisation, remote working, accelerated adoption of cloud computing and growth in IoT devices, have expanded the attack surface for threat actors – offering more vulnerabilities that can be exploited. Launching a ransomware attack is a relatively easy and low-risk way to make money for cyber-criminals. Threat actors are usually outside the jurisdiction where the attack takes place and are typically protected by the absence of extradition treaties between the country where the crime occurred and the country from where the attack was launched. As well as posing a remarkably low risk to the attacker the rewards from a successful ransomware attack are potentially very large. Ransomware as a service (RaaS) kits can be purchased on the dark web for a few hundred dollars and if used repeatedly are likely to find at least one victim. Cryptocurrencies such as bitcoin make it virtually impossible for law enforcement authorities to track ransom payments. Consequently, the rapid growth in ransoms combined with the increasing risk of successful ransomware attacks is leading to banks stocking up on bitcoin. This allows their customers to quickly pay ransoms.

How to Mitigate the Risks?
Companies will not be able to completely eliminate the risk of ransomware attacks. They can, however, mitigate the risk of these attacks with a zero-trust approach to cybersecurity, renewed focus on training and awareness programs, and well-prepared and rehearsed incident response plans.
Rigorously applying the principle of least privilege will make it harder for threat actors to gain the credentials that they need to move laterally within systems and networks. Segmenting networks and isolating workloads will limit the blast radius of attacks. Training and awareness campaigns will make employees less likely to download malware via phishing attacks or other social engineering activities. Ensuring that all sensitive data is classified and encrypted will make double extortion more difficult – a miserable scenario where the victim pays a ransom for a decryption key and is then asked to pay a further ransom for the dubious promise that stolen data will not be leaked.
Protecting against supply chain ransomware attacks, such as the Kaseya breach, is fiendishly difficult. In the case of Kaseya, attackers identified a zero-day vulnerability in its VSA IT management and monitoring tool. An update was then infected with ransomware and shared with managed service providers, who, in turn infected their customers with the ransomware.
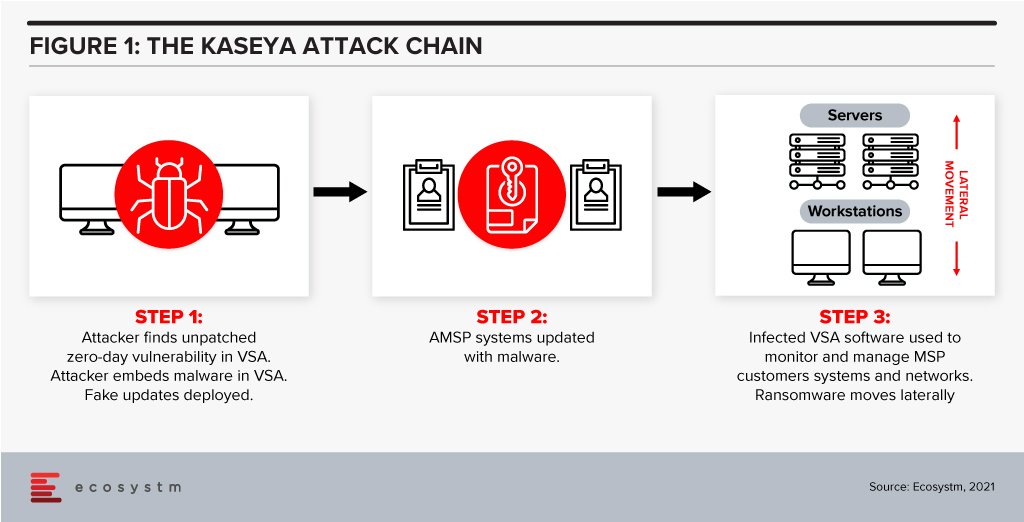
Rehearsed incident response plans that prepare for a successful ransomware attack are essential controls against such threats. A critical component of such a plan is backup and recovery. Backups are increasingly being targeted in well-orchestrated attacks so companies must find ways of ensuring that their data is stored in at least one immutable destination. This means that they can recover quickly – often almost instantly if the process is automated.
If companies follow cybersecurity best practices such as those outlined above, they should be able to manage ransomware risk and the misery associated with these attacks. If a ransomware attack occurs, well-prepared companies will be able to recover rapidly and be comfortable in the knowledge that the data which has been stolen is of little or no value to the attackers.




