The Wireless Broadband Alliance (WBA) was formed in 2003 to enable a seamless and interoperable Wi-Fi experience across the global wireless ecosystem. The key objective of the alliance was to bring together multiple stakeholders – such as telecom providers, technology vendors and enterprises – to work on areas such as industry guidelines, pilot projects, standards to promote end-to-end services and drive adoption in Wi-Fi, 5G, IoT and others.
WBA OpenRoaming™
Ecosystm Principal Advisor, Ashok Kumar says, “Wi-Fi has gained increasing popularity worldwide over the last two decades and has now become an essential network technology with ubiquitous service that it is utilitarian. However, it has been viewed as a collection of islands of heterogenous networks, requiring re-authentication each time a mobile user transits from one network and re-connects with another Wi-Fi network, with the associated hurdles of logging back in, making it cumbersome.”
“The lack of interoperability between Wi-Fi networks has been a drawback for service providers, compared to the ease of use associated with global mobile networks, such as 4G, LTE, 5G, and so on, which offer seamless roaming connectivity.”
The WBA OpenRoaming™ initiative was announced last month, to create a globally available Wi-Fi ecosystem that offers a federation of automatic and secure connections for billions of devices to millions of Wi-Fi networks. It provides a new global standards-led approach, removing public-guest Wi-Fi connectivity barriers and brings greater convenience and security to the wireless ecosystem. WBA OpenRoaming™ removes the need to search for Wi-Fi networks, to repeatedly enter or create login credentials, or to constantly reconnect or re-register to public Wi-Fi networks.
Several leading technology companies and telecom service providers have extended support to WBA OpenRoaming™ standards – Samsung, Google, Cisco, Intel, Aptilo, AT&T, Boingo Wireless, Broadcom, Comcast, Deutsche Telekom and Orange to name a few.
“Wi-Fi is arguably the most ground-breaking wireless technology of our time. From the first public Wi-Fi hotspots in the early 2000s which enabled radically increased productivity on the move, through to the role Wi-Fi has in today’s pandemic environment. With WBA OpenRoaming™ we want to revolutionise how individual users as well as businesses engage with Wi-Fi, removing the need to repeatedly log in, re-connect, share passwords or re-register for Wi-Fi networks as we travel locally, nationally or internationally”, said Tiago Rodrigues, CEO of the WBA, “Instead, no matter where we are, the new framework automates how users connect to Wi-Fi while seamlessly aligning to cellular network connectivity. It does so by bringing together a federation of trusted identity providers so that individual users are allowed to automatically join any network managed by a federation member.”
WBA OpenRoaming™ can simplify Wi-Fi, much like the cellular roaming experience. Kumar says, “ The WBA OpenRoaming™, with support from major global service providers, network solution vendors, and authentication & security firms, has the potential to address the issue of seamless interoperability in the Wi-Fi networks ecosystem with ease-of-use and security.”
WBA OpenRoaming™ Framework
The framework and standards are based on cloud federation, consisting of a global database of networks and identities, dynamic discovery and the Wireless Roaming Intermediary Exchange (WRIX); cybersecurity consisting of Public Key Infrastructure a RadSec providing the certificate policy, management and brokerage services; and network automation facilitated by an automated roaming consortium framework and policy and Wi-Fi CERTIFIED Passpoint®*.
