In the rush towards digital transformation, individual lines of business in organisations, have built up collections of unconnected systems, each generating a diversity of data. While these systems are suitable for rapidly launching services and are aimed at solving individual challenges, digital enterprises will need to take a platform approach to unlock the full value of the data they generate.
Data-driven enterprises can increase revenue and shift to higher margin offerings through personalisation tools, such as recommendation engines and dynamic pricing. Cost cutting can be achieved with predictive maintenance that relies on streaming sensor data integrated with external data sources. Increasingly, advanced organisations will monetise their integrated data by providing insights as a service.
Digital enterprises face new challenges – growing complexity, data explosion, and skills gap.
Here are 5 ways in which IT teams can mitigate these challenges.
- Data & AI projects must focus on data access. When the organisation can unify data and transmit it securely wherever it needs to, it will be ready to begin developing applications that utilise machine learning, deep learning, and AI.
- Transformation requires a hybrid cloud platform. Hybrid cloud provides the ability to place each workload in an environment that makes the most sense for the business, while still reaping the benefits of a unified platform.
- Application modernisation unlocks future value. The importance of delivering better experiences to internal and external stakeholders has not gone down; new experiences need modern applications.
- Data management needs to be unified and automated. Digital transformation initiatives result in ever-expanding technology estates and growing volumes of data that cannot be managed with manual processes.
- Cyber strategy should be Zero Trust – backed by the right technologies. Organisations have to build Digital Trust with privacy, protection, and compliance at the core. The Zero Trust strategy should be backed by automated identity governance, robust access and management policies, and least privilege.
Read below to find out more.
Download The Future of Business: 5 Ways IT Teams Can Help Unlock the Value of Data as a PDF

It’s been a tough couple of years for British Airways (BA). 2017 saw an IT failure that resulted in 726 flights getting cancelled and 75,000 passengers being stranded on a busy holiday weekend. The fallout from this incident was around GDP 80 million in compensation paid to passengers and an almost immediate 4% drop in the share price.
Then, in 2018, the British carrier fell victim to a security breach in which around 500,000 people had their personal data, including their credit card details, stolen by hackers.
It is this breach that British Airways is now told that it will be fined 183 million British Pounds for. The fine was announced by the British Information Commissioner’s Office (ICO), and if it stands, it will be the biggest fine ever imposed for a data breach in the UK or elsewhere in Europe. In fact, the fine dwarfs previous fines issued up until now.
The biggest fines issued by the ICO in the UK were to Facebook and Equifax – both of whom were fined GBP 500,000.
Facebook’s fine was for the notorious Cambridge Analytica data scandal, where the information of 87 million Facebook users was shared with the political consultancy through a quiz app that collected data from participants as well as their friends without their consent.
Equifax Ltd. fine was for something more similar to the British Airways case: In May 2017, hackers stole personal data including names, dates of birth, addresses, passwords, driving licences and financial details of 15 million UK customers. In its ruling, the ICO said that Equifax had failed to take appropriate steps to ensure the protection of this sensitive data despite warnings from the US government.
But these fines were all from before the General Data Protection Regulation (GDPR) came into effect. Now, under the new rules, fines can be as high as EUR 10,000,000 or 2% of total global annual turnover for the previous year (whichever is higher) for lesser data breach incidents. For significant data breaches and non-compliance, the fines can be double that: EUR 20,000,000 or 4% of total global annual turnover (whichever is higher).
British Airways’ GBP 183 million fine is the equivalent of 1.5% of its turnover in 2017. Had the ICO gone for the maximum limit, the fine could have been as much as GBP 489 million.
A lot can still happen before the fine is finally issued, and BA is likely to dispute the decision in court (Willie Walsh, the CEO of BA’s parent company, IAG, has said they will). But even if the fine ends up being significantly lower, there are obvious lessons to be learned from this case:
- “People’s personal data is just that—personal.” These were the words spoken by Elizabeth Denham, the ICO Information Commissioner, in response to media enquiries on the fine. In other words: companies will need to take data privacy extremely seriously from now on or expect very hefty fines.
