Ecosystm research reveals a stark reality: 75% of technology leaders in Financial Services anticipate data breaches.
Given the sector’s regulatory environment, data breaches carry substantial financial implications, emphasising the critical importance of giving precedence to cybersecurity. This is compelling a fresh cyber strategy focused on early threat detection and reduction of attack impact.
Read on to find out how tech leaders are building a culture of cyber-resilience, re-evaluating their cyber policies, and adopting technologies that keep them one step ahead of their adversaries.
Download ‘Cyber-Resilience in Finance: People, Policy & Technology’ as a PDF

Trust in the Banking, Financial Services, and Insurance (BFSI) industry is critical – and this amplifies the value of stolen data and fuels the motivation of malicious actors. Ransomware attacks continue to escalate, underscoring the need for fortified backup, encryption, and intrusion prevention systems. Similarly, phishing schemes have become increasingly sophisticated, placing a burden on BFSI cyber teams to educate employees, inform customers, deploy multifactor authentication, and implement fraud detection systems. While BFSI organisations work to fortify their defences, intruders continually find new avenues for profit – cyber protection is a high-stakes game of technological cat and mouse!
Some of these challenges inherent to the industry include the rise of cryptojacking – the unauthorised use of a BFSI company’s extensive computational resources for cryptocurrency mining.
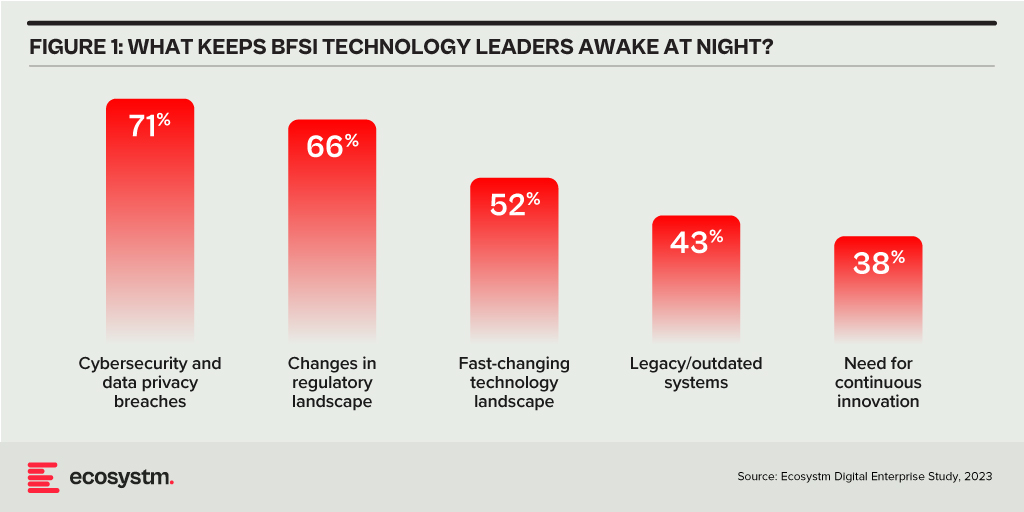
Building Trust Amidst Expanding Threat Landscape
BFSI organisations face increasing complexity in their IT landscapes. Amidst initiatives like robo-advisory, point-of-sale lending, and personalised engagements – often facilitated by cloud-based fintech providers – they encounter new intricacies. As guest access extends to bank branches and IoT devices proliferate in public settings, vulnerabilities can emerge unexpectedly. Threats may arise from diverse origins, including misconfigured ATMs, unattended security cameras, or even asset trackers. Ensuring security and maintaining customer trust requires BFSI organisations to deploy automated and intelligent security systems to respond to emerging new threats.
Ecosystm research finds that nearly 70% of BFSI organisations have the intention of adopting AI and automation for security operations, over the next two years. But the reality is that adoption is still fairly nascent. Their top cyber focus areas remain data security, risk and compliance management, and application security.
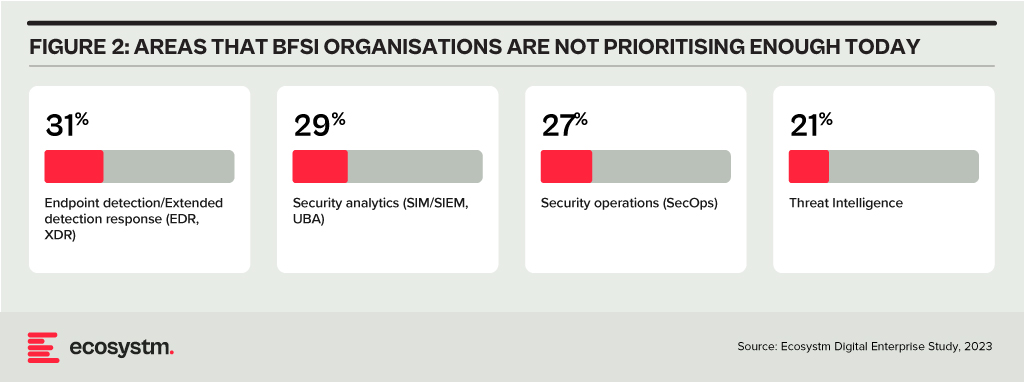
Addressing Alert Fatigue and Control Challenges
According to Ecosystm research, 50% of BFSI organisations use more than 50 security tools to secure their infrastructure – and these are only the known tools. Cyber leaders are not only challenged with finding, assessing, and deploying the right tools, they are also challenged with managing them. Management challenges include a lack of centralised control across assets and applications and handling a high volume of security events and false positives.
Software updates and patches within the IT environment are crucial for security operations to identify and address potential vulnerabilities. Management of the IT environment should be paired with greater automation – event correlation, patching, and access management can all be improved through reduced manual processes.
Security operations teams must contend with the thousands of alerts that they receive each day. As a result, security analysts suffer from alert fatigue and struggle to recognise critical issues and novel threats. There is an urgency to deploy solutions that can help to reduce noise. For many organisations, an AI-augmented security team could de-prioritise 90% of alerts and focus on genuine risks.
Taken a step further, tools like AIOps can not only prioritise alerts but also respond to them. Directing issues to the appropriate people, recommending actions that can be taken by operators directly in a collaboration tool, and rules-based workflows performed automatically are already possible. Additionally, by evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where security operations are completely automated.
Threat Intelligence and Visibility for a Proactive Cyber Approach
New forms of ransomware, phishing schemes, and unidentified vulnerabilities in cloud are emerging to exploit the growing attack surface of financial services organisations. Security operations teams in the BFSI sector spend most of their resources dealing with incoming alerts, leaving them with little time to proactively investigate new threats. It is evident that organisations require a partner that has the scale to maintain a data lake of threats identified by a broad range of customers even within the same industry. For greater predictive capabilities, threat intelligence should be based on research carried out on the dark web to improve situational awareness. These insights can help security operations teams to prepare for future attacks. Regular reporting to keep CIOs and CISOs informed of the changing threat landscape can also ease the mind of executives.
To ensure services can be delivered securely, BFSI organisations require additional visibility of traffic on their networks. The ability to not only inspect traffic as it passes through the firewall but to see activity within the network is critical in these increasingly complex environments. Network traffic anomaly detection uses machine learning to recognise typical traffic patterns and generates alerts for abnormal activity, such as privilege escalation or container escape. The growing acceptance of BYOD has also made device visibility more complex. By employing AI and adopting a zero-trust approach, devices can be profiled and granted appropriate access automatically. Network operators gain visibility of unknown devices and can easily enforce policies on a segmented network.