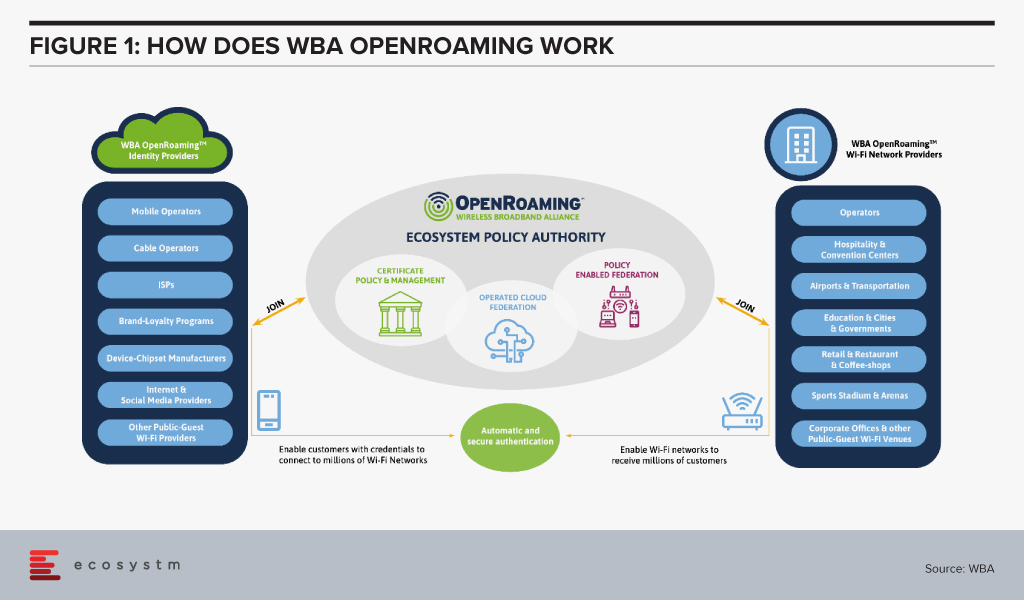
The Impact of WBA OpenRoaming™
“Enterprises are expected to benefit enormously from the opportunity to create new commercial business models and innovative services with speed and simplicity,” says Kumar.
Maturing mobile technologies such as 5G and Wi-Fi 6 along with next generation wireless devices, could make OpenRoaming™ more seamless and extend its applications further.
Cisco in particular has been leading the charge with several pilots that showcase the benefits of OpenRoaming™. Earlier this year, it partnered with Oxbotica, an autonomous vehicle software provider, to demonstrate how OpenRoaming™ can unlock the potential of autonomous vehicle fleets, allowing a seamless and secure sharing of high-volume data while on the move.
Last year, Cisco also showcased the benefits of OpenRoaming™ in a pilot at the Mobile World Congress in Barcelona with Samsung as the identity provider. Attendees were connected to the network throughout the venue, with connectivity extended to even local train stations and the airport. This unified experience was possible despite the fact that at least three network providers were involved. Pilots such as these gives the industry a glimpse of what benefits lie ahead.
Kumar sees the impact being extended across industries. “The impact of WBA OpenRoaming™ will be in the introduction of innovative services for consumers and enterprise users in public Wi-Fi networks in industries such as Hospitality, Transportation (airport and rail), Retail outlets, Smart City solutions, and local community networks.”
Learn more about WBA OpenRoaming™, visit www.openroaming.org
*Wi-Fi CERTIFIED Passpoint® is a registered trademark of the Wi-Fi Alliance
In his blog, The Cybercrime Pandemic, Ecosystm Principal Advisor, Andrew Milroy says, “Remote working has reached unprecedented levels as organisations try hard to keep going. This is massively expanding the attack surface for cybercriminals, weakening security and leading to a cybercrime pandemic. Hacking activity and phishing, inspired by the COVID-19 crisis, are growing rapidly.” Remote working has seen an increase in adoption of cloud applications and collaborative tools, and organisations and governments are having to re-think their risk management programs.
We are seeing the market respond to this need and May saw initiatives from governments and enterprises on strengthening risk management practices and standards. Tech vendors have also stepped up their game, strengthening their Cybersecurity offerings.
Market Consolidation through M&As Continues
The Cybersecurity market is extremely fragmented and is ripe for consolidation. The last couple of years has seen some consolidation of the market, especially through acquisitions by larger platform players (wishing to provide an end-to-end solution) and private equity firms (who have a better view of the Cybersecurity start-up ecosystem). Cybersecurity providers continue to acquire niche providers to strengthen their end-to-end offering and respond to market requirements.
As organisations cope with remote working, network security, threat identification and identity and access management are becoming important. CyberArk acquired Identity as a Service provider Idaptive to work on an AI-based identity solution. The acquisition expands its identity management offerings across hybrid and multi-cloud environments. Quick Heal invested in Singapore-based Ray, a start-up specialising in next-gen wireless and network technology. This would benefit Quick Heal in building a safe, secure, and seamless digital experience for users. This investment also shows Quick Heal’s strategy of investing in disruptive technologies to maintain its market presence and to develop a full-fledged integrated solution beneficial for its users.
