Cyber operations become more complex with distributed company assets due to the hybrid work model; the need to revamp supply chains; and constantly monitor business continuity measures. And of course, 2021 has shown us that hackers are getting smarter and more vicious. Attacks now often originate from what appears to be trusted devices, people, applications – that reside inside the network. This will drive organisations to continue to focus on cybersecurity, and tech providers to develop on security by design in 2022.
Read on to find out what Ecosystm Analysts, Andrew Milroy and Claus Mortensen think will be the leading cybersecurity and compliance trends in 2022.

In recent times, there appears to be a shift in motive for cyber-attacks – along with common data theft, there is a proliferation of attacks aimed at the business interruption and physical incapacitation of business operations. We have witnessed an alarming increase in high-profile attacks on manufacturing businesses and critical infrastructure providers, globally.
This appears to be a global phenomenon. Honda manufacturing plants went offline in June after a cyber-attack compromised some of the Japanese automaker’s facilities. The same pattern emerged in a separate attack at the same time targeting Edesur S.A., a company belonging to the Enel Group that confirmed its internal IT network was disrupted due to a ransomware attack, which was caught by antivirus software before the malware could infect. Both companies had machines with Internet-accessible remote desktop servers, which is a favorite infection method among attackers nowadays. One of Australia’s largest brewers, Lion also faced a ransomware outbreak, last month. In Israel, it was reported that a cyber-attack very nearly poisoned the water supply with the attackers attempting to overload the water system with chlorine, and in recent days, a fire and explosion at an Iranian nuclear plant is suspected of being caused by cyber-attack.
These attacks highlight the need for appropriate investments in cybersecurity by companies and municipalities that own or operate critical infrastructure, properties (including places of public congregation, retailers and others) that are rapidly deploying a suite of operational technologies, and businesses in the manufacturing sector.
Operational Technology (OT) is the backbone of modern industrial operations and is a network of multiple computing systems that perform operations including production line management, operations control and industrial monitoring. OT can further include specific computing systems like industrial control systems (ICS) which is a collection of control systems used to operate and/or automate industrial processes. There are several types of ICSs, the most common of which are Supervisory Control and Data Acquisition (SCADA) systems, and Distributed Control Systems (DCS). With such industrial systems and smart end-user products connected by a common network, several vulnerabilities may appear.
In OT security, the focus is much less on information, but more on the industrial process that technology controls. Hence, availability and integrity are often more important than confidentiality. Any organisation employing OT should employ continual risk-based assessments of their cybersecurity posture to prioritise and tailor recommended guidelines and solutions to fit specific security, business, and operational requirements.
Why is OT More Vulnerable?
OT systems are versatile and can be found in all kinds of industrial settings and infrastructures like smart buildings, oil and gas, energy generation/distribution, mining, wastewater treatment/distribution, manufacturing, food production, consumer devices and transport. In fact, almost every business in 2020 has an element of IoT within their operations.
A big issue with OT is that a lot of the technology in place is over 20 years old and therefore was not designed to provide the security capabilities required to face cyber threats in 2020. Legacy technology often requires legacy hardware and software to support it – much of which is the end of life and unsupported by the vendors (for example, consider SCADA systems still reliant on Windows NT or older Unix based systems, which have not been supported by their vendors for many years).
OT systems have also been damaged as unintended side effects of problems starting in corporate networks that took advantage of increasing connectivity, proving clearly that the standard PCs that now form part of a typical organisation’s IT environment are in turn used to manage OT systems and become a major vector for such cyber-attacks.
When it comes to OT, safety and reliability are the primary concerns as attackers aim to disrupt the critical services industry and their customers rely upon them. Given the increasing propensity of connecting OT systems with corporate networks for ease of management and the growing use of IoT systems, the likelihood of such systems being affected by vulnerabilities exploitable over the network is increasing exponentially.
For almost every business – not just critical infrastructure providers – most technologies we deploy include connectivity to the internet. Not knowing what systems and external access to these systems that your business is introducing in its everyday technology investment create significant risks to the broader business operations.
