The semiconductor industry is 70-years old and has a prominent – and sometimes inconspicuous – presence in our daily lives. Many of us, however, have become more aware of the industry and the ramifications of its disruption, because of recent events. The pandemic, natural disasters, power outages, geo-political conflicts, and accelerated digital transformation have all combined to disrupt the semiconductor sector, leaving no organisation immune to the impacts of the continuing global chip crisis.
It is estimated that 200 downstream industries have failed to fulfill customer demands owing to the silicon scarcity, ranging from automotive, consumer electronics, utilities and even the supply of light fixtures.
This Ecosystm Bytes discusses the impact of the crisis and highlights major initiatives that chip manufacturers and governments are taking to combat it, including:
- The factors leading to the shortage in the semiconductor industry
- The impact on industry sectors such as Automotive, Consumer Electronics and MedTech
- How leading chip makers such as TSMC, Intel and Samsung are increasing their manufacturing capabilities
- The importance of Asia to the semiconductor industry
- How countries such as Malaysia and India are aiming to build self-sufficiency in the industry
Read on to find out more.

The Healthcare industry has achieved much in the last two years, despite all the struggles and pivots. However, the impact of COVID-19 on the industry is far from over.
2020 was focused on finding a vaccine against the virus, setting treatment protocols, and workforce management to handle the emergency. 2021 was focused on vaccine distribution and administration. 2022 will be the year when we start seeing the second-order impacts of the pandemic – and see healthcare providers address these impacts.
In 2022 the key drivers of the ongoing transformation in Healthcare will be:
- Patients. Improved self-knowledge and ownership of personal health outcomes and data
- Technology. Widespread availability and adoption of digital and cognitive technologies
- Employees. The ongoing challenges of clinical and administrative staff
- The Life Sciences Industry. The recent investments in, and success of the sector
- Policy Makers. The sharp increase in focus on population health
- Continued Uncertainty. Around challenges such as new virus strains, anti-vaccine protests, supply chain disruptions etc.
Read on to find out what Ecosystm Analysts Amit Rana, Krish Krishnan, and Sash Mukherjee think are the key achievements of the industry and the future trends in 2022 and beyond.

In this Insight, our guest author Anupam Verma talks about how the Global Capability Centres (GCCs) in India are poised to become Global Transformation Centres. “In the post-COVID world, industry boundaries are blurring, and business models are being transformed for the digital age. While traditional functions of GCCs will continue to be providing efficiencies, GCCs will be ‘Digital Transformation Centres’ for global businesses.”

India has a lot to offer to the world of technology and transformation. Attracted by the talent pool, enabling policies, digital infrastructure, and competitive cost structure, MNCs have long embraced India as a preferred destination for Global Capability Centres (GCCs). It has been reported that India has more than 1,700 GCCs with an estimated global market share of over 50%.
GCCs employ around 1 million Indian professionals and has an immense impact on the economy, contributing an estimated USD 30 billion. US MNCs have the largest presence in the market and the dominating industries are BSFI, Engineering & Manufacturing, Tech & Consulting.
GCC capabilities have always been evolving
The journey began with MNCs setting up captives for cost optimisation & operational excellence. GCCs started handling operations (such as back-office and business support functions), IT support (such as app development and maintenance, remote IT infrastructure, and help desk) and customer service contact centres for the parent organisation.
In the second phase, MNCs started leveraging GCCs as centers of excellence (CoE). The focus then was product innovation, Engineering Design & R&D. BFSI and Professional Services firms started expanding the scope to cover research, underwriting, and consulting etc. Some global MNCs that have large GCCs in India are Apple, Microsoft, Google, Nissan, Ford, Qualcomm, Cisco, Wells Fargo, Bank of America, Barclays, Standard Chartered, and KPMG.
In the post-COVID world, industry boundaries are blurring, and business models are being transformed for the digital age. While traditional functions of GCCs will continue to be providing efficiencies, GCCs will be “Digital Transformation Centres” for global businesses.
The New Age GCC in the post-COVID world
On one hand, the pandemic broke through cultural barriers that had prevented remote operations and work. The world became remote everything! On the other hand, it accelerated digital adoption in organisations. Businesses are re-imagining customer experiences and fast-tracking digital transformation enabled by technology (Figure 1). High digital adoption and rising customer expectations will also be a big catalyst for change.
In last few years, India has seen a surge in talent pool in emerging technologies such as data analytics, experience design, AI/ML, robotic process automation, IoT, cloud, blockchain and cybersecurity. GCCs in India will leverage this talent pool and play a pivotal role in enabling digital transformation at a global scale. GCCs will have direct and significant impacts on global business performance and top line growth creating long-term stakeholder value – and not be only about cost optimisation.
GCCs in India will also play an important role in digitisation and automation of existing processes, risk management and fraud prevention using data analytics and managing new risks like cybersecurity.