Another interesting deal was Venafi acquiring Jetstack. Jetstack’s open-source Kubernetes certificate manager controller – cert-manager – with a thriving developer community of over 200 contributors, has been used by many global organisations as the go-to tool for using certificates in the Kubernetes space. The community has provided feedback through design discussion, user experience reports, code and documentation contributions as well as serving as a source for free community support. The partnership will see Venafi’s Machine Identity Protection having cloud-native capabilities. The deal came a day after VMware announced its intent to acquire Octarine to extend VMware’s Intrinsic Security Capabilities for Containers and Kubernetes and integrate Octarine’s technology to VMware’s Carbon Black, a security company which VMware bought last year.
Cybersecurity vendors are not the only ones that are acquiring niche Cybersecurity providers. In the wake of a rapid increase in user base and a surge in traffic, that exposed it to cyber-attacks (including the ‘zoombombing’ incidents), Zoom acquired secure messaging service Keybase, a secure messaging and file-sharing service to enhance their security and to build end-to-end encryption capability to strengthen their overall security posture.
Governments actively working on their Cyber Standards
Governments are forging ahead with digital transformation, providing better citizen services and better protection of citizen data. This has been especially important in the way they have had to manage the COVID-19 crisis – introducing restrictions fast, keeping citizens in the loop and often accessing citizens’ health and location data to contain the disaster. Various security guidelines and initiatives were announced by governments across the globe, to ensure that citizen data was being managed and used securely and to instil trust in citizens so that they would be willing to share their data.
Singapore, following its Smart Nation initiative, introduced a set of enhanced data security measures for public sector. There have been a few high-profile data breaches (especially in the public healthcare sector) in the last couple of years and the Government rolled out a common security framework for public agencies and their officials making them all accountable to a common code of practice. Measures include clarifying the roles and responsibilities of public officers involved in managing data security, and mandating that top public sector leadership be accountable for creating a strong organisational data security regime. The Government has also empowered citizens to raise a flag against unauthorised data disclosures through a simple incident report form available on Singapore’s Smart Nation Website.
Australia is also ramping up measures to protect the public sector and the country’s data against threats and breaches by issuing guidelines to Australia’s critical infrastructure providers from cyber-attacks. The Australian Cyber Security Centre (ACSC) especially aims key employees working in services such as power and water distribution networks, and transport and communications grids. In the US agencies such as the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Energy (DOE) have issued guidelines on safeguarding the country’s critical infrastructure. Similarly, UK’s National Cyber Security Centre (NCSC) issued cybersecurity best practices for Industrial Control Systems (ICS).
Cyber Awareness emerges as the need of the hour
While governments will continue to strengthen their Cybersecurity standards, the truth is Cybersecurity breaches often happen because of employee actions – sometimes deliberate, but often out of unawareness of the risks. As remote working becomes a norm for more organisations, there is a need for greater awareness amongst employees and Cybersecurity caution should become part of the organisational culture.
Comtech received a US$8.4 million in additional orders from the US Federal Government for a Joint Cyber Analysis Course. The company has been providing cyber-training to government agencies in the communications sector. Another public-private partnership to raise awareness on Cybersecurity announced in May was the MoU between Europol’s European Cybercrime Centre (EC3) and Capgemini Netherlands. With this MoU, Capgemini and Europol are collaborating on activities such as the development of cyber simulation exercises, capacity building, and prevention and awareness campaigns. They are also partnered on a No More Ransomware project by National High Tech Crime Unit of the Netherlands’ Police, Kaspersky and McAfee to help victims fight against ransomware threats.
The Industry continues to gear up for the Future
Technology providers, including Cybersecurity vendors, continue to evolve their offerings and several innovations were reported in May. Futuristic initiatives such as these show that technology vendors are aware of the acute need to build AI-based cyber solutions to stay ahead of cybercriminals.