Intelligent Cyber Strategies
Here is what BFSI CISOs should prioritise to build a cyber resilient organisation.
Automation. The volume of incoming threats has grown beyond the capability of human operators to investigate manually. Increase the level of automation in your SOC to minimise the routine burden on the security operations team and allow them to focus on high-risk threats.
Cyberattack simulation exercises. Many security teams are too busy dealing with day-to-day operations to perform simulation exercises. However, they are a vital component of response planning. Organisation-wide exercises – that include security, IT operations, and communications teams – should be conducted regularly.
An AIOps topology map. Identify where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of threats, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
A trusted intelligence partner. Extend your security operations team by working with a partner that can provide threat intelligence unattainable to most individual organisations. Threat intelligence providers can pool insights gathered from a diversity of client engagements and dedicated researchers. By leveraging the experience of a partner, BFSI organisations can better plan for how they will respond to inevitable breaches.
Conclusion
An effective cybersecurity strategy demands a comprehensive approach that incorporates technology, education, and policies while nurturing a culture of security awareness throughout the organisation. CISOs face the daunting task of safeguarding their organisations against relentless cyber intrusion attempts by cybercriminals, who often leverage cutting-edge automated intrusion technologies.
To maintain an advantage over these threats, cybersecurity teams must have access to continuous threat intelligence; automation will be essential in addressing the shortage of security expertise and managing the overwhelming volume and frequency of security events. Collaborating with a specialised partner possessing both scale and experience is often the answer for organisations that want to augment their cybersecurity teams with intelligent, automated agents capable of swiftly

The Banking, Financial Services, and Insurance (BFSI) industry, known for its cautious stance on technology, is swiftly undergoing a transformational modernisation journey. Areas such as digital customer experiences, automated fraud detection, and real-time risk assessment are all part of a technology-led roadmap. This shift is transforming the cybersecurity stance of BFSI organisations, which have conventionally favoured centralising everything within a data centre behind a firewall.
Ecosystm research finds that 75% of BFSI technology leaders believe that a data breach is inevitable. This requires taking a new cyber approach to detect threats early, reduce the impact of an attack, and avoid lateral movement across the network.
BFSI organisations will boost investments in two main areas over the next year: updating infrastructure and software, and exploring innovative domains like digital workplaces and automation. Cybersecurity investments are crucial in both of these areas.
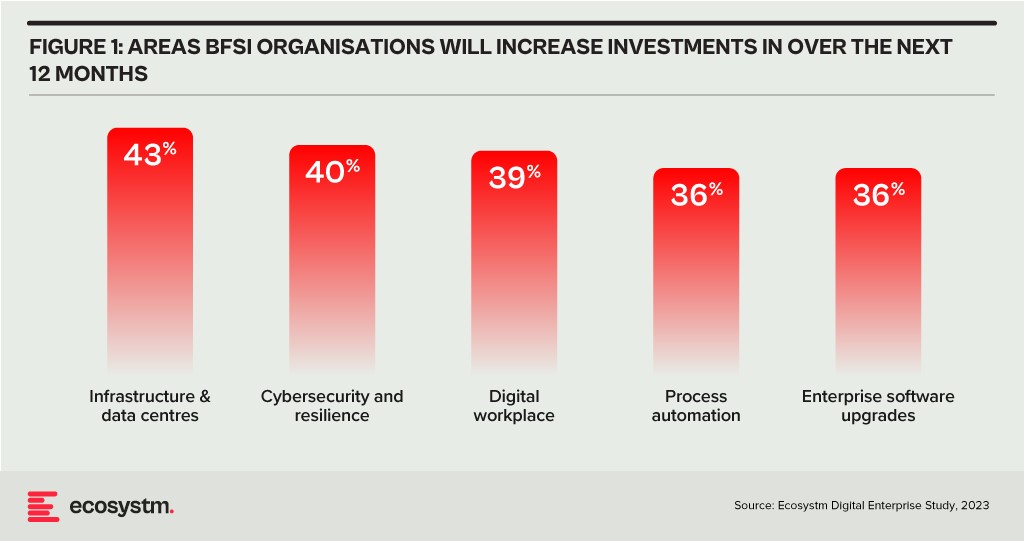
As a regulated industry, breaches come with significant cost implications, underscoring the need to prioritise cybersecurity. BFSI cybersecurity and risk teams need to constantly reassess their strategies for safeguarding data and fulfilling compliance obligations, as they explore ways to facilitate new services for customers, partners, and employees.
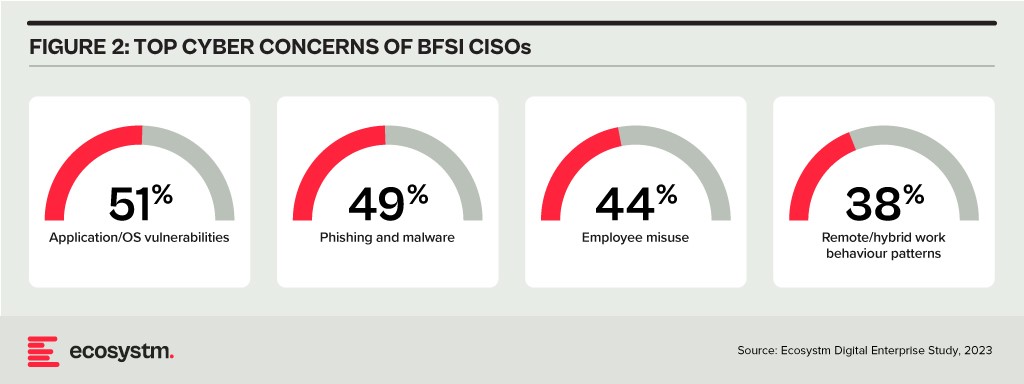
The primary concerns of BFSI CISOs can be categorised into two distinct groups:
- Expanding Technology Use. This includes the proliferation of applications and devices, as well as data access beyond the network perimeter.
- Employee-Related Vulnerabilities. This involves responses to phishing and malware attempts, as well as intentional and unintentional misuse of technology.
Vulnerabilities Arising from Employee Actions
Security vulnerabilities arising from employee actions and unawareness represent a significant and ongoing concern for businesses of all sizes and industries – the risks are just much bigger for BFSI. These vulnerabilities can lead to data breaches, financial losses, damage to reputation, and legal ramifications. A multi-pronged approach is needed that combines technology, training, policies, and a culture of security consciousness.
Training and Culture. BFSI organisations prioritise comprehensive training and awareness programs, educating employees about common threats like phishing and best practices for safeguarding sensitive data. While these programs are often ongoing and adaptable to new threats, they can sometimes become mere compliance checklists, raising questions about their true effectiveness. Conducting simulated phishing attacks and security quizzes to assess employee awareness and identify areas where further training is required, can be effective.
To truly educate employees on risks, it’s essential to move beyond compliance and build a cybersecurity culture throughout the organisation. This can involve setting organisation-wide security KPIs that cascade from the CEO down to every employee, promoting accountability and transparency. Creating an environment where employees feel comfortable reporting security concerns is critical for early threat detection and mitigation.