More and more MNCs in traditional businesses will add GCCs in India over the next decade and the existing 1,700 plus GCCs will grow in scale and scope focussing on innovation. Shift of supply chains to India will also be supported by Engineering R & D Centres. GCCs passed the pandemic test with flying colours when an exceptionally large workforce transitioned to the Work from Home model. In a matter of weeks, the resilience, continuity, and efficiency of GCCs returned to pre-pandemic levels with a distributed and remote workforce.
A Final Take
Having said that, I believe the growth spurt in GCCs in India will come from new-age businesses. Consumer-facing platforms (eCommerce marketplaces, Healthtechs, Edtechs, and Fintechs) are creating digital native businesses. As of June 2021, there are more than 700 unicorns trying to solve different problems using technology and data. Currently, very few unicorns have GCCs in India (notable names being Uber, Grab, Gojek). However, this segment will be one of the biggest growth drivers.
Currently, only 10% of the GCCs in India are from Asia Pacific organisations. Some of the prominent names being Hitachi, Rakuten, Panasonic, Samsung, LG, and Foxconn. Asian MNCs have an opportunity to move fast and stay relevant. This segment is also expected to grow disproportionately.
New age GCCs in India have the potential to be the crown jewel for global MNCs. For India, this has a huge potential for job creation and development of Smart City ecosystems. In this decade, growth of GCCs will be one of the core pillars of India’s journey to a USD 5 trillion economy.
The views and opinions mentioned in the article are personal.
Anupam Verma is part of the Senior Leadership team at ICICI Bank and his responsibilities have included leading the Bank’s strategy in South East Asia to play a significant role in capturing Investment, NRI remittance, and trade flows between SEA and India.

Since the start of this millennium, no region has transformed as much as Asia. There has been significant paradigm shifts in the region and the perception that innovation starts in the US or in Europe and percolates through to Asia after a time lag, has been shattered. Asia is constantly demonstrating how dynamic, and technology-focused it is. This is getting fueled by the impact of the growing middle class on consumerism and the spirit of innovation across the region. The region has also seen a surge in new and upcoming business leaders who are embracing change and looking beyond success to creating impact.
What is Driving Innovation in Asia?
The “If you ain’t got it, build it” attitude. One of the key drivers of this shift is the age of the average population in Asia. According to the UN the Asia Pacific region has nearly 60% of the world’s youth population (between the age of 17-24). With youth comes dynamism, a desire to change the world, and innovation. As this age group enters the workforce, they will transform their lives and the companies they work in. They are already showing a spirit of agility when it comes to solving challenges – they will build what they do not have.
The Need to enable Foundational Shifts. The younger generation is more aware of environmental, social and governance issues that the world continues to face. Many of the countries in the region are emerging economies, where these issues become more apparent. COVID-19 has also inculcated an empathy in people and they are thinking of future success in terms of impact. The desire to enable foundational shifts is giving direction to the transformation journey in the region. The wonderful new paradigm that is the Digital Economy allows us to cut across all segments; and technology and its advancements has immense potential to create a more sustainable and inclusive future for the world.
Realising the Power of Momentum. The pandemic has caused major disruptions in the region. But every crisis also presents an opportunity to perhaps re-imagine a brighter world through a digital lens. The other thing that the pandemic has done is made people and organisations realise that to succeed they need to be open to change – and that momentum is important. As organisations had to pivot fast, they realised what I have been saying for years – we shouldn’t “let perfect get in the way of better”. This adaptability and the readiness to fail fast and learn from the mistakes early for eventual success, is leading to faster and more agile transformation journeys.
Where are we seeing the most impact?
Industries are Transforming. There are industries such as Healthcare and Education that had to transform out of a necessity and urgency brought about by the COVID-19 pandemic. This has led to a greater impetus for change and optimism in these industries. These industries will continue to transform as governments focus significantly on creating “Social Safety Nets” and technology plays a key role in enabling critical services across Health, Education and Food Security. Then there are industries, such as the Financial Services and Retail, that had a strong customer focus and were well on their digital journeys before the pandemic. The pandemic boosted these efforts.
But these are not the only industries that are transforming. There are industries that have been impacted more than others. There are several instances of how organisations in these industries are demonstrating not only resilience but innovation. The Travel & Hospitality industry has had several such instances. As business models evolve the industry will see significant changes in digital channels to market, booking engines, corporate service offerings and others, as the overall Digital Strategy is overhauled.
Technologies are Evolving. Organisations depended on their tech partners to help them make the fast pivot required to survive and succeed in the last year – and tech companies have not disappointed. They have evolved their capabilities and continue to offer innovative solutions that can solve many of the ongoing business challenges that organisations face in their innovation journey. More and more technologies such as AI, machine learning, robotics, and digital twins are getting enmeshed together to offer better options for business growth, process efficiency and customer engagement. And the 5G rollouts will only accelerate that. The initial benefits being realized from early adoption of 5G has been for consumers. But there is a much bigger impact that is waiting to be realised as 5G empowers governments and businesses to make critical decisions at the edge.