Samsung introduced a new secure element (SE) Cybersecurity chip to protect mobile devices against security threats. The chip received an Evaluation Assurance Level (EAL) 6+ certification from CC EAL – a technology security evaluation agency which certifies IT products security on a scale of EAL0 to EAL7. Further applications of the chip could include securing e-passports, crypto hardware wallets and mobile devices based on standalone hardware-level security. Samsung also introduced a new smartphone in which Samsung is using a chipset from SK Telecom with quantum-crypto technology. This involves Quantum Random Number Generator (QRNG) to enhance the security of applications and services instead of using normal random number generators. The technology uses LED and CMOS sensor to capture quantum randomness and produce unpredictable strings and patterns which are difficult to hack. This is in line with what we are seeing in the findings of an Ecosystm business pulse study to gauge how organisations are prioritising their IT investments to adapt to the New Normal. 36% of organisations in the Asia Pacific region invested significantly in Mobile Security is a response to the COVID-19 crisis.
The same study reveals that nearly 40% of organisations in the region have also increased investments in Threat Analysis & Intelligence. At the Southern Methodist University in Texas, engineers at Darwin Deason Institute for Cybersecurity have created a software to detect and prevent ransomware threats before they can occur. Their detection method known as sensor-based ransomware detection can even spot new ransomware attacks and terminates the encryption process without relying on the signature of past infections. The university has filed a patent for this technique with the US Patent and Trademark Office.
Microsoft and Intel are working on a project called STAMINA (static malware-as-image network analysis). The project involves a new deep learning approach that converts malware into grayscale images to scan the text and structural patterns specific to malware. This works by converting a file’s binary form into a stream of raw pixel data (1D) which is later converted into a photo (2D) to feed into image analysis algorithms based on a pre-trained deep neural network to scan and classify images as clean or infected.

The opportunities that can be created by 5G continue to excite businesses and consumers alike. As 5G rollouts gather pace, new consumer experiences and business models emerge. For consumers, enhanced mobile broadband offers superior experience, driving the consumption of much more data-rich content and the more widespread application of emerging technologies such as augmented reality (AR). For businesses, the low latency, higher bandwidth, and the ability to handle massive machine type communications promised by 5G create opportunities for a dizzying array of uses cases, usually linked to IoT technology.
As enterprise use cases like autonomous driving, remote surgery and software-defined factories are enabled by 5G, the impact of cybersecurity breaches becomes much greater. Breaches can potentially have a catastrophic impact – they could lead to serious damage to or the destruction of sensitive critical infrastructures, such as power stations and transportation systems.
Security vulnerabilities associated with 5G are underpinned by a change in network architecture. The latency benefits of 5G require a more distributed architecture to enable use cases which require real-time data processing. This leads to the virtualisation of higher-level network functions formerly performed by physical appliances. So 5G networks will necessarily create a greatly expanded attack surface. If an attacker gains control of the software managing the networks, they can also control the network and potentially cause chaos.
One of the major benefits of 5G is massively increased bandwidth. This is also a huge benefit for attackers. An increase in available bandwidth makes it much easier to generate attack traffic from compromised connected devices and vulnerable networks. As volumetric DDoS attacks grow in terms of frequency, magnitude, and sophistication, traditional defences such as out-of-band scrubbing centres and manual interventions become inadequate and expensive.
In a 5G World, Security Postures must be Agile and not Act as a Bottleneck to Performance
5G use cases require a radical shift in cybersecurity posture and a new set of security considerations. Networks managed by enterprises and service providers need to scale up to handle larger capacity requirements and scale out to accommodate the increased demands of edge computing and the growing volumes of IoT endpoints. Security infrastructure must change accordingly with upgrades to both physical and virtual components. Importantly, security postures must also be sufficiently agile to change with new requirements while ensuring that security does not act as a bottleneck to network performance.
A common response to the increasing complexity of distributed cloud and IoT environments – where existing tools cannot always detect new and emerging threats – is to deploy brand new security tools. This seems like a great solution but can lead to significant problems and compromise security. Over time, the deployment of multiple security tools creates an estate of siloed security products, sometimes reporting to their own dashboards. Although this management challenge is typically being addressed by service providers and large enterprises, most commonly with SIEM, they must continually ensure that there is provision for the centralisation of security alerts, so that cybersecurity staff do not face the challenge of monitoring multiple consoles and cross-referencing between disparate screens and information formats. Applying security policy changes is a laborious and time-consuming task in a multi-dashboard environment – representing a security threat in its own right.