Policies. Clear security policies and enforcement are essential for ensuring that employees understand their roles within the broader security framework, including responsibilities on strong password use, secure data handling, and prompt incident reporting. Implementing the principle of least privilege, which restricts access based on specific roles, mitigates potential harm from insider threats and inadvertent data exposure. Policies should evolve through routine security audits, including technical assessments and evaluations of employee protocol adherence, which will help organisations with a swifter identification of vulnerabilities and to take the necessary corrective actions.
However, despite the best efforts, breaches do happen – and this is where a well-defined incident response plan, that is regularly tested and updated, is crucial to minimise the damage. This requires every employee to know their roles and responsibilities during a security incident.
Tech Expansion Leading to Cyber Complexity
Cloud. Initially hesitant to transition essential workloads to the cloud, the BFSI industry has experienced a shift in perspective due to the rise of inventive SaaS-based Fintech tools and hybrid cloud solutions, that have created new impetus for change. This new distributed architecture requires a fresh look at cyber measures. Secure Access Service Edge (SASE) providers are integrating a range of cloud-delivered safeguards, such as FWaaS, CASB, and ZTNA with SD-WAN to ensure organisations can securely access the cloud without compromising on performance.
Data & AI. Data holds paramount importance in the BFSI industry for informed decision-making, personalised customer experiences, risk assessment, fraud prevention, and regulatory compliance. AI applications are being used to tailor products and services, optimise operational efficiency, and stay competitive in an evolving market. As part of their technology modernisation efforts, 47% of BFSI institutions are refining their data and AI strategies. They also acknowledge the challenges associated – and satisfying risk, regulatory, and compliance requirements is one of the biggest challenges facing BFSI organisations in the AI deployments.
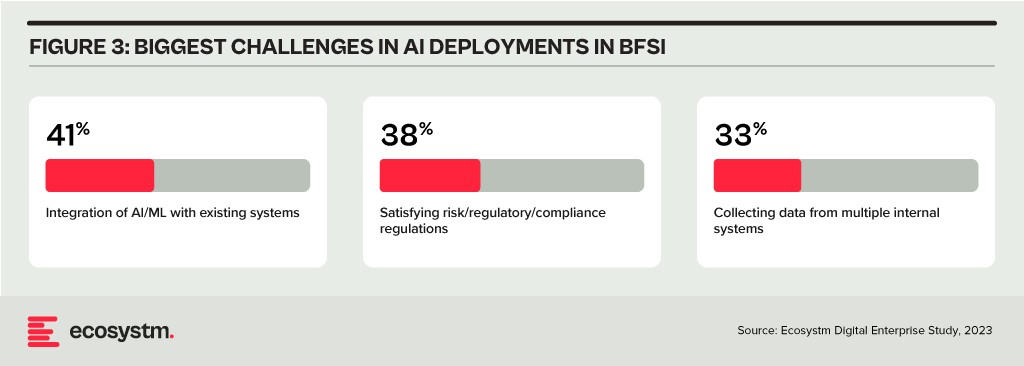
The rush to experiment with Generative AI and foundation models to assist customers and employees is only heightening these concerns. There is an urgent need for policies around the use of these emerging technologies. Initiatives such as the Monetary Authority of Singapore’s Veritas that aim to enable financial institutions to evaluate their AI and data analytics solutions against the principles of fairness, ethics, accountability, and transparency (FEAT) are expected to provide the much-needed guidance to the industry.
Digital Workplace. As with other industries with a high percentage of knowledge workers, BFSI organisations are grappling with granting remote access to staff. Cloud-based collaboration and Fintech tools, BYOD policies, and sensitive data traversing home networks are all creating new challenges for cyber teams. Modern approaches, such as zero trust network access, privilege management, and network segmentation are necessary to ensure workers can seamlessly but securely perform their roles remotely.
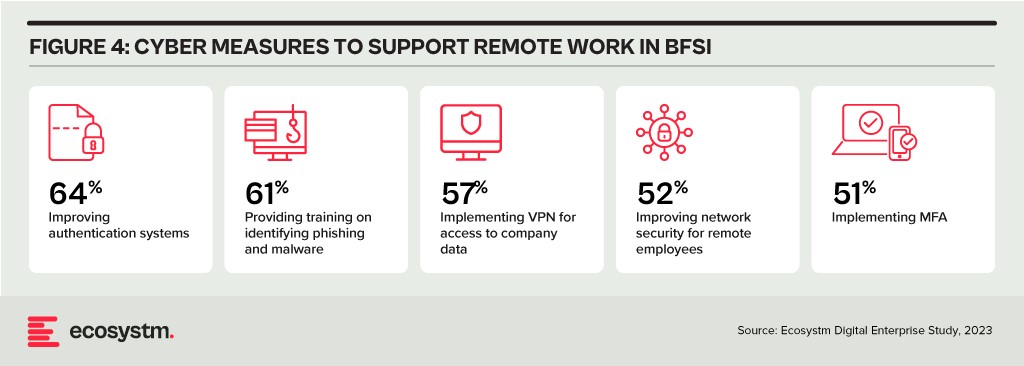
Looking Beyond Technology: Evaluating the Adequacy of Compliance-Centric Cyber Strategies
The BFSI industry stands among the most rigorously regulated industries, with scrutiny intensifying following every collapse or notable breach. Cyber and data protection teams shoulder the responsibility of understanding the implications of and adhering to emerging data protection regulations in areas such as GDPR, PCI-DSS, SOC 2, and PSD2. Automating compliance procedures emerges as a compelling solution to streamline processes, mitigate risks, and curtail expenses. Technologies such as robotic process automation (RPA), low-code development, and continuous compliance monitoring are gaining prominence.
The adoption of AI to enhance security is still emerging but will accelerate rapidly. Ecosystm research shows that within the next two years, nearly 70% of BFSI organisations will have invested in SecOps. AI can help Security Operations Centres (SOCs) prioritise alerts and respond to threats faster than could be performed manually. Additionally, the expanding variety of network endpoints, including customer devices, ATMs, and tools used by frontline employees, can embrace AI-enhanced protection without introducing additional onboarding friction.
However, there is a need for BFSI organisations to look beyond compliance checklists to a more holistic cyber approach that can prioritise cyber measures continually based on the risk to the organisations. And this is one of the biggest challenges that BFSI CISOs face. Ecosystm research finds that 72% of cyber and technology leaders in the industry feel that there is limited understanding of cyber risk and governance in their organisations.
In fact, BFSI organisations must look at the interconnectedness of an intelligence-led and risk-based strategy. Thorough risk assessments let organisations prioritise vulnerability mitigation effectively. This targeted approach optimises security initiatives by focusing on high-risk areas, reducing security debt. To adapt to evolving threats, intelligence should inform risk assessment. Intelligence-led strategies empower cybersecurity leaders with real-time threat insights for proactive measures, actively tackling emerging threats and vulnerabilities – and definitely moving beyond compliance-focused strategies.

Against a backdrop of extended disruption, cybersecurity risks are expanding rapidly and current defences are inadequate. Ransomware attacks are increasing in frequency and impact, focusing more on targets where outages are not an option, such as critical infrastructure and hospitals. Supply chain attacks are creating chaos and has led to a much-needed focus on supply chain vulnerabilities.
As digitalisation continues at a faster pace, cybersecurity is too often, a secondary concern.
With the acceleration of cloud adoption; widespread remote working; the resulting proliferation of endpoints; and the expansion of attack surface for malicious actors, this is the time for organisations to transform their cybersecurity approaches.