Tech Start-ups are Flourishing. There are immense opportunities for technology start-ups to grow their market presence through innovative products and services. To succeed these companies need to have a strong investment roadmap; maintain a strong focus on customer engagement; and offer technology solutions that can fulfil the global needs of their customers. Technologies that promote efficiency and eliminate mundane tasks for humans are the need of the hour. However, as the reliance on technology-led transformation increases, tech vendors are becoming acutely aware that they cannot be best-in-class across the different technologies that an organisation will require to transform. Here is where having a robust partner ecosystem helps. Partnerships are bringing innovation to scale in Asia.
We can expect Asia to emerge as a powerhouse as businesses continue to innovate, embed technology in their product and service offerings – and as tech start-ups continue to support their innovation journeys.
Ecosystm CEO Amit Gupta gets face to face with Garrett Ilg, President Asia Pacific & Japan, Oracle to discuss the rise of the Asia Digital economies, the impact of the growing middle class on consumerism and the spirit of innovation across the region.

Last week Microsoft announced the acquisition of Nuance for an estimated USD 19.7 billion. This is Microsoft’s second largest acquisition ever, after they acquired LinkedIn in 2016. Nuance is an established name in the Healthcare industry and is said to have a presence in 10,000 healthcare organisations globally. Apart from Healthcare, Nuance has strong capabilities in Conversational AI and speech solutions to support other industries. This acquisition is in line with Microsoft’s go-to-market roadmap and strategies.
Microsoft’s Healthcare Focus
Microsoft announced their Healthcare Cloud last year and this acquisition will bolster their Healthcare offerings and market presence. Nuance’s product portfolio includes clinical speech recognition SaaS offerings – Dragon Ambient eXperience, Dragon Medical One and PowerScribe One for radiology reporting – on Microsoft Azure. The acquisition builds on already existing integrations and partnerships that were in place over the years.

“Microsoft Cloud for Healthcare offers its solution capabilities to healthcare providers using a ‘modular’ approach. Given how diverse healthcare providers are in their technology maturity and appetite for change, the more diverse the ‘modules’, the greater the opportunities for Microsoft. This partnership with Nuance also brings to the table established relationships with EHR vendors, which will be useful for Microsoft globally.
The Healthcare industry continues to struggle as the world negotiates the challenges of mass vaccination. But on the upside, the ongoing Healthcare crisis has given remote care a much-needed shot in the arm. Clinicians today will be more open to documentation and transcription services for process automation and compliance. The acquisition of Nuance’s Healthcare capabilities will definitely boost Microsoft’s market presence in provider organisations.
However, Healthcare is not the only industry that Microsoft and Nuance are focused on. The Microsoft Cloud for Retail that was launched earlier this year aims to offer integrated and intelligent capabilities to retailers and brands to improve their end-to-end customer journey. Nuance has omnichannel customer engagement solutions that can be leveraged in Retail and other industries. As Microsoft continues to verticalise their offerings, they will consider more acquisitions that will complement their value proposition.“
Microsoft’s Focus on Conversational AI
Microsoft already has several speech recognition offerings, speech to text services, and chatbots; and they continue to invest in the Conversational AI space. They have created an open-source template for creating virtual assistants to help Bot Framework developers. In February, Microsoft announced their industry specific cloud offerings for Financial services, Manufacturing, and Non-Profit, and also introduced a series of AI and natural language features in Microsoft Outlook, Microsoft Teams, Microsoft Office Lens and Microsoft Office mobile to deliver interactive, voice forward assistive experiences.

“There is no slowing down in this space and the acquisition clearly demonstrates the vision that Microsoft is building with Nuance – a vendor that has made speech recognition, text to speech, conversational AI the foundation of the company. This is a brilliant move by Microsoft in the Conversational AI space and a win-win for both companies.
This move could also mark further inroads for Microsoft into the contact centre space. With Teams now being integrated into contact centre technologies, working with large customers using speech and conversational AI, Dynamics 365 could herald the start of more acquisitions for Microsoft to bolster a wider customer engagement vision.
The Conversational AI war is heating up and various other cloud vendors such as Google and AWS are starting to get aggressive and have made investments in recent years to enhance their Conversational AI capabilities. Google Dialogflow has been seeing rapid uptake and they now have deep partnerships with Genesys, Avaya, Cisco and other contact centre players. Microsoft coming into the game and acquiring a company with years of history and IP in the speech space, demonstrates how the cloud battle and the war between Google, Microsoft and AWS is heating up in the Conversational AI. All of a sudden you have Microsoft as a powerhouse in this game.”

Fundamentally, any change has to be about people. And the Digital Value Journey that we are introducing in the upcoming CXO Digital Leaders Dialogue Series is no different.
The journey covers five stages of development involving five capabilities. Still, without the engagement of the people who will be affected by the change, you will not make progress.