In the case of large volumetric attacks, redirecting suspicious traffic to scrubbing centres adds latency and imposes a significant financial burden, since mitigation costs are directly tied to the volume of the data traffic. Large enterprises and service providers should consider adopting new DDoS protection approaches that incorporate AI, real-time analysis, and telemetry to automate a more intelligent and cost-effective detection and mitigation process.
Different Policies Required to Reflect Specific Needs of Each Use Case
5G allows mobile service providers to partition their network resources, to address a diverse set of use cases with differing performance and functional requirements. These varying service performance profiles have a direct impact on security protocol choices and policy implementation. For instance, the service in one use case, such as a Smart City application, may require extremely long device battery life, which constrains the security protocol in some other way (e.g., how often re-authentication is performed). In another example, the use case may be very privacy-sensitive, requiring unusually intensive security procedures (e.g., very frequent reallocation of temporary identities).
The complexity associated with securing highly distributed and virtualised networks powered by 5G, will grow enormously and be hampered by an ever-increasing skills shortage. The only way to address these challenges is to create an intelligent security infrastructure that is sufficiently agile to scale with the network and use AI to detect, contain and eliminate threats. Security managers will need a unified view of all assets – physical and virtual – so that multiple security policies can be enforced and managed.
CEOs have an active role to play in an organisation’s transformation needs and journey – including in the technology decisions. Last month we spoke about why CEOs should get involved in their organisation’s IoT investments. Now, we look at Cloud – which has been a part of the CIO’s purview so far. Under the current circumstances, most organisations are actively pushing to go digital and the internal discussions will often revolve around empowering remote employees and digital customers. All the technologies that are being evaluated by organisations today have Cloud as their pillar. Increasingly, we see organisations adopt the hybrid and the multi-cloud. And organisations may not have the capabilities – technological and skills – to support the complexity of their Cloud environment. While a CEO does not have to understand the technology fully, it is important to understand the business impact of the technology.
Why should a CEO get involved in and have visibility into an organisation’s Cloud investments? There are a few important reasons.
#1 Cloud is not a cost-saving measure – it will enable you to transform
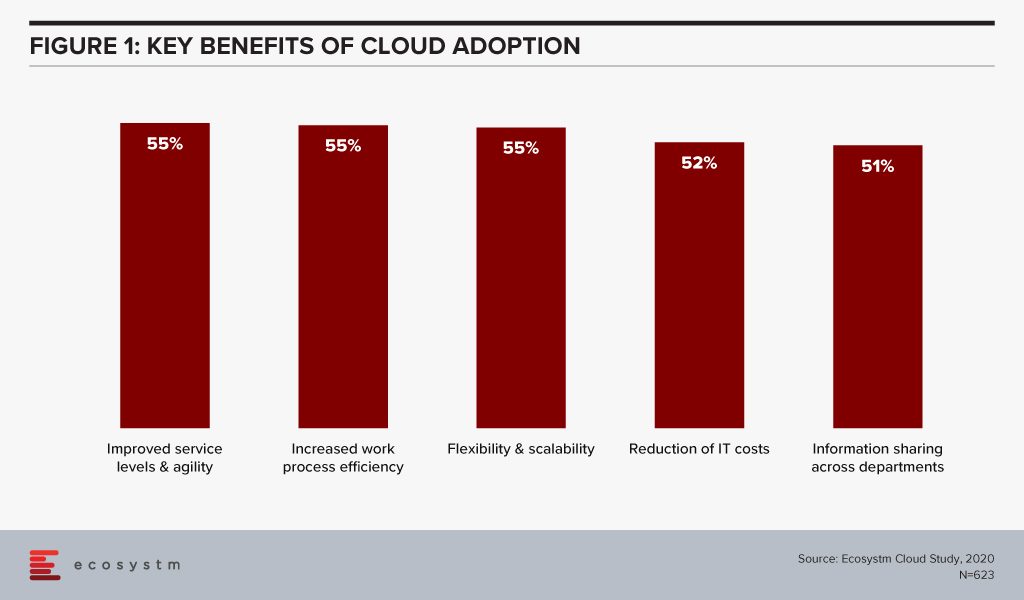
Organisations have matured in their Cloud adoption and no longer evaluate the benefits of Cloud only in terms of shifting CapEx to OpEx. If we look at the benefits of Cloud adoption, reduction of IT costs is not even in the top 3 benefits that organisations are seeking from Cloud anymore. Operational efficiency and collaboration emerge as key benefits (Figure 1) – while some companies still move to the Cloud for the savings, they stay there for other benefits.