Here are the 5 steps that you should consider:
- Having CISOs report directly into top management – bypassing CIOs
- Focusing on configuration management
- Building resilience against ransomware attacks
- Migrating away from a legacy perimeter-based approach
- Shifting to Policy-as-Code
In 2022, attacks on organisations will grow in frequency and intensity. Organisations need to transform their approaches to cybersecurity. This involves embracing new concepts such as zero-trust and Secure Access Service Edge (SASE) as well as a stronger focus on policy as code and human factors.
Click here to download Shaping your Cyber Practice in 2022 as a PDF

Ecosystm recently partnered with Asavie to conduct a study into the opportunity and outlook for the “Branch of One”. One of the challenges was actually defining what the Branch of One is. Here’s what we came up with:
Branch of One enables Office Anywhere by delivering secure, frictionless access to all business resources, with full mobility – meeting the security and manageability requirements of CIOs and CISOs.
Basically it is all the data and systems you need to get your job done, in your pocket. Secure. Easy to manage.
What I really like about the idea is that it describes what business is trying to achieve and it gives a common language and outcome for IT and business leaders. Consider all the things that IT and security teams need to do to enable access to applications and data in remote branches – from connectivity to security to data and system access. Often it takes days, weeks or months to open a new office or branch, or to provision a new retail store. Now, imagine having the ability to roll out all of these systems and services in seconds. To a single user or to thousands. Without consideration for location. Business leaders will understand this benefits and will support it.
It also has the opportunity to help nearly every business today. Of the 1005 businesses we interviewed across the globe in our Global CxO Study 2020, 44% admitted to suffering cyber-attack incidents during COVID-19 due to employees working from home – and over half of these attacks were on mobile devices. Compromised devices were the number one target for cyber-attacks in 2020.
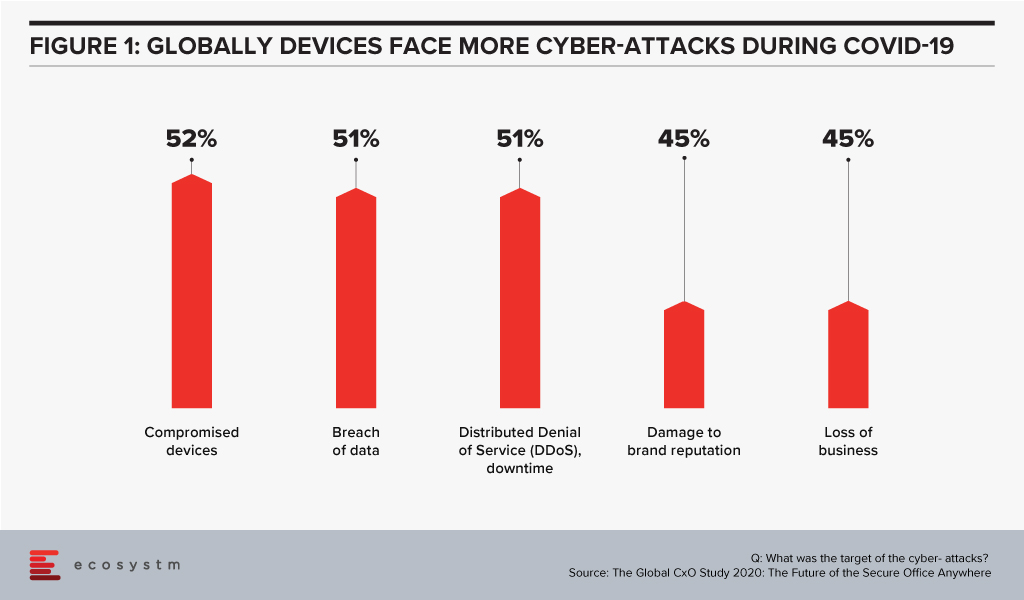
Businesses need a new way to manage the devices and applications of their remote employees. They need to be able to extend the benefits of the WAN to them without the downsides of VPNs. Every business we interviewed saw benefits of bringing devices, locations and offices inside the WAN. Turning every device and office into a Branch of One.
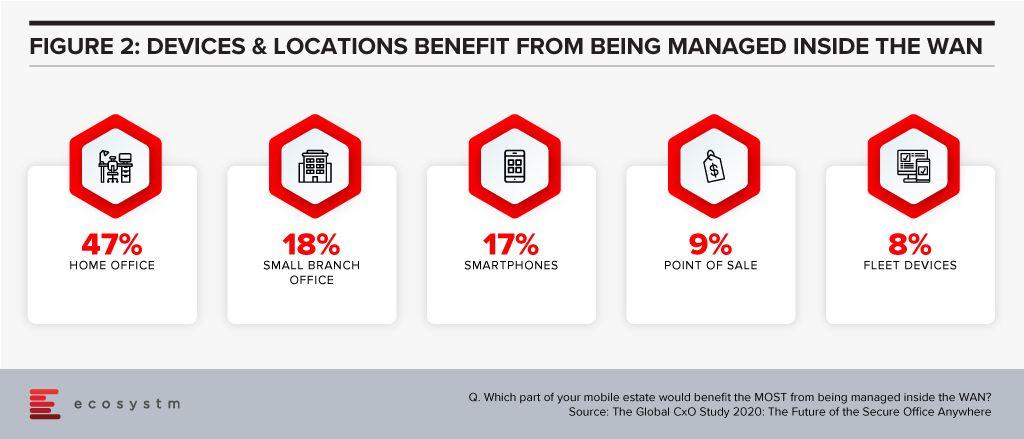
A few security and network technologies have promised this capability – SDNs can offer a similar service, but they require client software to be installed. 78% of businesses we interviewed are using VPNs to bring devices inside the WAN – but again, they require client software, and can be inconsistent (and insecure!) on mobile devices.
Companies that embrace the Branch of One can provision new users in a few clicks. No software to install, no cables to connect, no hardware to provision – it makes life easier for technology and security professionals. The Branch of One gives your employees the systems and data they need to get their job done – delivered securely across the mobile network.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

CEOs have an active role to play in an organisation’s transformation needs and journey – including in the technology decisions. Last month we spoke about why CEOs should get involved in their organisation’s IoT investments. Now, we look at Cloud – which has been a part of the CIO’s purview so far. Under the current circumstances, most organisations are actively pushing to go digital and the internal discussions will often revolve around empowering remote employees and digital customers. All the technologies that are being evaluated by organisations today have Cloud as their pillar. Increasingly, we see organisations adopt the hybrid and the multi-cloud. And organisations may not have the capabilities – technological and skills – to support the complexity of their Cloud environment. While a CEO does not have to understand the technology fully, it is important to understand the business impact of the technology.
Why should a CEO get involved in and have visibility into an organisation’s Cloud investments? There are a few important reasons.
#1 Cloud is not a cost-saving measure – it will enable you to transform
Organisations have matured in their Cloud adoption and no longer evaluate the benefits of Cloud only in terms of shifting CapEx to OpEx. If we look at the benefits of Cloud adoption, reduction of IT costs is not even in the top 3 benefits that organisations are seeking from Cloud anymore. Operational efficiency and collaboration emerge as key benefits (Figure 1) – while some companies still move to the Cloud for the savings, they stay there for other benefits.