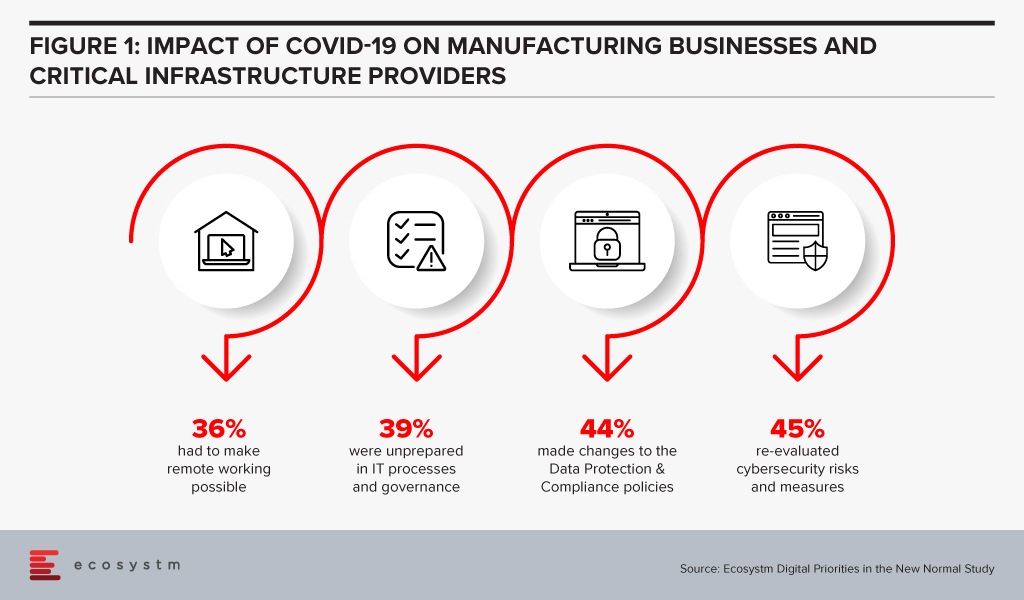
Manufacturing businesses and critical infrastructure providers realise that there is need to re-evaluate their cybersecurity measures, in the wake of the COVID-19 crisis, according to the findings of the Ecosystm’s ongoing “Digital Priorities in the New Normal” study (Figure 1).
But these measures may not be sufficient, as indicated by the slew of cyber-attacks on these organisations.
Why are these attacks successful?
There are several reasons why OT attacks are successful:
- Unauthorised access to internet-facing systems (e.g. deploying an IoT with the default username and password)
- Introduction of a compromised device (e.g. USB stick) to the environment that infects the network (often employee action)
- Exploitation of zero-day vulnerabilities in control devices and software
- Propagated malware infections within isolated computer networks (i.e. The attacker can place a receiving device to make contact over a channel that can propagate across the isolated network)
- SQL injection via exploitation of web application vulnerabilities
- Network scanning and probing
- Lateral movement (i.e. inadequate segmentation which results in attackers being able to move between systems, groups of systems, network zones and even geographical locations.)
How can they be prevented?
The mitigation cannot rely solely on the organisation building security around the deployment nor can it be a reactive approach to fixing vulnerabilities in production, as they are identified. It begins with the OT vendors building security within; however, as with most IT systems and applications, this will evolve over time. For example, there is an initiative in Australia – driven by the IoT Alliance Australia (IOTAA) – to introduce a ‘Trust Mark’ for IoT devices that pass a certification process for security and privacy in product development. This is targeted to launch in September 2020 but could take many years to gain real traction. Thus, for the foreseeable future, the best operational outcomes must be planned and managed by the consumers of the technologies.
Here are the best practices to reduce exploitable IoT weaknesses and attacks occurring in your business:
- Maintain an accurate inventory of Operational Systems and eliminate any exposure of these systems to external networks
- Establish clear roles and responsibilities for your organisation and your vendors, to ensure cybersecurity risk is being addressed and managed throughout the OT lifecycle
- Implement network segmentation and apply firewalls between critical networks and systems.
- Use secure remote access methods
- Establish Role-Based Access Controls (RBAC) and implement system logging
- Use only strong passwords, change default passwords, and consider other access controls (especially for any elevated privileges) such as multi-factor authentication, privileged access management solutions, etc.