- Attitude matters. British Airways chairman and chief executive, Alex Cruz, said in a statement that BA was “…surprised and disappointed in this initial finding from the ICO. British Airways responded quickly to a criminal act to steal customers’ data. We have found no evidence of fraud/fraudulent activity on accounts linked to the theft. We apologize to our customers for any inconvenience this event caused.”
Although we can’t know this for certain, the response may reflect what could be described as an “attitude problem” in how BA has been dealing with the ICO: a whiff of arrogance, blaming the breach on criminal hackers and failing to accept any blame or real responsibility for the incident.
We know from other GDPR cases in other countries that any failure to cooperate with the authorities may result in larger fines. Full transparency, full cooperation and accepting responsibility are the way to go. If it’s your data, then the buck stops with you.
- The risks associated with IT cutbacks just went through the roof. The operating losses following the financial crises of 2008 made the carrier slash back its IT budgets (as well as other “expenditures”). Airlines, in general, are notorious for under-spending on IT, but when combining that with further cutbacks on IT expenditure, disaster may ensue. BA’s recent IT related woes may or may not be a direct result of under-spending on IT, but in the court of public opinion, this connection has been made.
In any case, with the new fine regime under the GDPR, the risks associated with under-spending on IT – and on IT security in particular – have now gotten substantially bigger.
More than ever, the notion that IT is an expenditure that can be cut back on is a false economy.
On 17 May 2019, the New Zealand Prime Minister Jacinda Ardern and the Singapore Prime Minister Lee Hsien Loong signed a formal arrangement, to step up collaboration in the areas of trade, defence, cybersecurity, science and technology, and arts and culture.
To strengthen cybersecurity, the Cyber Security Agency of Singapore (CSA) and the National Cyber Policy Office (NCPO) of New Zealand inked an agreement on information sharing, cybersecurity and capacity building in the region. A new Cyber Security Arrangement will support greater information exchange, including through an annual cybersecurity dialogue between the two countries. The aim of the agreement is to increase information exchange, prevent incidents and threats and follow best practices on data, infrastructure, and systems protection.
Commenting on the announcement Ecosystm Principal Advisor, New Zealand-based Jannat Maqbool, said, “Engaging internationally on cybersecurity research and initiatives is fundamental given the trans-boundary nature of the cyberspace. As both nations become more digitised and connected, a collaboration will enable each to leverage strengths in key areas to develop a multi-pronged approach to cybersecurity. Both countries will also be in a better position to weigh in on the development of rules-based international order for cyberspace.”
Echoing these comments, Ecosystm Board Advisor, and former Global Head, Digital Development Unit at the World Bank, Randeep Sudan explains how cybersecurity is critical to the growth and development of the digital economy. “Mitigating cyber risks will require coordinated action by multiple stakeholders, including governments, the private sector, academia, and non-governmental organisations,” Sudan says. These bilateral and multilateral G2G partnerships are, therefore, an essential piece in tackling cyber threats. “Given that Singapore and New Zealand are leading players in cyberspace, a G2G collaboration between them will offer learnings of immense value to other governments,” Sudan continues.
Due to Ecosystm’s own close ties with New Zealand, and considering that we are headquartered in Singapore, we are ourselves actively engaged in promoting the dialogue between New Zealand and Singapore. Ecosystm CEO Amit Gupta and Chief Operating Officer, Ullrich Loeffler are in New Zealand this week to participate in Techweek New Zealand (an annual initiative to promote and build awareness for new technologies and innovation in New Zealand) to meet key stakeholders and attend industry events.
 |
 |
Commenting on the sidelines of Techweek, Amit Gupta gave his thoughts on the agreement, “Both New Zealand and Singapore are in hyper-innovation mode at the moment. With the advent of Blockchain and AI especially spurring the growth of the Fintech ecosystem in New Zealand, there is strong potential gains in engaging with the already thriving Singapore Fintech ecosystem.”