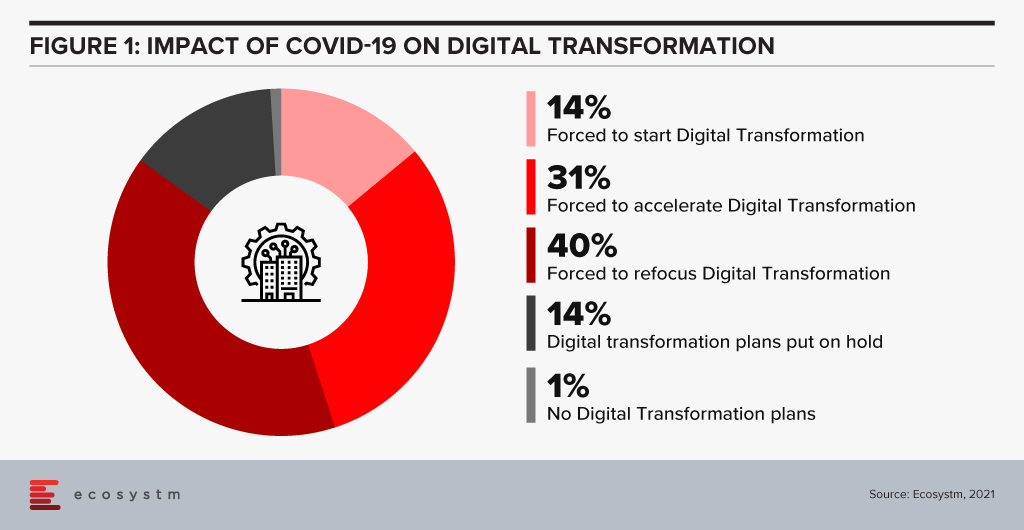
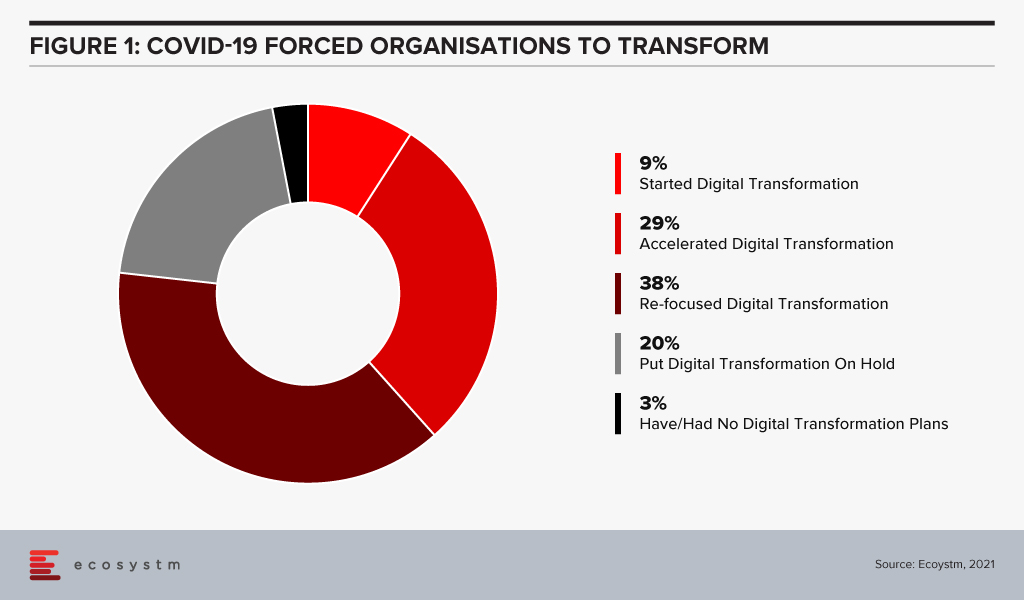
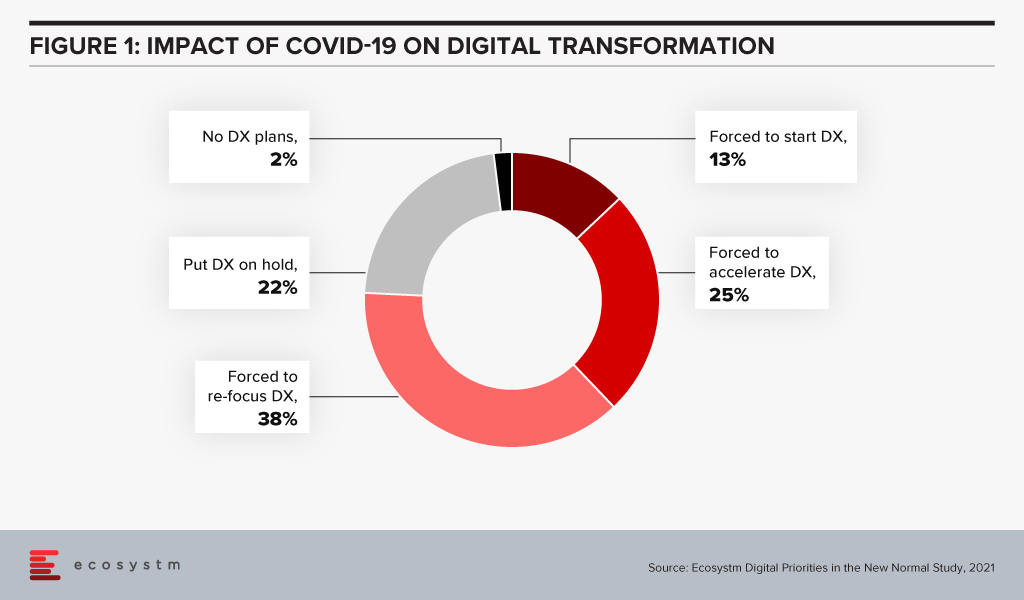
And the situation gets even more complicated when external events impact your business. Ecosystm research unearths the impact of COVID-19: over 90% of respondents changed their planned Digital Transformation in some way (Figure 1). These changes will inevitably mean that the anticipated behaviour changes from their teams no longer apply. Getting the affected people re-engaged with the new initiatives will not be a simple task.