- Establish threat intelligence feeds from your OT vendors and security vendors to ensure you remain abreast of new vulnerabilities, software/firmware patches and threats targeting systems you employ
- Develop and enforce policies on mobile devices, including strict device controls for any device connecting to OT systems or network zones
- Implement an employee cybersecurity training program
- Establish and maintain rigorous testing and patching program including vulnerability assessment and penetration testing
- Implement measures for detecting compromises and develop a cybersecurity incident response plan with a specific focus on responding to a disruptive attack on your OT environment
- Maintain an up-to-date Business Continuity Plan that can be deployed rapidly in response to a significant disruption

In the midst of the current global crisis, the Utilities industry has had to continue to provide essential public services – through supply chain disruption, reduction of demand in the commercial sector, demand spikes in the consumer sector, change in peak profiles, remote staff management, cyber-attacks and so on. Robust business continuity planning and technology adoption are key to the continued success of Utilities companies. The Ecosystm Business Pulse Study which aims to find how organisations are adapting to the New Normal finds that 6 out of 10 Utilities companies are accelerating or refocusing the Digital Transformation initiatives after the COVID-19 outbreak, underpinning the industry’s need for technology adoption to remain competitive.
Drivers of Transformation in the Utilities Industry
The Evolving Energy Industry. As consumers become more energy-conscious, many are making changes in their usage pattern to stay off the grid as much as possible, potentially reducing the customer base of Utilities companies. This increases their reliance on renewable energy sources (such as solar panels and wind turbines) and batteries, forcing Power companies to diversify and leverage other energy sources such as biomass, hydropower, solar, wind, and geothermal. The challenge is further heightened by the fast depletion of fossil fuels – it is estimated that the world will have run out of fossil fuels in 60 years. The industry is also mandated by government regulations and cleaner energy pacts that focus on climate change and carbon emission – there are strict mandates around how Utilities companies produce, deliver and consume energy.
Business Continuity & Disaster Management. Perhaps no other industry is as vulnerable to natural disasters as Utilities. One of the reasons why the industry has been better prepared to handle the current crisis is because their usual business requires them to have a strong focus on business continuity through natural disasters. This includes having real-time resource management systems and processes to evaluate the requirement of resources, as well as a plan for resource-sharing. There is also the danger of cyber-attacks which has been compounded recently by employees who have access to critical systems such as production and grid networks, working from home. The industry needs to focus on a multi-layered security approach, securing connections, proactively detecting threats and anomalies, and having a clearly-defined incident response process.
The Need to Upgrade Infrastructure. This has been an ongoing challenge for the industry – deciding when to upgrade ageing infrastructure to make production more efficient and to reduce the burden of ongoing maintenance costs. The industry has been one of the early adopters of IoT in its Smart Grid and Smart Meter adoption. With the availability of technology and advanced engineering products, the industry also views upgrading the infrastructure as a means to mitigate some of its other challenges such as the need to provide better customer service and business continuity planning. For example, distributed energy generation systems using ‘micro grids’ have the potential to reduce the impact of storms and other natural disasters – they can also improve efficiency and quality of service because the distance electricity travels is reduced, reducing the loss of resources.
The Evolving Consumer Profile. As the market evolves and the number of Energy retailers increases, the industry has had to focus more on their consumers. Consumers have become more demanding in the service that they expect from their Utilities provider. They are increasingly focused on energy efficiency and reduction of energy consumption. They also expect more transparency in the service they get – be it in the bills they receive or the information they need on outages and disruptions. The industry has traditionally been focused on maintaining supply, but now there is a need to evaluate their consumer base, to evolve their offerings and even personalise them to suit consumer needs.