New Zealand and Singapore are not only model free markets, but also have been key proponents of data privacy over the years, an area that requires a serious look, as we start to apply new emerging technologies such as AI. “There is an opportunity for these two forward-looking nations to take it a step further to build an actionable Data Privacy Corridor to streamline the Fintech collaboration between them,” Gupta added. “With New Zealand being an export economy and Singapore, a strong services economy, this would enable a much more seamless collaboration between these two countries.”
The collaboration does not end at cybersecurity and Fintech. As part of the partnership, a joint work programme is being negotiated, starting with two flagship collaborations – an advanced data science research platform to build New Zealand’s data science capability; and a food and nutrition cooperative science programme with a focus on ‘future foods’. Both countries have different areas of expertise, and collaborative measures such as these, give them an opportunity to share best practices that will prove mutually beneficial.
The NCSC’s first ‘UK cyber survey’ published alongside global password risk list. The UK government’s cybersecurity organisation National Cyber Security Centre (NCSC) provides cybersecurity support and guidance to the private and public sectors.
The survey identified exploitable gaps in personal level security management. The study was carried out between November 2018 and January 2019 and revealed that 89% of the respondents used the Internet and only 15% acknowledged a greater understanding of personal security measures.
The NCSC also published an analysis of the 100,000 most commonly used passwords that have been accessed by third parties in global cyber breaches. The analysis shows that less than half of the respondents do are not concerned about the strength of passwords for their emails and online accounts. Some examples of commonly used passwords used by people rely on their own names, Premier League football teams, musicians and fictional characters for inspiration.
This general lack of understanding of the cyber world can be harmful to individuals but can be devastating to organisations. A chain is no stronger than its weakest link, and insecure passwords may pose a serious security risk to an organisation. “We rely on passwords in all facets of our online world, so this presents a massive risk to anyone taking short-cuts. Unfortunately, if organisations are not prepared, and allow the use of similarly insecure passwords, the flow on effect of a breach can escalate rapidly” says Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm “The passwords in the above list are very weak. Even without the knowledge provided in the list, a hacker would be able to crack these passwords in seconds with the right tools. Even password complexity cannot always protect an organisation. What about a user that re-uses a complex password repeatedly, and that password is part of a breach? That puts all of the organisation’s logins at risk”.
There are some additional steps that system administrators and IT professionals need to consider when it comes to securing passwords and managing logins.
The global Ecosytsm Cybersecurity & Data Privacy study found the most common controls organisations implement to manage data access.
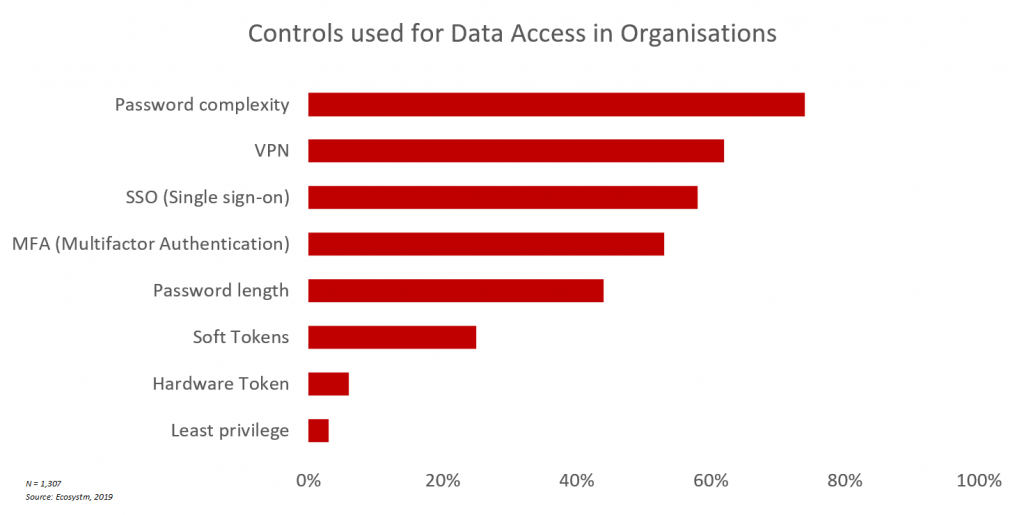
“The main step being used currently is ensuring MFA is enabled wherever possible. While not a perfect solution, it provides a circuit breaker for the most common types of attacks that would get anyone using insecure passwords into trouble” says Woerndle.