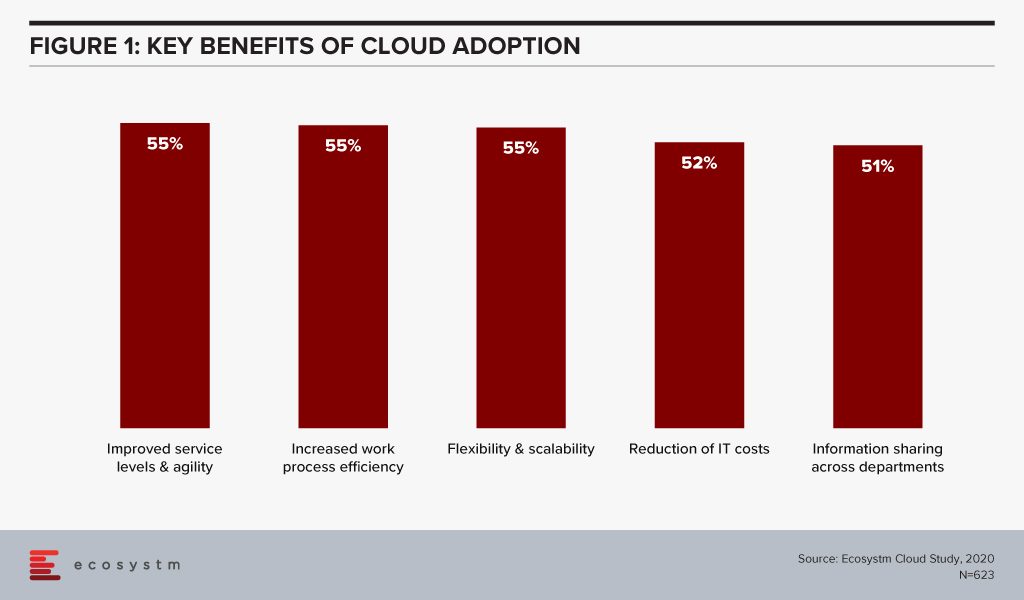
This requires organisations to think of Cloud as a technology empowering their infrastructure and services. Cloud acts as an enabler for ease of doing business, real-time data access for productivity increase, and process automation. This impacts the entire organisation. It also involves prioritising the needs of certain functions over others – definitely not what a CIO should have to do.
If we look at just Cloud storage as an example, organisations can no longer have individual functions and their associated shadow IT teams having their own Cloud storage (and collaboration). This often turns out to be more expensive and there is a lack of consolidated view and management. While organisations forge ahead with the dream of having real-time information sharing across functions, a CIO has to consider the entire organisation’s technological and business needs – a CEO is the best person to guide the CIO in translating the organisation’s vision into IT priorities.
#2 In fact Cloud adoption may not cut costs at all!
Organisations are also re-evaluating the cost benefits of Cloud. Investing in a Cloud infrastructure with a short-term view on the investments involved has led to instances of Cloud solutions being brought back in-house because of rising costs. While security, data privacy and integration remain the key challenges of Cloud adoption (Figure 2), over a third of the organisations find Cloud more expensive than traditional licensing or owning the hardware.
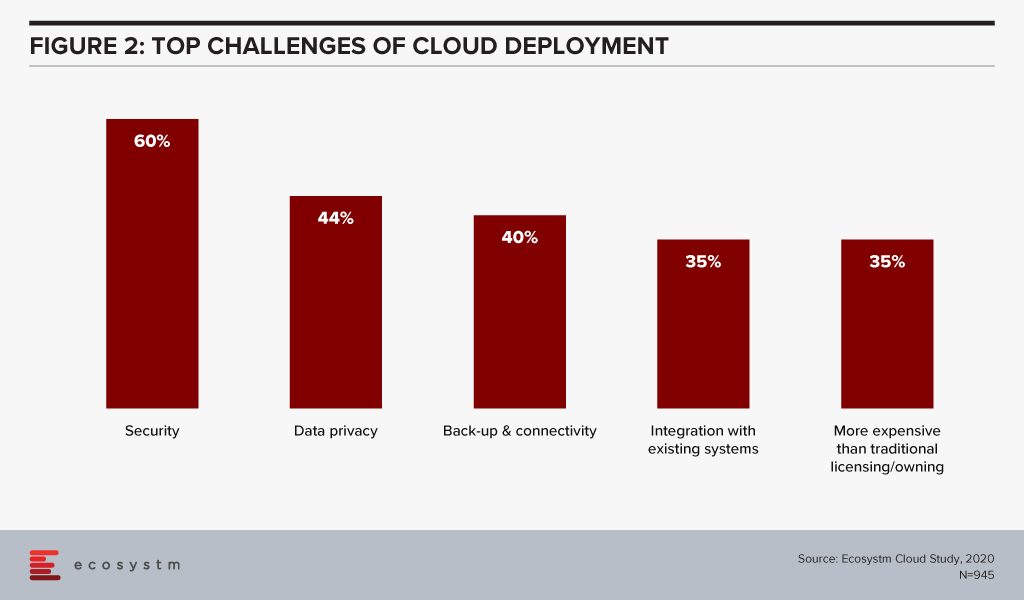
Organisations find that the cost considerations do not stop after the adoption or migration. As businesses use Cloud to scale, there are several aspects that require constant re-evaluation and often further investments – cybersecurity measures, continuous data protection (CDP), disaster recovery management, rightsizing capacity, software and database licenses and day-to-day maintenance, to name a few. In addition to this, the cost of finding and recruiting a team of professionals to manage and maintain the Cloud environment also adds up to the OpEx.
If the CIO is talking about a Cloud migration for cost benefits only, the CEO and the CFO need to step in to evaluate that all factors have been taken into consideration. Moreover, the CIO may not have full visibility of how and where the organisation is looking to scale up or down. It is the CEO’s responsibility to share that vision with the CIO to guide Cloud investments.
#3 Cloud will increasingly be part of all tech adoption considerations
In this disruptive world, CEOs should explore possibilities and understand the technical capabilities which can give organisations an edge over their competitors. It is then up to the CIOs to implement that vision with this larger context in mind. As organisations look to leverage emerging technologies, organisations will adopt Cloud to optimise their resources and workloads.
AI is changing the way organisations need to store, process and analyse the data to derive useful insights and decision-making practices. This is pushing the adoption of Cloud, even in the most conservative organisations. Cloud is no longer only required for infrastructure and back-up – but actually improving business processes, by enabling real-time data and systems access. Similarly, IoT devices will grow exponentially. Today, data is already going into the Cloud and data centres on a real-time basis from sensors and automated devices. However, as these devices become bi-directional, decisions will need to be made in real-time as well. Edge Computing will be essential in this intelligent and automated world. Cloud platform vendors are building on their edge solutions and tech buyers are increasingly getting interested in the Edge allowing better decision-making through machine learning and AI.
In view of the recent global crisis, we will see a sharp uptake of Cloud solutions across tech areas. IaaS will remain the key area of focus in the near future, especially Desktop-as-as-Service. Organisations will also look to evaluate more SaaS solutions, in order to empower a mobile and remote workforce. This will allow the workforce of the future to stay connected, informed and make more decisions. More than ever, CEOs have to drive business growth with innovative products and services – not understanding the capabilities and challenges of Cloud adoption and the advancements in the technology can be a serious handicap for CEOs.
#4 Your IT Team may be more complacent about Cloud security than you think
Another domain that requires the CEO’s attention is cybersecurity. The Cloud is used for computing operations and to store data including, intellectual property rights, financial information, employee details and other sensitive data. Cybersecurity breaches have immense financial and reputational implications and IT Teams cannot solely be responsible for it. Cybersecurity has become a Board-level conversation and many organisations are employing a Chief Information Security Officer (CISO) who reports directly into the CEO. Cybersecurity is an aspect of an organisation’s risk management program.