For example, when an organisation I worked at integrated an information-as-a-service capability, we found that our most experienced people did not use the new capability! They preferred to stick with their paper sources as they were very good at finding what they needed.
So nothing is achieved unless someone acts differently. We can change the technology, and we can change the process, but unless the people who need to change do change, we will waste everything else we do.
The scale of the change really doesn’t matter. If people are not in a mindset where they are looking to improve, we waste our time.
In the example I mentioned earlier, our store teams used catalogues to look up parts and equipment for customers. Our most experienced people were amazing – they knew which of the myriad of catalogues was going to give them the best part. We had not convinced them that the real-time system, which the supplier updated constantly, was better for them than the last paper version they had received.
So, on the Digital Value Journey, travellers need to remain very aware of the state of mind of the people whose behaviour they expect to change. Getting and keeping these people engaged is essential to the change.
People’s Resistance to Change
But why do people resist (or just plain ignore) change? How clear are you on what is in it for them?
Recent research on people’s motivation by psychologists such as Daniel Kahneman highlights that people fear loss much more than they look forward to success. To overcome this loss aversion, we need to help people understand why their lives will be better once we’ve completed the change and specifically address their concerns.
When we were looking at replacing the paper catalogues, we told the store teams that they would be able to quickly and easily search across all the catalogues available to them to give the customer the best deal. We didn’t consider that the ability to find the right part was a source of pride for some of the team. It was a skill that our experienced team members had developed over the years, and they felt we were devaluing their expertise.
We need to help those affected by the change recognise the purpose of the change and what is in it for them. If there is nothing, then why change?
And leaving people behind on the change journey is never going to lead to success. Their clear understanding of the purpose of the change is essential to getting the anticipated benefits.
I’ve seen change activities launch with a hiss and a roar, but as the pressure comes on during the delivery stages, communication and collaboration drop away. Listening carefully and responding authentically is a necessary part of the journey right through implementation until our teams have fully adopted the changes. A change doesn’t end at the implementation of a capability.
And that catalogue replacement? The delivery team kept listening to the store teams and made some great changes that were asked for. Some of the changes we didn’t understand, but the store teams were adamant. And the development paid for itself in less than six months through increased and better quality sales.
How do digital leaders shift from providing a cost-focused to a value-focused service? At the CXO Digital Leaders Dialogue series, together with Best Case Scenario, we will be in discussion with leaders who will share their experiences on navigating their digital journey.
To learn more, or to register to attend, visit here

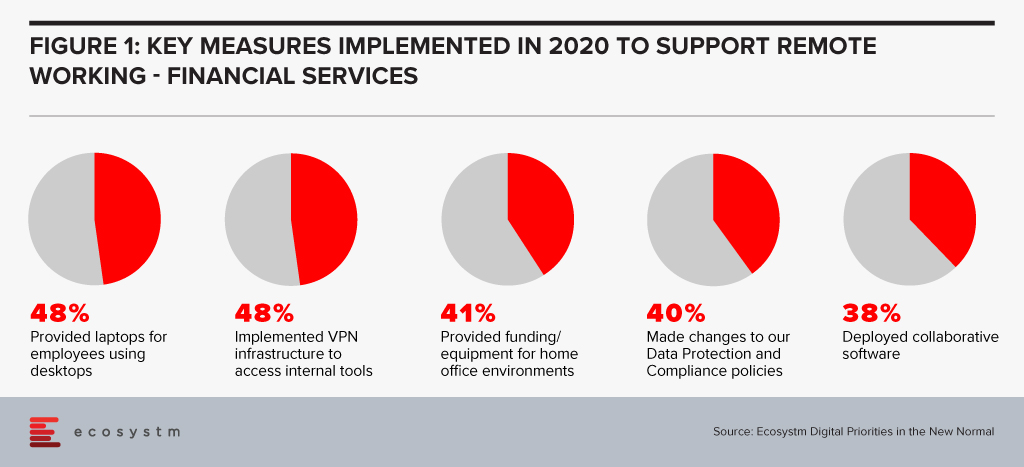
Financial services institutions made a fast switch to remote working when the pandemic forced widespread lockdowns across the globe. The adoption of remote working was nascent in the industry, and there was a need for a fast pivot by both the organisations and employees (Figure 1).