The NCSC hopes to reduce the risk of further breaches by building awareness of how attackers use easy-to-guess passwords, or those obtained from breaches and help guide developers and system administrators to protect their users. NCSC has framed guidelines covering multiple aspects of managing and maintaining security on its website.
Ultimately this problem will not go away until we find a genuine replacement for passwords. The pure scale of growth in the number of systems and applications that all users, both at a personal and on a professional level, have access to, makes password management complex and frustrating. While focusing on how to strengthen your passwords and other easy steps to avoid a cyber attack, may be a good start, it will not be enough, as long as systems and applications are dependent on passwords for better security.
The Changing Shape of Asia’s Cybersecurity Landscape
The latest in our Leaders BreakFirst series. Following the launch of our Cybersecurity and Data Privacy study, Ecosystm is delighted to share the insights from almost 7000 deployments globally.Featuring two of Ecosystm’s cybersecurity and data privacy experts on one stage- Claus Mortensen and Carl Woerndle, this session will highlight the findings from our Cybersecurity & Privacy research.
The cyber world is ever growing and in this vast world, no business is 100% safe & insured against cyber attacks. With so many threats out there incurred every minute, it is hard to detect each one and prevent them all. In this world of disruptive technology if organisations want to remain competitive, keeping their IT infrastructure security up-to-date is a must.
The Government, cybersecurity experts & other groups are taking various initiatives to spread awareness on cyber attacks but despite these attempts, organisations fail to take their cybersecurity seriously, we may say this is due to lack of awareness, increase in expense or companies simply not wanting to take the pains to prevent breaches.
“When things are going well, it is hard to sell the message of security to stakeholders and get support from across the business. When things are not going so well (e.g. you’ve had a breach), it means high pressure and a lot of focus on your performance” says Alex Woerndle, Principal Analyst Cybersecurity, Ecosystm.
Cyber attacks happen without notice. While there are many cyber experts present to help and provide consultation to the organisations, knowing beforehand about the attacks and strengthening your cybersecurity will safeguard you against serious ramifications.
Let’s Understand – What is a Cyber Attack?
A cyber attack is a deliberate attempt by an individual or a community working together to tap into an existing or a newly discovered vulnerability in the system, network, firmware or software resulting in complete control or gaining information from the victim’s system. While measuring the ill-effects of a cyber attack, we can say that with access to critical data one can exploit sensitive information, identity and may cause serious damage to an organisation or personal identity. Sometimes, a cyber attack is also referred to as computer network exploitation (CNE) or a computer network attack (CNA).
The other common terms used in association with a cyber attack are threat, vulnerability, and risk. Often these terms are mingled together in our day-to-day usage, but they all mean something different. Let’s try to uncover the basic difference between a threat, a vulnerability, and a risk.
A threat can be explained as an activity to exploit a weakness in a system, to cause harm or reveal the underlying assets. It always involves a person responsible for performing threat actions to impact the system’s security known as a threat actor.
A vulnerability is an unknown system flaw or a known weakness that could potentially be exploited by a person also known as a hacker. In other words, it can be known or unknown issues within a system or its software that can be exploited by hackers.
Together, when a threat acts and exploits a vulnerability, this may result in the development of a situation known as a risk. A risk could lead to potential loss or damage to a business.
Understanding threats, vulnerabilities, risks and other components will help you to act against cyber attacks but this may raise another question on why someone would try to harm your business.
So Why do Cyber Attacks Happen?
The people behind a cyber attack could be hackers, a team or a dark web organisation who work with an ulterior motive to commit a digital crime or to gain access to one’s system through a cyber attack. Collectively we may refer to them as cyber criminals. Cyber criminals try to identify vulnerability to crackdown a system.Below are some of the common reasons why a cyber attack happens.