Evaluating the security features of the Cloud offerings, therefore, becomes an important aspect of an IT decision-maker’s job. While security remains a key concern when it comes to Cloud adoption, Cloud is often regarded as a more secure option than on-premise. Cloud providers have dedicated security focus, constantly upgrade their security capabilities in response to newer threats and evolve their partner ecosystem. There is also better traceability with the Cloud as every virtual activity can be tracked, monitored, and logged. Ecosystm research finds that more than 40% of IT decision-makers think the Public Cloud has enough security measures and does not need complementing (Figure 3).
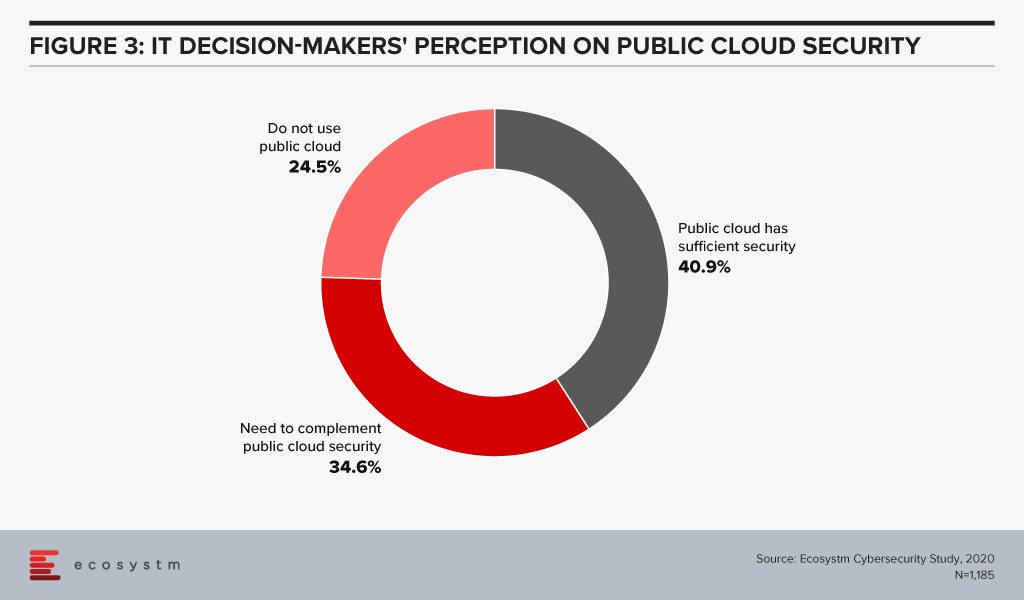
However, the Cloud is as secure as an organisation makes it. The perception that there is no need to supplement Public Cloud security features can have disastrous outcomes. It is important to supplement the Cloud provider’s security with event-driven security measures within an organisation’s applications and cloud interface.
It is the job of the CEO – through the CISO – to evaluate how cyber ready the IT Team really is. Do they know enough about shared responsibility? Do they have full cognizance of the SLAs of their Cloud providers? Do they have sufficient internal cybersecurity skills? Do they understand that data breaches can have cost and reputational impacts? As cybersecurity breaches begin to have more financial implications than ever and can derail an organisation, a CEO should have visibility of the risks of the organisation’s Cloud adoption.
Cloud is no longer just a technological decision – it is a business decision and takes into account the organisation’s vision. A full visibility of the Cloud roadmap – including the pitfalls, the risks and the immense potential – will empower a CEO immensely.

One of the questions that organisations are asked in the global Ecosystm Cybersecurity Study, is how they rate their cybersecurity measures and controls (on a scale of 1-10, where 10 is extremely mature). Organisations that rate themselves at an 8-10, are considered ‘mature’ in their cybersecurity measures while those that rate themselves at 1-7 are evolving their cybersecurity practices. Clear differences in priorities and investments can be seen between the mature and evolving adopters of cybersecurity measures.
Here are the key differences that emerge and should allow organisations to benchmark their cybersecurity practices against those of the mature adopters of cybersecurity solutions.
#1 Do you have the Right Motives?
There is no denying that organisations have to continue to evolve their cybersecurity measures with the evolving threat landscape. There is a need to have a continued focus on cybersecurity. However, are they doing it to address the right issues and threats? Mature organisations have their cybersecurity measures entrenched within the organisation’s risk management programs which help them align their investments to their risk position (Figure 1). Very often these programs have their technology landscape – special projects for digital transformation (DX) – and industry compliance laws built into them. Mature organisations also have a proactive approach to incidents and breaches, continuing to evolve their cybersecurity practices.
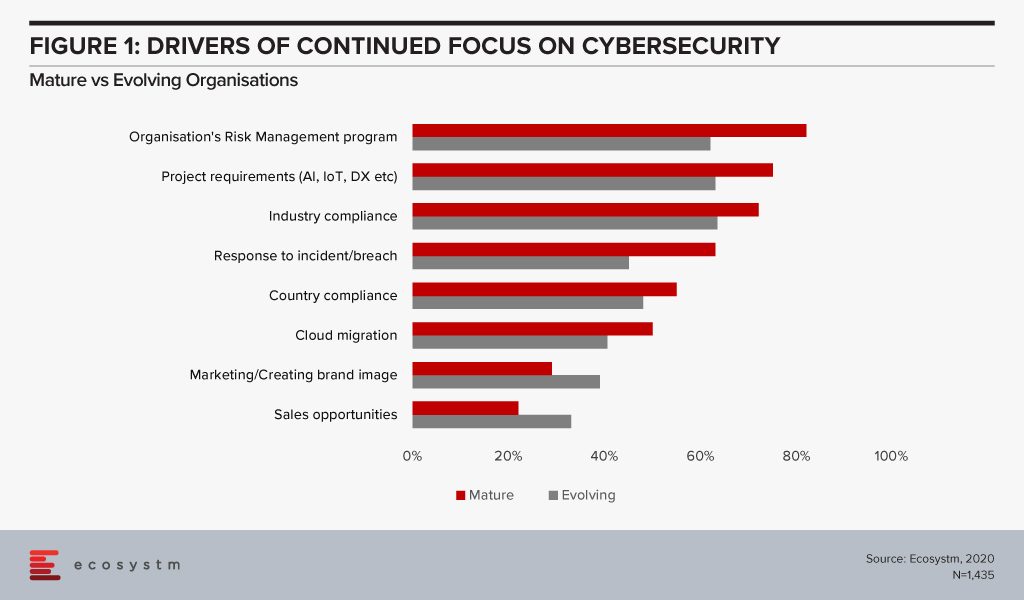
While cybersecurity practices can help with an organisation’s go-to-market messaging, the reasons for investing in robust cybersecurity practices should be more aligned to the organisation’s risk strategies. Also, it should not be restricted to compliance alone and should be much more proactive than merely ticking the right boxes.
#2 Are you focusing on the Right Challenges?
As solution complexity increases, organisations are challenged by their cybersecurity deployments (Figure 2). Cybersecurity measures must be applied across the entire organisation and systems, including applications, database, and storage whether on-prem or on cloud (public, private or hybrid). This adds to the complexity of the solutions and the associated integration challenges.