However, this has also exposed the industry to technology-related risks. Ecosystm Principal Advisor, Gerald Mackenzie says, “The move to a more virtualised working environment has been a trend taking shape for many years and like so many trends, it needed an impetus to make it a norm; in this case COVID-19.”
“Many, if not most, financial institutions have been shifting to more cloud-based and modularised Banking-as-a-Service (BaaS) models and these trends will only accelerate as we need to manage risks inherent in conducting financial services via remote working environments. For example, critical capabilities such as Advisor to Client communications need to be verifiable and auditable whether they are happening inside or outside of the office and I predict regulators will be pushing financial institutions to ensure these standards become the norm rather than the exception.”
Singapore Addresses Risk in the Financial Industry
To manage and mitigate risks that could emerge from the extensive remote working adoptions by FIs, The Monetary Authority of Singapore (MAS) and The Association of Banks in Singapore (ABS) jointly released a paper titled Risk Management and Operational Resilience in a Remote Working Environment. This is also in line with the previous collaboration between MAS and ABS in May 2020 to establish the Return to Onsite Operations Taskforce (ROOT). ROOT sought to strengthen and implement safe management and operational resilience measures as well as endorsement of industry best practices.
The paper seeks to create awareness amongst financial institutions on key remote working risks in the domains of technology, operations, security, fraud, staff misconduct, legal and regulatory risks. MAS encourages them to take pre-emptive measures to adopt good practices on managing risks.
Mackenzie adds, “Of course, some of the issues are difficult to solve. For example, staff accessing client data from their homes creates inherent vulnerabilities and the ways to ensure staff have suitable ‘in-home’ working environments to effectively manage these risks can be challenging and expensive. There are great opportunities for innovators to adapt solutions to solve these problems in what will undoubtedly be a growing investment area for many Financial Institutions.” The paper also examines various controls on the people and culture leveraging examples drawn from the experiences of ABS member banks to address evolving risks. For instance, FIs can implement security controls on staff infrastructure including their personal devices, verify in-person meetings against original documents, timely response strategies for recovery teams, legal risks and more.
To keep pace with the changing trends in technology deployment, risk management, and cybersecurity, MAS has been regularly working and engaging with experts to introduce guidelines, principles and best practices for financial institutions. In February, MAS issued a consultation paper proposing revisions to enhance the current requirements for enterprise risk management, investment risk management and public disclosure practices for insurers. Similarly, in January, MAS issued risk management best practice and standards to guide financial institutions in managing technology risk and maintain IT and cyber resilience.
Get insights on the technology areas in the Financial services industry that will see continued investments, as organisations get into the recovery phase.

Microsoft introduced a second Vertical Cloud offering, last week – this time turning the focus on Retail, after having launched Microsoft Cloud for Healthcare in October 2020.
The Microsoft Cloud for Retail aims to offer integrated and intelligent capabilities to retailers and brands to improve their end-to-end customer journey. It brings industry-specific capabilities to the Microsoft suite including Microsoft Azure, Microsoft Power Platform, Microsoft 365, and Microsoft Dynamics 365 – and is aimed at the growing need for “intelligent retail’. Microsoft’s partner ecosystem will also be involved in the new platform to address challenges in the sector and future proof the retail evolution.
In The Top 5 Retail & eCommerce Trends for 2021, Ecosystm notes that while retailers will focus on the shift in customer expectations, a mere focus on customer experience will not be enough this year. From the customer experience angle, they will strongly focus on omnichannel, catering to ‘glocal’ consumption, using location-based services, and improving both their onsite and online customer experience. They will also have to work on their supply chain and pricing capabilities, as distribution woes continue. These trends are seeing a deeper need for transformational technologies and leading cloud providers are introducing solutions targeted at the industry. Google has introduced its cloud retail solutions aiming to help retailers get more from data. Similarly, AWS has cloud offerings for the retail industry leveraging its retail domain experience and cloud deployment services.
Ecosystm Comments

“Global cloud vendors continue to “move up the stack” to provide more of the technology landscape for organisations. The focus of these tech giants is on adding unique value to customers by tailoring the combination of the different cloud services they can provide to specific industries. Providing the full-stack will mean higher customer retention rates – as the implementation time should be lower than traditional on-premises implementations. Microsoft has a diverse range of capabilities. Having a software company and implementation partner that can deliver the full stack of technology and business processes should improve the time to value for organisations.
But I see three key difficulties in implementing systems such as these:
- People adapting effectively to use the new processes
- Migrating enough high-quality data to leverage the new capabilities
- Integrating the new capabilities into an organisation’s existing landscape.