Financial Gain
This is one of the most well-known types of cyber crime. The motive of cyber criminals here is to get easy access to money and the ways they make this happen is through frauds, demands, data breaches or direct attacks. What attackers try to steal are the business’ financial details or sensitive data/intellectual property, customer financial data or databases, staff or client credentials. By gaining access to these, the attackers get in a position to easily access a secured system and exploit it for their financial gains.
Hacktivism – Political or Social
Hacktivism is an activity involving anonymous organisations breaking into an organisation’s IT infrastructure for political or social reasons. Hacktivists mount cyber attacks to access information that can damage the intended target or perform activities to hurt or lower the reputation of certain bodies. Government and political bodies are often the targets of hacktivism.
Intellectual Challenge
Cyber world experts are sometimes challenged by the thrill of hacking or may develop a personality living in a virtual world pushing them to hack into a network with an intention of identifying system vulnerabilities. Generally, hackers are referred to as people with bad motives but hackers are not necessarily criminals as some of them help organisations to test systems, recognise backdoors, loopholes or vulnerabilities in a system which is termed as ‘white hat’ hacking. Knowing the vulnerabilities in the existing IT infrastructure and services may protect organisations from some serious future consequences.
Espionage
Stealing classified information, sensitive data or intellectual property from a government entity or a competitive organisation is a common form of espionage attack. The examples of an espionage attack could be stealing trade and military secrets or technologies or potential system flaws which may pose an influential threat to a nation.
Organised Cyber Crime
Digital technology has empowered individuals with some serious fire-power. IMs and chat technology have made it easy for individuals to form teams or an organisation to commit crimes on the web. Sometimes several groups form communities to commit a serious cyber crime – planned, coordinated and conducted together at a macro level.
Disruption
Aiming to disrupt business, or the operations of critical infrastructure, can be undertaken just to demonstrate security weaknesses, the hacker’s general disapproval for the business, or even to cause extensive operational, financial and physical damage to their target.
The Vulnerabilities that a Business can Experience
Data breaches occur every minute and unknown threats and vulnerabilities always pose a risk for a business. To stay protected, it is always better to know and understand the types of threats or vulnerabilities that a business can experience rather than later raising questions on how the attackers got in.
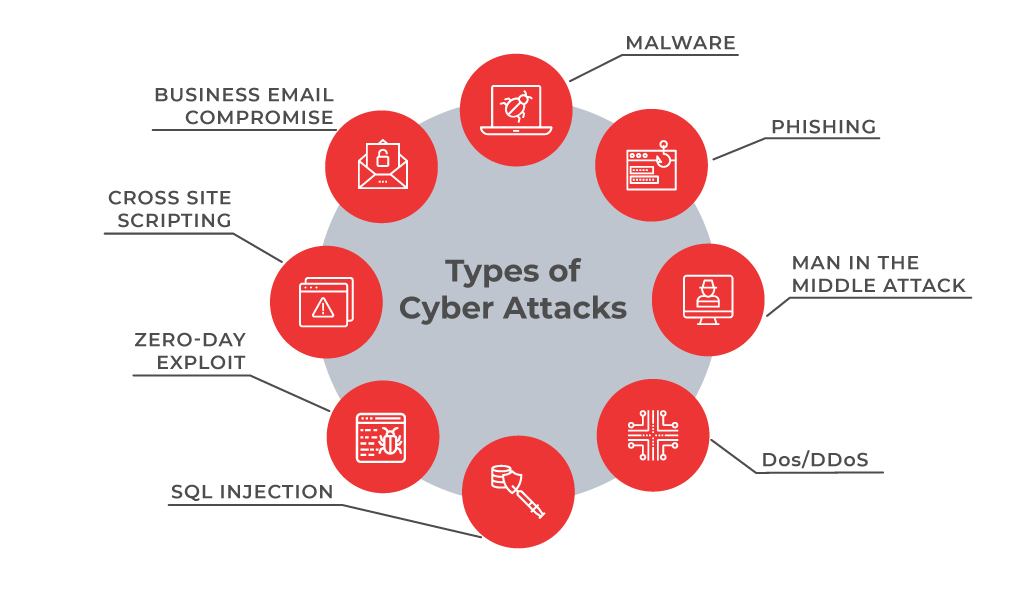
- Malware . A malware is a type of cyber attack where malicious software is installed on the victim’s systems through executable files usually without the user’s knowledge. Malware includes malicious software, including spyware, ransomware, viruses, and worms. After installation, a malware can keep track of the user’s activity or can trigger codes resulting into access to sensitive information, login details, credit cards or intellectual properties by the hacker.