The global Ecosystm AI study reveals the top priorities for Utilities companies, that are focused on adopting emerging technologies (Figure 1). It is noticeably clear that the key areas of focus are cost optimisation (including automating production processes), infrastructure management and disaster management (including prevention). 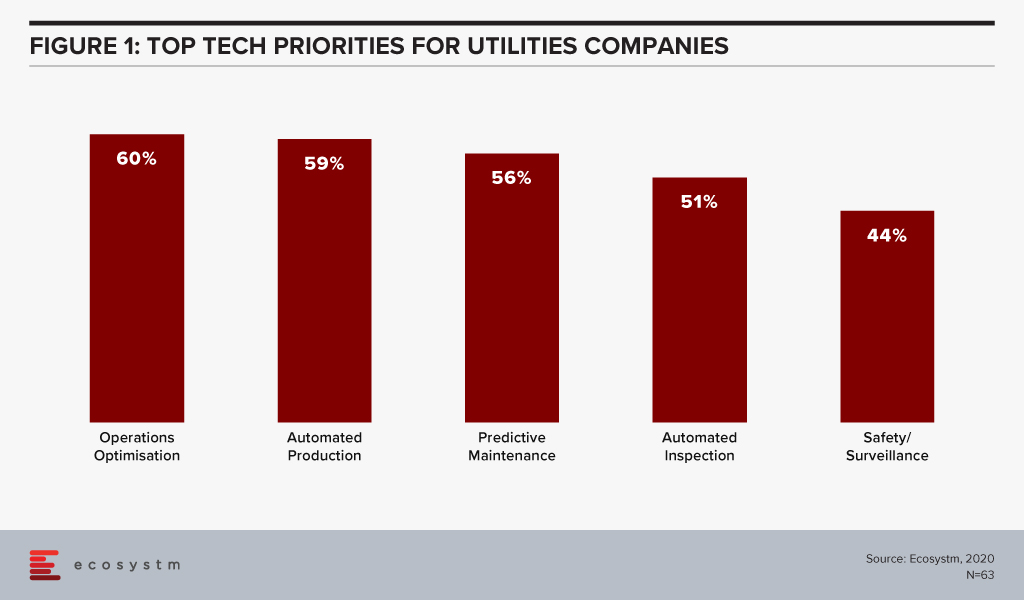
Technology as an Enabler of Utilities Sector transformation
Utilities companies have been leveraging technology and adopting new business models for cost optimisation, employee management and improved customer experience. Here are some instances of how technology is transforming the industry:
Interconnected Systems and Operations using IoT
Utilities providers have realised that an intelligent, interconnected system can deliver both efficiency and customer-centricity. As mentioned earlier, the industry has been one of the early adopters of IoT both for better distribution management (Smart Grids) and for consumer services (Smart Meters). This has also given the organisations access to enormous data on consumer and usage patterns that can be used to make resource allocation more efficient.
For instance, the US Government’s Smart Grid Investment Grant (SGIG) program aims to modernise legacy systems through the installation of advanced meters supporting two-way communication, identification of demand through smart appliances and equipment in homes and factories, and exchange of energy usage information through smart communication systems.
IoT is also being used for predictive maintenance and in enhancing employee safety. Smart sensors can monitor parameters such as vibrations, temperature and moisture, and detect abnormal behaviours in equipment – helping field workers to make maintenance decisions in real-time, enhancing their safety.
GIS is being used to get spatial data and map project distribution plans for water, sewage, and electricity. For instance, India’s Restructured Accelerated Power Development & Reforms Program (R-APDRP) government project involves mapping of project areas through GIS for identification of energy distribution assets including transformers and feeders with actual locations of high tension and low tension wires to provide data and maintain energy distribution over a geographical region. R-APDRP is also focused on reducing power loss.
Transparency and Efficiency using Blockchain
Blockchain-based systems are helping the Utilities industry in centralising consumer data, enabling information sharing across key departments and offering more transparent services to consumers.
Energy and Utilities companies are also using the technology to redistribute power from a central location and form smart contracts on Blockchain for decisions and data storage. This is opening opportunities for the industry to trade on energy, and create contracts based on their demand and supply. US-based Brooklyn Microgrid, for example, is a local energy marketplace in New York City based on Blockchain for solar panel owners to trade excess energy generated to commercial and domestic consumers. In an initiative launched by Singapore’s leading Power company, SP Group, companies can purchase Renewable Energy Certificates (RECs) through a Blockchain-powered trading platform, from renewable producers in a transparent, centralised and inexpensive way.
Blockchain is also being used to give consumers the transparency they demand. Spanish renewable energy firm Acciona Energía allows its consumers to track the origin of electricity from its wind and solar farms in real-time providing full transparency to certify renewable energy origin.
Intelligence in Products and Services using AI
Utilities companies are using AI & Automation to both transform customer experience and automate backend processes. Smart Meters, in itself, generate a lot of data which can be used for intelligence based on demographics, usage patterns, demand and supply. This is used for load forecasting and balancing supply and demand for yield optimisation. It is also being leveraged for targeted marketing including personalised messages on Smart Energy usage.
Researchers in Germany have developed a machine learning program called EWeLiNE which is helping grid operators with a program that can calculate renewable energy generation over 48 hours from the data taken from solar panels and wind turbines, through an early warning system.