This is why it is likely that initial use will come from Microsoft’s existing Retail customers as they expand the range of services they use. New adopters of these Microsoft solutions will find that much of the complexity and cost of implementing a new business solution will remain.
However, these value-added cloud services open access to smaller organisations. If Microsoft is able to work with their partners to simplify the implementation of these capabilities, it will allow smaller organisations to access these complex capabilities affordably.“

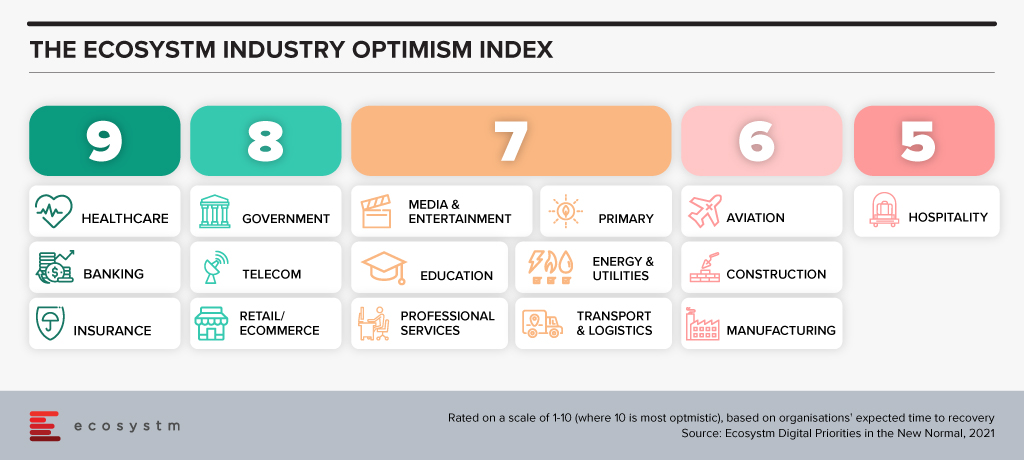
“The Ecosystm Digital Priorities in the New Normal Study aims to determine how optimistic industries are about successfully negotiating these uncertain times (Figure 1). The industries that are rated the most optimistic fall into two clear categories. In the first category, there are industries, such as Healthcare that had to transform urgently – mostly in an unplanned manner. This has led to a greater appetite for change and optimism in these industries. Then there are industries, such as Retail, that had some time to re-focus their technology roadmap when the crisis hit. These industries have a strong customer focus and had started their digital journeys before the pandemic.
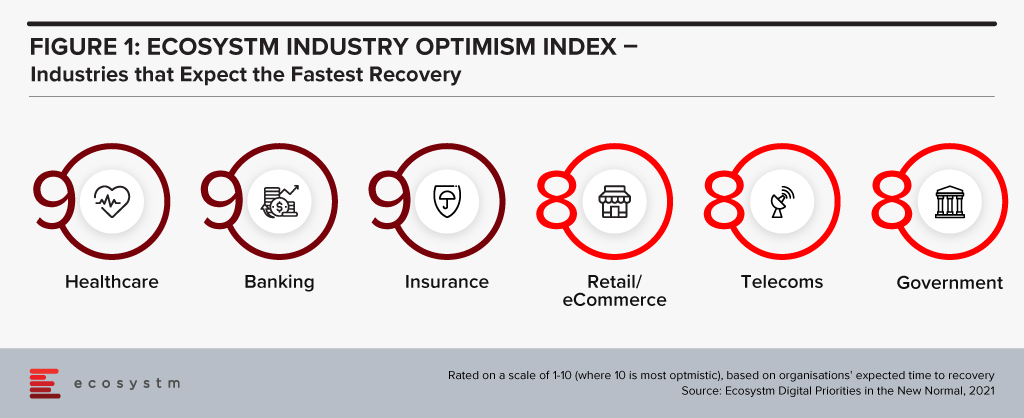
Microsoft’s industry focus appears to be spot-on. Their first two vertical clouds target enterprises that have had to – and will continue to – pivot. The ‘modular’ approach taken in the Microsoft Cloud for Healthcare offering allows providers to choose the right capability for their organisation – whether it is workflow automation, patient engagement through virtual health, collaboration within care teams or better clinical and operational insights. As healthcare organisations across the world negotiate the challenges of mass vaccination, they may well find themselves leveraging these industry-specific capabilities as they revamp their workflows, processes, and data use.”
Get to know the right research, insights and technologies for you to be one step ahead in this new world of retail in our top 5 retail trends for 2021 that represent the most significant shifts in 2021

In 2009 one of the foremost Financial Services industry experts was giving my team a deep dive into the Global Financial Crisis (GFS) and its ramifications. According to him, one of the key reasons why it happened was that most people in key positions in both industry and government had probably never seen a full downturn in their careers. There was a bit of a hiccup during the dot com bust but nothing that seriously interrupted the long boom that began somewhere in 1988. They had never experienced anything quite like 2008; so they never imagined that such a crisis could actually happen.