- Phishing. Phishing refers to spoofing or deceptive communications activities performed by the attackers that appear to originate from a credible source such as emails, messages, legitimate websites that are disguised. Through phishing, attackers try to fetch sensitive information, user details, credit card numbers or make fraudulent attempts.
- Man-in-the-middle attack. These attacks happen with relaying or altering the communication channels. This can be communication between organisations and cloud server or over unsecured networks.
- DoS/DDoS. A DoS/DDoS attack aims at flooding the target website with overwhelming traffic to exhaust resources and bandwidth of the system. These are not to bring down a website but to breach a security perimeter and smoke out the online systems. This can reduce a user base or may bring down the entire network.
- SQL Injection. This is injecting a nefarious code or statements into SQL queries or a database server to extract information from the database or to take a data dump of the complete database.
- Zero-day exploit. Zero-day is a software security flaw which is known to the software developers. Attackers try to exploit a vulnerability before a patch or solution is implemented to capture the system with known weaknesses.
- Cross Site Scripting. XSS attacks occur when a web app sends malicious code in the form of a side script to another user thus bypassing access controls of the site to same as the origin.
- Business Email compromise. This is an attack to spoof business emails and gain illegal access to company accounts and ids to defraud the company or its employees.
According to Woerndle, “Nowadays, most of the reported attacks appear to be email-focused either with the intention to encrypt the infected systems to demand payment of a ransom for the keys (i.e. ransomware), to steal credentials (subsequently used for further attacks on other systems and applications) or to steal information that can be sold for profit on the black markets. “
Some of the World’s Largest Data Breaches
Cyber attacks have become a repeated theme every year and we hear quite often about the data breaches. Here’s a visualisation of some of the world’s largest data breaches that have occurred in the past few years.
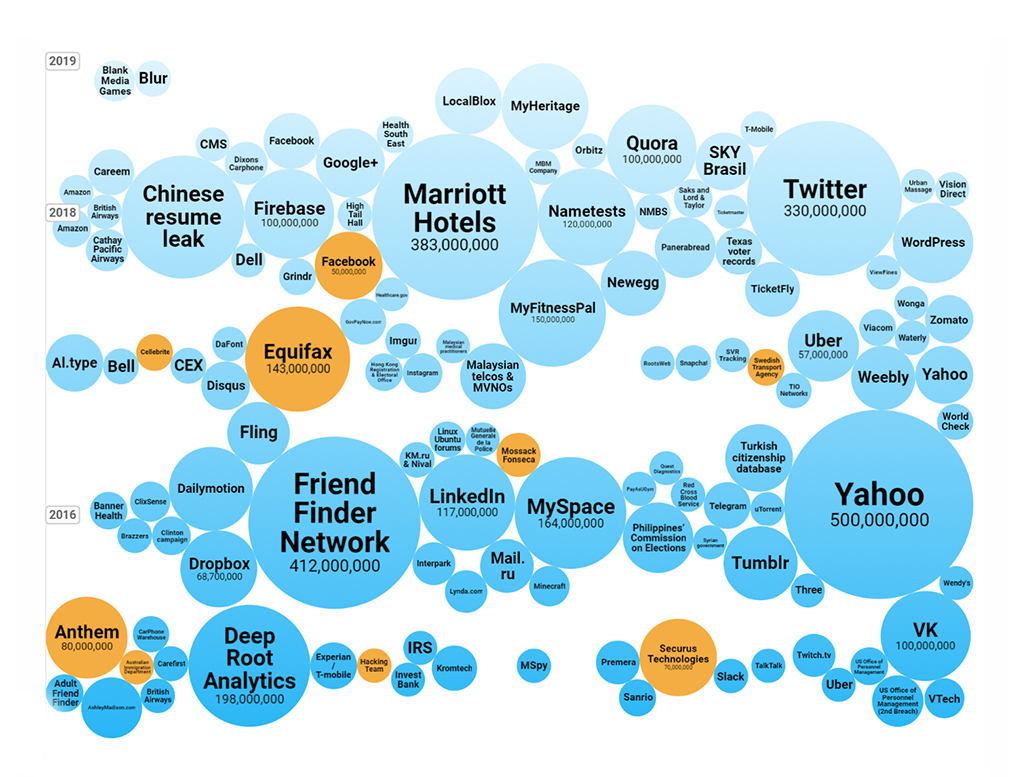
Source: Informationisbeautiful-worlds biggest data breaches hacks
How to Prevent Cyber Attacks?