While it is not possible to have an unlimited budget for cybersecurity measures, once it is treated like a business issue, and the risks associated (including financial and reputational) are conveyed to the key stakeholders cybersecurity budgets become part of the organisational strategy consideration. If your security team is still struggling to procure what they think is the right budget, there is a mismatch in expectations and miscommunication between the security team and executive management. “A risk focussed approach enables organisations to understand the ROI on security measures and therefore invest in the most impactful areas of cyber risk for their business”, says Alex Woerndle, Principal Advisor Ecosystm.
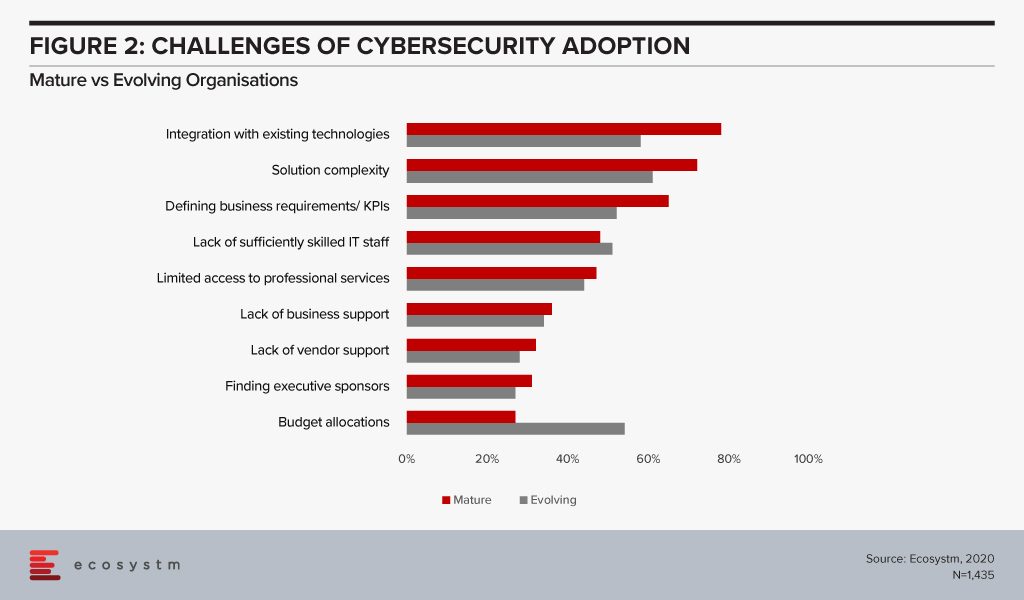
A real challenge that all organisations face is skills shortage. However, it is time to align business and security strategies and look beyond IT for security analysts – professionals who can translate what the Board’s priorities are into defining the security strategy.
#3 Do you have a dedicated Cybersecurity Role?
While the Board will often be involved in evaluating the risk exposure of an organisation, there is need for a dedicated role that can traverse both the business and the technological needs in deciding the right cybersecurity framework.
Organisations should have a dedicated responsibility for their cybersecurity practice – the CISO/CSO is the key data protection lead in mature organisations (Figure 3). CISOs should be reporting into the CFO, Chief Risk Officer or the CEO and not the CIO to avoid a conflict of interest. Alex says, “While the most common reporting line for CISOs is still to the CIO, there is a fundamental conflict of interest with this model – being part of the risk function, or reporting directly to the CEO, provides the level of independence required for good governance of cyber risk.”
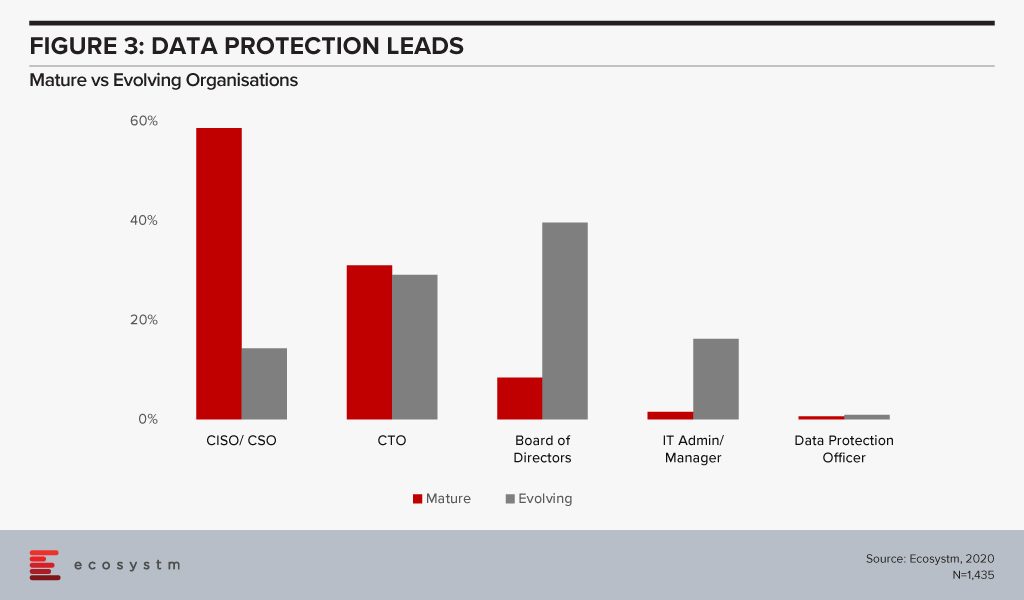
The reality is that many organisations – especially small and medium enterprises that have small dedicated security teams – will find it difficult to appoint a dedicated CSO/CISO. The study also finds that 80% of evolving organisations have less than 10 employees in their security teams as compared to only a third of mature organisations. Carl Woerndle, Principal Advisor Ecosystm, suggests these organisations look at the option of hiring a vCISO (virtual CISO). “A vCISO can help your organisation deliver a full security program within a fixed budget. Hiring someone external also has the added benefits of bringing objectivity to your security strategies and providing guidance on newer skills and technologies to your security teams.”
#4 Are you aware of Cloud Risk?
Cloud adoption has become mainstream, especially as organisations ramp up their digitalisation initiatives. It adds scale and agility to the organisation’s transformation investments. While security remains a key concern when it comes to cloud adoption, cloud is often regarded as a more secure option than on-premise. Cloud providers have dedicated security focus, constantly upgrade their security capabilities in response to newer threats and evolve their partner ecosystem. There is also better traceability with cloud as every virtual activity can be tracked, monitored, and is loggable.
However, mature organisations not only use on-prem options more for their sensitive data storage (Figure 4), they are also more skeptical about relying only on public cloud security features. Only 34% of mature organisations feel that public cloud security features do not need to be complemented while 52% of evolving organisations share that perception.