Niche providers of Smart Energy products have been working with providing energy intelligence to consumers. UK start-up Verv, as an example, uses an AI-based assistant to guide consumers on energy management by tracing the energy usage data from appliances through meters and assisting in reducing costs. Increasingly, Utilities companies will partner with such niche providers to offer similar services to their customers.
Utilities companies have started using chatbots and conversational AI to improve customer experience. For instance, Exelon in the US is using a chatbot to answer common customer queries on power outages and billing.
While the predominant technology focus of Utilities companies is still on cost optimisation, infrastructure management and disaster management, the industry is fast realising the power of having an interconnected system that can transform the entire value chain.

Agents are the most valuable assets in a contact centre. In the current environment, the biggest threat is agents getting infected, causing the closure of contact centres for weeks or possibly even longer. We are already seeing the impact of that with offices being shut, students not going to school and industry gatherings and events being put on hold or cancelled. So having a business continuity plan (BCP) is critical. The BCP should include ways to continue to engage with customers.
The contact centre manages live interactions. Every second there are voice calls coming in, emails received and self-service tools being accessed. It is important to have multiple backup plans – both from a people and a technology perspective – to keep operations running effectively, without calls being put on hold too long or with other channels going unanswered. Contact centres battle with these challenges every day and the situation will get far more serious with the ongoing changes we are witnessing.
Some important considerations include:
Having a backup plan allowing agents working from home
More contact centres today are gearing up to agents working from home, but the process is not an easy one. To begin with, the initial set up includes having the right connectivity and a reliable network. Ensuring that the agent has the right working environment with minimal distraction is crucial. A good quality headset can help. A poor-quality headset will only create unwanted problems with understanding customer issues and handling them. Other concerns include security, tracking how data is being handled, agent under-performance and safety of the agents from an operational and health perspective. Measures such as listening to call recordings and storing them centrally are growing in importance. Multi-factor authentication and analytics using agent logs are some measures that can be put in place.
While there are lots of tools and technologies to monitor and check on agents, the key for home-based agents will be trust. Some outsourced contact centre providers that have been using home-based agents for years have stated that having trust and not micromanaging the agents, is essential for the model to work. Some contact centres have also deployed a BYOD policy for home-based agents assuming the right security, device management, application management and authentication measures are in place.
Organisations should also consider actively recruiting additional home-based agents. These agents could be retirees, currently unemployed or people with mobility issues who prefer to work from home.
Given the difference in the working environment, the metrics used to measure agent performance needs to be modified to be more realistic and fair to both agents and organisations.
Employing home-based agents will drive employment amidst challenges in the economy. Ecosystm research finds that more than a third of organisations do not have provisions for agents working remotely (Figure 1).
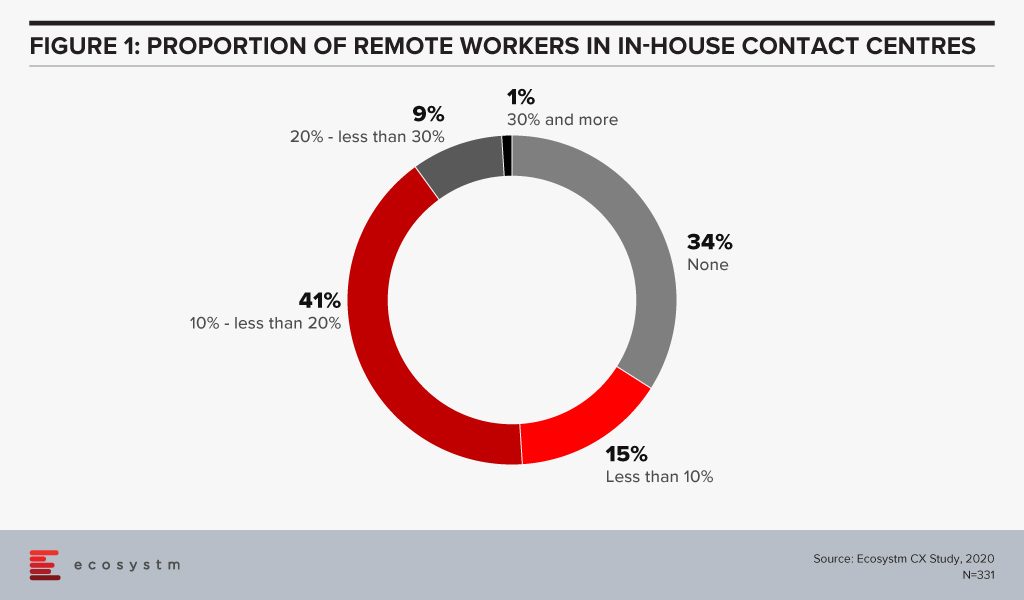
For a long time, the industry has talked about the rise of home-based agents and while it has received positive momentum, it has never really taken off in a big way. This time it will.
