Ecosystm research reveals a stark reality: 75% of technology leaders in Financial Services anticipate data breaches.
Given the sector’s regulatory environment, data breaches carry substantial financial implications, emphasising the critical importance of giving precedence to cybersecurity. This is compelling a fresh cyber strategy focused on early threat detection and reduction of attack impact.
Read on to find out how tech leaders are building a culture of cyber-resilience, re-evaluating their cyber policies, and adopting technologies that keep them one step ahead of their adversaries.
Download ‘Cyber-Resilience in Finance: People, Policy & Technology’ as a PDF

The Banking, Financial Services, and Insurance (BFSI) industry, known for its cautious stance on technology, is swiftly undergoing a transformational modernisation journey. Areas such as digital customer experiences, automated fraud detection, and real-time risk assessment are all part of a technology-led roadmap. This shift is transforming the cybersecurity stance of BFSI organisations, which have conventionally favoured centralising everything within a data centre behind a firewall.
Ecosystm research finds that 75% of BFSI technology leaders believe that a data breach is inevitable. This requires taking a new cyber approach to detect threats early, reduce the impact of an attack, and avoid lateral movement across the network.
BFSI organisations will boost investments in two main areas over the next year: updating infrastructure and software, and exploring innovative domains like digital workplaces and automation. Cybersecurity investments are crucial in both of these areas.
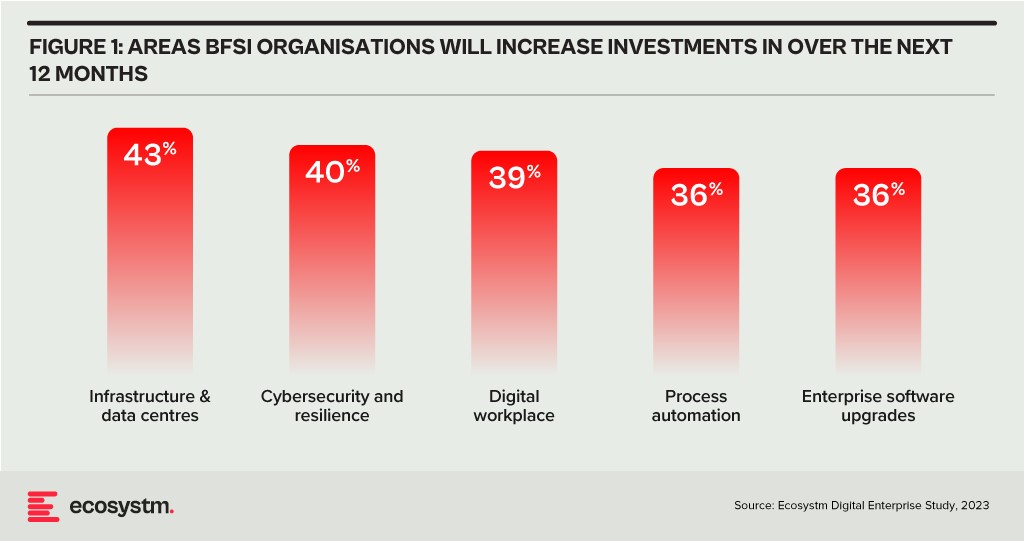
As a regulated industry, breaches come with significant cost implications, underscoring the need to prioritise cybersecurity. BFSI cybersecurity and risk teams need to constantly reassess their strategies for safeguarding data and fulfilling compliance obligations, as they explore ways to facilitate new services for customers, partners, and employees.
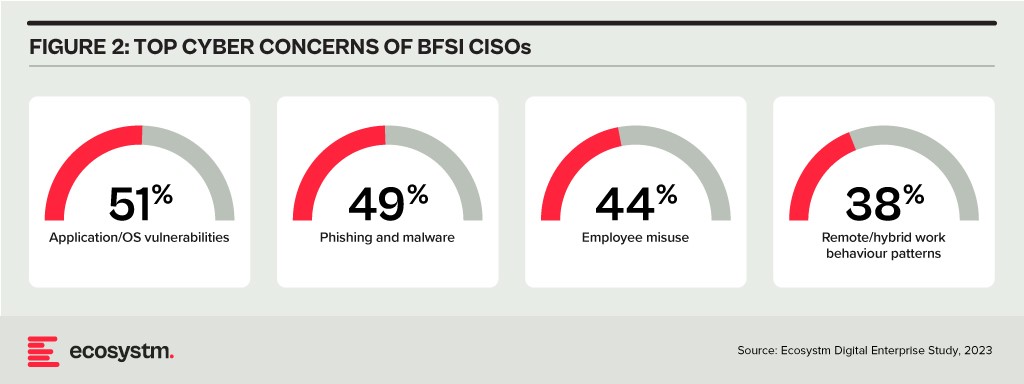
The primary concerns of BFSI CISOs can be categorised into two distinct groups:
- Expanding Technology Use. This includes the proliferation of applications and devices, as well as data access beyond the network perimeter.