To minimise cyber attacks, businesses can put some counter-measures in place. It is a smart move to be prepared for serious circumstances and act reactively with security measures.
Secure assets. It is always considered a security best practice to keep your systems and infrastructure updated with latest security patches and updates which are released from vendors or manufacturers on a regular basis.
Conduct threat assessment. Vulnerabilities can arise within your own system or potentially from other sources which are not directly under your control, but they can be identified if you are aware. Perform regular due diligence of your system or network security.
Stay informed on threats. News articles, software companies, cyber security organisations often release information on threats and vulnerabilities that can help you stay informed and act against threats.
Formulate steps to avoid threats. Training and regular information to organisations and employees can prevent many attacks from happening. If your users or employees are aware and informed they can escape the threats. Keep strong passwords, encrypt sensitive information, safeguard accounts, use firewalls to prevent attacks.
Plan an incident response. Create plans and approaches to react against a cyber attack to manage and limit the damage. Always keep your systems backed up online/offline and prepare your IT team to deal with it. You may also take advice or may hire experts to strengthen your infrastructure security.
It is rightly believed that prevention is better than cure. Speaking on the subject, Alex Woerndle, conveys that “the fundamentals are always the most critical starting points – focus on your system and application hardening and patching processes, deploy and actively maintain endpoint protections (e.g. anti-virus), restrict the permissions users have on their devices and invest in regular training and awareness for all staff. Beyond that, ensure all systems are backed up regularly, and deploy (and encourage all users to apply in their everyday lives) multi-factor authentication wherever possible.”
Considering the recent information security breaches, governments around the world are actively forming committees and taking measures to fight against cyber attacks. The governments of various nations have published some guidelines and measures to prevent cyber attacks.
The NIST Cybersecurity Framework, US, provides a policy framework of computer security guidance for organisations to assess and improve their ability to prevent, detect, and respond to cyber-attacks. The framework has been translated into many languages and is used by various governments and organisations across the world.
The Australian Government (via Australian Signals Directorate – part of Defence) has published some very good guidelines – called the ‘Essential 8’ and ‘Strategies to Mitigate Cyber Security Incidents’. The Essential 8 are a very user-friendly guide for businesses and provide protection against 80% of the most common cyber attacks
The UK Government has also come out with very useful information to help organisations.
Recently, Singapore opened a new cybersecurity school and the Ministry of Defence (MINDEF), is planning to hire security experts for their cyber defense strategy.
Cybersecurity is a challenging area and is a very broad discipline that requires skills across technology, forensics, business management, risk and compliance, education, communication, technical support, and others.
Negligence can impair reputation and lead to commercial losses but by understanding the security aspects, one can become aware of the potential threat and be in a better position to counteract it, or even preempt it.
This is just a glimpse to give you some insights into areas of cybersecurity and what goes under the surface. For specific details, you may get in touch with us or speak with a cybersecurity expert.