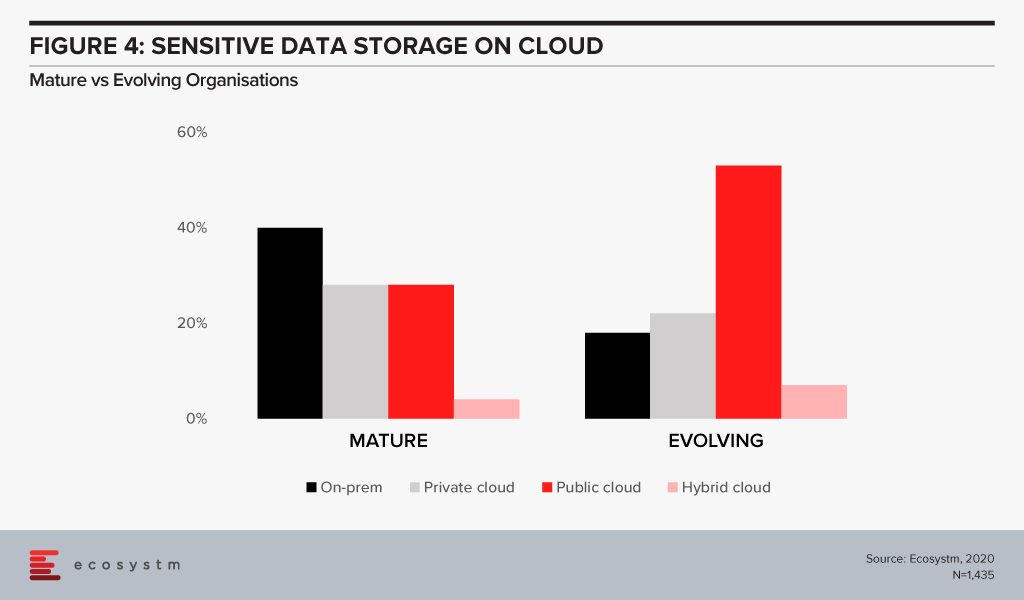
The cloud is as secure as an organisation makes it. The perception that there is no need to supplement public cloud security features can have disastrous outcomes. It is important to supplement the cloud provider’s security with event-driven security measures within an organisation’s applications and cloud interface. Alex says, “Assuming the big cloud providers have security covered for you is a huge mistake. Understanding the shared responsibility model is crucial in your public cloud adoption journey. The tools are available – but typically at an extra cost, and you need to employ, configure and continually manage them for effective security.”
The big differentiator between mature and evolving organisations in securing cloud environments is in the use of multi-factor authentication (Figure 5). With 3/4th of mature organisations employing this as a control, it highlights that passwords – even strong passwords – alone, are not sufficient in 2020. Mature organisations are increasingly investing in encryption. But the perception of the complexity in deploying and managing encryption (and the keys) has been a challenge especially for organisations with smaller teams and less in-house technical capabilities.
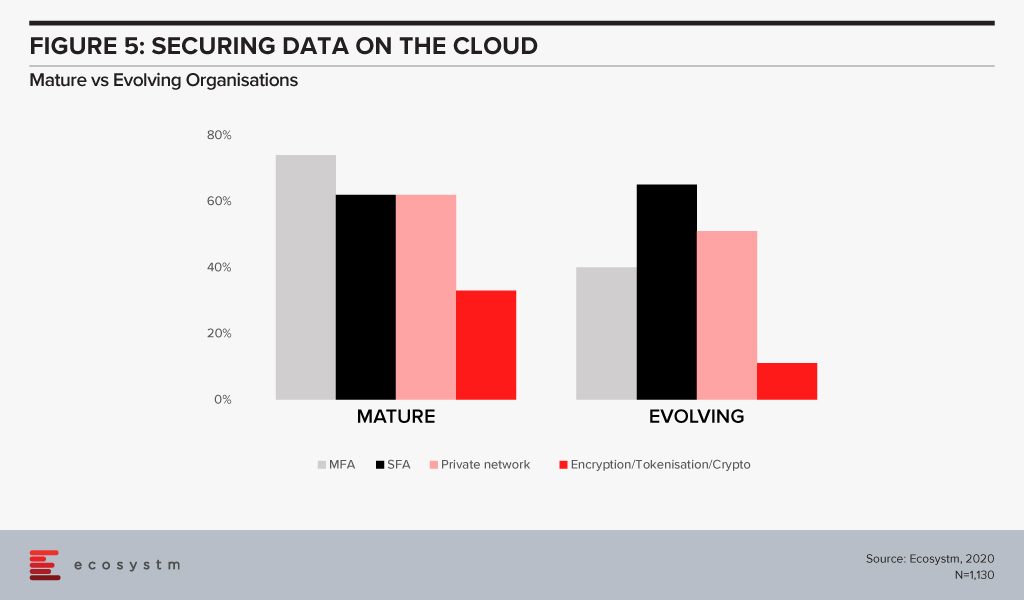
#5 Are you Breach Ready?
Global organisations generally consider a data breach as inevitable – largely believing that “it is not about if, but when”(Figure 6). All organisations will face some incident, attempted breach or a breach, at some point. It is necessary to have the right cybersecurity measures to avoid breaches – but it is equally important to be prepared for when a breach actually happens. A majority of organisations, regardless of maturity, are worried about (and expect) a breach. For evolving organisations this is a troubling statistic given their use of public cloud with limited security understanding or controls – better education is needed from the public cloud providers but also the security industry.
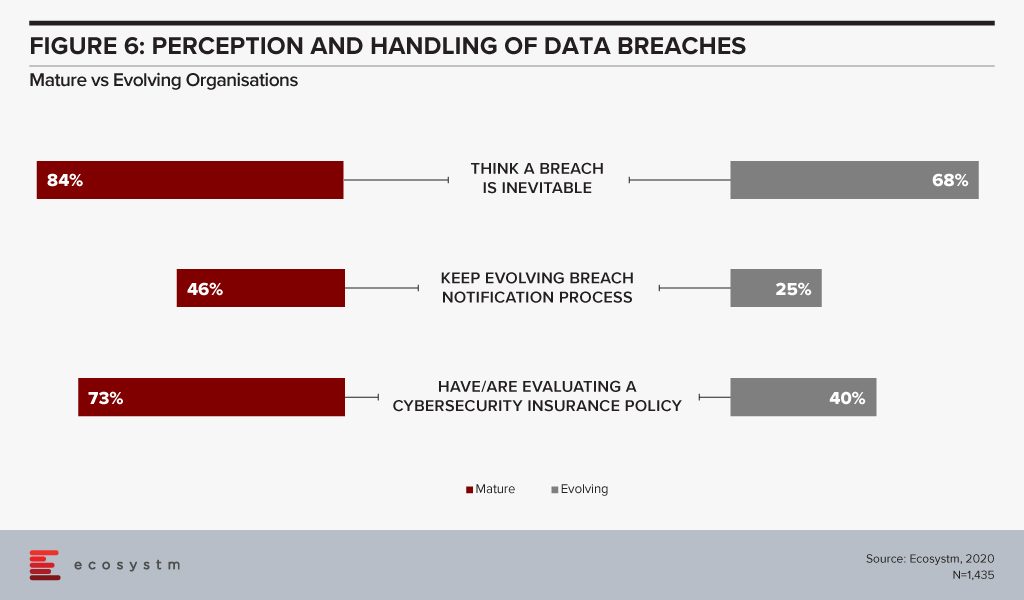
Breach notification processes need to keep evolving – and they must also include employees. Organisations should be aware of the need for people management during an incident. Policies might be clear and adhered to, but it is substantially harder to train the stakeholders involved, on how they will handle the breach emotionally. It extends to how an organisation manages their welfare both during an incident, and long after the incident response has been closed off.
“Cyber insurance has rapidly become a must-have as part of an organisation’s layered defence. While it provides a layer of support in the event of a breach, you should not rely on it as your only safety net,” Carl adds. “It is also important to ensure that your cyber cover is appropriate to your risks and organisational needs and policies should be evaluated carefully.”



