- Employee-Related Vulnerabilities. This involves responses to phishing and malware attempts, as well as intentional and unintentional misuse of technology.
Vulnerabilities Arising from Employee Actions
Security vulnerabilities arising from employee actions and unawareness represent a significant and ongoing concern for businesses of all sizes and industries – the risks are just much bigger for BFSI. These vulnerabilities can lead to data breaches, financial losses, damage to reputation, and legal ramifications. A multi-pronged approach is needed that combines technology, training, policies, and a culture of security consciousness.
Training and Culture. BFSI organisations prioritise comprehensive training and awareness programs, educating employees about common threats like phishing and best practices for safeguarding sensitive data. While these programs are often ongoing and adaptable to new threats, they can sometimes become mere compliance checklists, raising questions about their true effectiveness. Conducting simulated phishing attacks and security quizzes to assess employee awareness and identify areas where further training is required, can be effective.
To truly educate employees on risks, it’s essential to move beyond compliance and build a cybersecurity culture throughout the organisation. This can involve setting organisation-wide security KPIs that cascade from the CEO down to every employee, promoting accountability and transparency. Creating an environment where employees feel comfortable reporting security concerns is critical for early threat detection and mitigation.
Policies. Clear security policies and enforcement are essential for ensuring that employees understand their roles within the broader security framework, including responsibilities on strong password use, secure data handling, and prompt incident reporting. Implementing the principle of least privilege, which restricts access based on specific roles, mitigates potential harm from insider threats and inadvertent data exposure. Policies should evolve through routine security audits, including technical assessments and evaluations of employee protocol adherence, which will help organisations with a swifter identification of vulnerabilities and to take the necessary corrective actions.
However, despite the best efforts, breaches do happen – and this is where a well-defined incident response plan, that is regularly tested and updated, is crucial to minimise the damage. This requires every employee to know their roles and responsibilities during a security incident.
Tech Expansion Leading to Cyber Complexity
Cloud. Initially hesitant to transition essential workloads to the cloud, the BFSI industry has experienced a shift in perspective due to the rise of inventive SaaS-based Fintech tools and hybrid cloud solutions, that have created new impetus for change. This new distributed architecture requires a fresh look at cyber measures. Secure Access Service Edge (SASE) providers are integrating a range of cloud-delivered safeguards, such as FWaaS, CASB, and ZTNA with SD-WAN to ensure organisations can securely access the cloud without compromising on performance.
Data & AI. Data holds paramount importance in the BFSI industry for informed decision-making, personalised customer experiences, risk assessment, fraud prevention, and regulatory compliance. AI applications are being used to tailor products and services, optimise operational efficiency, and stay competitive in an evolving market. As part of their technology modernisation efforts, 47% of BFSI institutions are refining their data and AI strategies. They also acknowledge the challenges associated – and satisfying risk, regulatory, and compliance requirements is one of the biggest challenges facing BFSI organisations in the AI deployments.
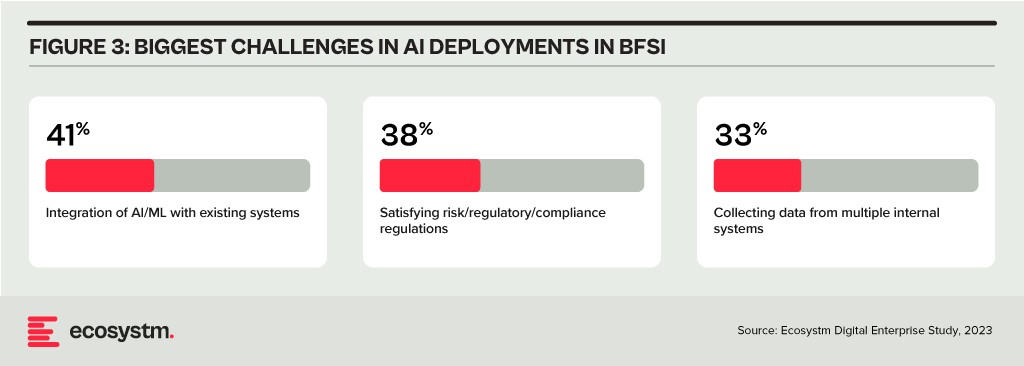
The rush to experiment with Generative AI and foundation models to assist customers and employees is only heightening these concerns. There is an urgent need for policies around the use of these emerging technologies. Initiatives such as the Monetary Authority of Singapore’s Veritas that aim to enable financial institutions to evaluate their AI and data analytics solutions against the principles of fairness, ethics, accountability, and transparency (FEAT) are expected to provide the much-needed guidance to the industry.