Similarly, 2020 was an unprecedented year – in our lives and certainly for the tech industry. The GFC (as the name suggests) was a financial crisis. A lot of people lost their jobs, but after the bailouts things went largely back to normal. COVID-19 is something different altogether – the impact will be felt for years and we don’t yet know the full implications of the crisis.
While we would like to start 2021 with a clean slate and never talk about the pandemic again, the reality is that COVID-19 will shape what we will see this year. In the first place it looks like the disease will still be around for a substantial part of the year. Secondly, all the changes it has brought in 2020 with entire workforces suddenly moving to operating from home will have profound implications for technology and customer experience this year.
As we ease into 2021, I look at some of the organisational and technology trends that are likely to impact customer experience (CX) in 2021.
#1 All Business is Now eBusiness
COVID-19 has ensured that the few businesses which did not have an online presence became acutely aware that they needed one. It created a need for many businesses to quickly initiate eCommerce. Forbes reported a 77% increase in eCommerce infrastructure spending YoY. This represents about 4 years of growth squeezed into the first 6 months of 2020!
From a CX point of view there is going to be far more interaction with brands and products through online channels. This is not just about eCommerce and buying from a portal. It is also about using tools like Instagram, Facebook and other social media platforms more widely. It is about learning to interact with the customer in multiple ways and touching their journeys at multiple points, all virtually using the web – mostly the mobile web.
Ecosystm research shows that almost three out of four companies have decided on accelerating or modifying the digitalisation they were undergoing (Figure 1). It is fair to expect that this gives a further boost to moving to the cloud. For the customer it will mean being able to access information in many new ways and connect with products, services, brands at multiple points on the web.
Since interacting with the customer at multiple points is new for most services, I foresee a lot of missed opportunities as companies learn to navigate a completely different landscape. Customers pampered by digitally native organisations often react harshly to even a small mistake. It will become critical for companies to not just become a bigger presence online but also to manage their customers well.
New solutions such as Customer Data Platforms (CDP), as opposed to CRM will become common. Players who are into Customer Experience management are likely to see huge business growth and new players will rapidly enter this space. They will promise to affordably manage CX across the globe, leveraging the cloud.
#2 Virtual Merges with Real
Virtual and Augmented Reality are not new. They have been around for a while. This will now cross the early adoption stage and is likely to proliferate in terms of use cases and importance.
AR/VR has so far been seen mainly in games where one wears an unwieldy – though ever-improving – headset to transport oneself into a 3D virtual world. Or in certain industrial applications e.g., using a mobile device to look at some machinery; the device captures what the eye can see while providing graphical overlays with information. In 2021 I expect to see almost all industrial applications adopting some form of this technology. This will have an impact on how products are serviced and repaired.
For the mainstream, 2020 was the year of videoconferencing – as iconic as the shift to virtual meetings has been, there is much more to come. Meetings, conferences, events, classrooms have all gone virtual. Video interaction with multiple people and sharing information via shared applications is commonplace. Virtual backgrounds which hide where you are actually speaking from are also widely used and getting more creative by the day.
Imagine then a future where you get on one of these calls wearing a headset and are transported into a room where your colleagues who are joining the call also are. You see them as full 3D people, you see the furniture, and the room decor. You speak and everyone sees your 3D avatar speak, gesture (as you gesture from the comfort of your home office) and move around. It will seem like you are really in the conference room together! If this feels futuristic or unreal try this or look at how the virtual office can look in the very near future.
While the solutions may not look very sophisticated, they will rapidly improve. AR/VR will start to really make its presence felt in the lives of consumers. From being able to virtually “try” on clothes from a boutique to product launches going virtual, these technologies will deeply impact customer experience in 2021 and beyond
In the immortal words of Captain Kirk, we will be going where no man has gone before – enabled by AR / VR.
#3 Digital CX will involve Multiple Technologies
AI, IoT and 5G will continue to support wider CX initiatives.
The advances that I have mentioned will gain impetus from 5G networking, which will enable unprecedented bandwidth availability. To deliver an AR experience over the cloud, riding on a 5G network, will literally be a game changer compared to the capabilities of older networks.
Similarly, IoT will lead to massive changes in terms of product availability, customisation and so on. 5G-enabled IoT will allow a lot more data to be carried a lot faster; and more processing at the edge. IoT will have some initial use cases in Retail, Services and other non-manufacturing sectors – but perhaps not as strongly as some commentators seem to indicate.
AI continues to drive change. While AI may not transform CX in 2021, this is a technology which will be a component of most other CX offerings, and so will impact customer experience in the next few years. In fact, thinking of businesses in 2025 I cannot believe that there will be a single business to customer (B2C) interaction which will not feature some form of AI technology.
I’d be interested to hear your thoughts on the technologies which will impact CX in 2021 – Connect with me on the Ecosystm platform.

