Managing spikes in voice and non-voice calls
In industries such as healthcare and airlines, call volumes are exceeding normal volumes. Having the ability to deflect the calls to other non-voice channels will be important. It might need the Interactive Voice Response (IVR) scripts to be changed from time to time to manage the flow of the calls. This is when cloud architecture becomes important. The cloud model can be used to make changes to call workflows easily. The sudden peaks will also require changing the channels easily and without intervention from IT. This is where the agility of cloud comes in as it allows changes and additions – for example when 500 agents need to be added or moved to work on other areas – to be made more easily. Ecosystm research finds that currently, only a third of organisations have their contact centre solutions fully on a cloud, with another 66% with partial cloud solutions. This is set to change with the rise in the number of home-based agents.
There should be thought and planning on how to deflect voice calls to other self-service channels. In the current environment, some organisations deploy a call back option when there is an overflow calls. Similarly looking at deflecting voice calls to self-service channels to ease the load on agents should be evaluated.
Managing back up locations (onshore and offshore)
Contact centre operators are looking at ways to isolate agents and keep them safe. Apart from very strict hygiene measures, organisations are also restricting agents to their specific floor. Some are looking at having agents split into different centres, to contain the risk of mass infection.
Several contact centre operators are building contingency plans to route calls to outside the onshore location in case the situation in a site or a cluster worsens.
For back-end contact centre activities and non-voice calls, taking the load off from the current onshore setup and pushing them offshore, can be an option. The best place to start would be by evaluating each client contract and SLAs especially on security, regulation and privacy issues regarding customer data-handling.
There will be a lot to be considered too should the country go into the full lock-down mode as we are starting to see with a few countries. This makes the case for employing home-based agents stronger.
Using messaging apps, the website and FAQs for daily notifications
Many contact centres are informing citizens and customers about the changes in business operations, services offered, refunds, where to go for help, what do to in an emergency and other essential information through the website, app or the updated FAQ. This will help reduce unnecessary voice and non-voice enquiries to the contact centre. During an emergency, it is normal that phone queries will rise and developing a detailed FAQ is critical to counter that. The more detailed the FAQ giving essential information, the more agents will be able to focus on the more essential day to day activities. Several companies are now sending pop-ups within apps about daily changes to avoid an overflow of inbound enquiries.
Virtual Assistants and Conversational AI can help to ease the load
The more intelligent the virtual assistant and conversational AI platform, the more a customer will be able to get the right response. The challenge has been that many platforms are poorly designed and customers get frustrated because they are unable to get the basic information they need. In times of high inbound activity, if answers to simpler queries can be provided through a chatbot, it can help ease the load on agents. It is good to start planning for this as it will take some time to get the virtual assistant platform up and running and even longer for the algorithms to learn from historical patterns to work well. While it may not be the perfect solution now, planning for a Conversational AI can bring some sort of balance back to the contact centre. Having a solid knowledge management system at the back-end cannot be compromised. Without a good knowledge management system, the virtual assistant solution will force customers to leave the self-service platform and place a call to the contact centre, defeating its very purpose.
The challenging situation we are in is undoubtedly putting pressure on contact centres. It is not uncommon now for customers to be put on hold – for more than two hours and in some extreme cases more than 7 hours! In times like this, understanding data and the patterns around data from each customer touchpoint will help plan the next steps on how best to navigate the situation. Testing and pre-testing the channels and the changes made before they go live must be done rigorously.
Whilst these are very challenging times for the economy, the good news is that contact centres are successfully piloting or have already implemented some or all of the above discussed here. Outsourced contact centre providers are running pilots across various locations and applying technology to deal with the challenges they are witnessing daily. Technology has also come a long way in the contact centre space, and by the application of the right technologies, scale, and business continuity measures, resilience can be achieved.
This blog was created with input from CX leaders across the entire Asia Pacific region. The author wishes to thank everyone for their valuable input.
