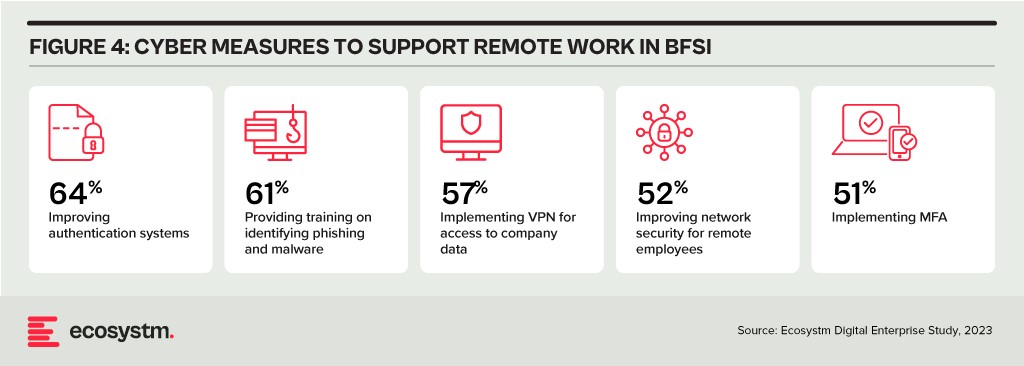
Digital Workplace. As with other industries with a high percentage of knowledge workers, BFSI organisations are grappling with granting remote access to staff. Cloud-based collaboration and Fintech tools, BYOD policies, and sensitive data traversing home networks are all creating new challenges for cyber teams. Modern approaches, such as zero trust network access, privilege management, and network segmentation are necessary to ensure workers can seamlessly but securely perform their roles remotely.
Looking Beyond Technology: Evaluating the Adequacy of Compliance-Centric Cyber Strategies
The BFSI industry stands among the most rigorously regulated industries, with scrutiny intensifying following every collapse or notable breach. Cyber and data protection teams shoulder the responsibility of understanding the implications of and adhering to emerging data protection regulations in areas such as GDPR, PCI-DSS, SOC 2, and PSD2. Automating compliance procedures emerges as a compelling solution to streamline processes, mitigate risks, and curtail expenses. Technologies such as robotic process automation (RPA), low-code development, and continuous compliance monitoring are gaining prominence.
The adoption of AI to enhance security is still emerging but will accelerate rapidly. Ecosystm research shows that within the next two years, nearly 70% of BFSI organisations will have invested in SecOps. AI can help Security Operations Centres (SOCs) prioritise alerts and respond to threats faster than could be performed manually. Additionally, the expanding variety of network endpoints, including customer devices, ATMs, and tools used by frontline employees, can embrace AI-enhanced protection without introducing additional onboarding friction.
However, there is a need for BFSI organisations to look beyond compliance checklists to a more holistic cyber approach that can prioritise cyber measures continually based on the risk to the organisations. And this is one of the biggest challenges that BFSI CISOs face. Ecosystm research finds that 72% of cyber and technology leaders in the industry feel that there is limited understanding of cyber risk and governance in their organisations.
In fact, BFSI organisations must look at the interconnectedness of an intelligence-led and risk-based strategy. Thorough risk assessments let organisations prioritise vulnerability mitigation effectively. This targeted approach optimises security initiatives by focusing on high-risk areas, reducing security debt. To adapt to evolving threats, intelligence should inform risk assessment. Intelligence-led strategies empower cybersecurity leaders with real-time threat insights for proactive measures, actively tackling emerging threats and vulnerabilities – and definitely moving beyond compliance-focused strategies.

Ransomware attacks have become a real threat to organisations world-wide – SonicWall reports that there were 304.7 million attacks globally in the first half of 2021, surpassing the full-year total for 2020. Organisations today are challenged with having the right cybersecurity measure in place, with cyber-attacks considered an inevitability.
This also challenges tech providers and cybersecurity vendors, as they have to constantly evolve their security offerings to protect their client organisations.
Ecosystm analysts, Alan Hesketh, Andrew Milroy and Claus Mortensen discuss the challenges tech providers face and how they are evolving their capabilities – organically, through acquisitions (Microsoft) and through partnerships (Google).