This requires organisations to think of Cloud as a technology empowering their infrastructure and services. Cloud acts as an enabler for ease of doing business, real-time data access for productivity increase, and process automation. This impacts the entire organisation. It also involves prioritising the needs of certain functions over others – definitely not what a CIO should have to do.
If we look at just Cloud storage as an example, organisations can no longer have individual functions and their associated shadow IT teams having their own Cloud storage (and collaboration). This often turns out to be more expensive and there is a lack of consolidated view and management. While organisations forge ahead with the dream of having real-time information sharing across functions, a CIO has to consider the entire organisation’s technological and business needs – a CEO is the best person to guide the CIO in translating the organisation’s vision into IT priorities.
#2 In fact Cloud adoption may not cut costs at all!
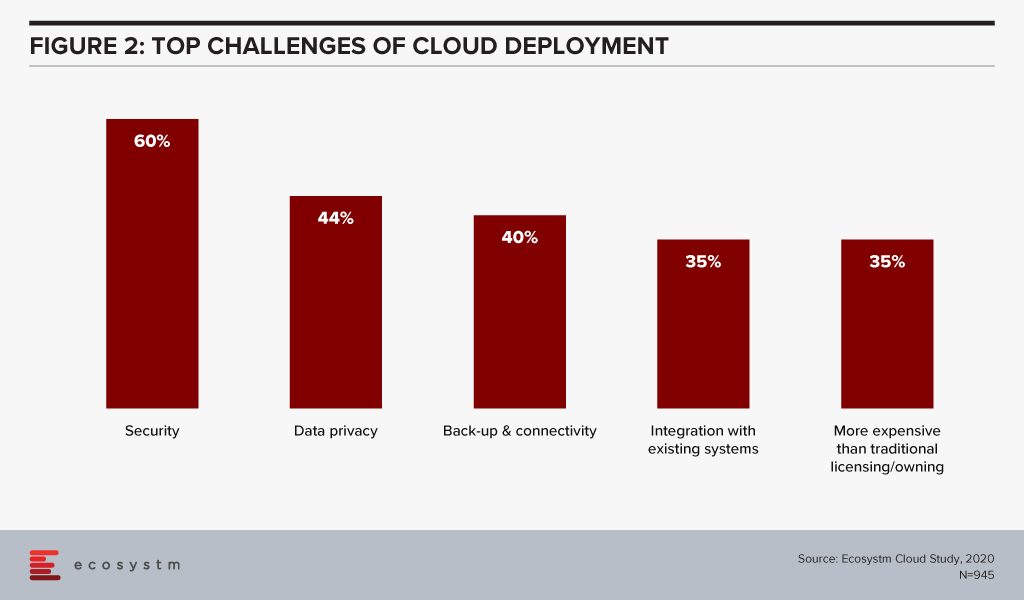
Organisations are also re-evaluating the cost benefits of Cloud. Investing in a Cloud infrastructure with a short-term view on the investments involved has led to instances of Cloud solutions being brought back in-house because of rising costs. While security, data privacy and integration remain the key challenges of Cloud adoption (Figure 2), over a third of the organisations find Cloud more expensive than traditional licensing or owning the hardware.
Organisations find that the cost considerations do not stop after the adoption or migration. As businesses use Cloud to scale, there are several aspects that require constant re-evaluation and often further investments – cybersecurity measures, continuous data protection (CDP), disaster recovery management, rightsizing capacity, software and database licenses and day-to-day maintenance, to name a few. In addition to this, the cost of finding and recruiting a team of professionals to manage and maintain the Cloud environment also adds up to the OpEx.
If the CIO is talking about a Cloud migration for cost benefits only, the CEO and the CFO need to step in to evaluate that all factors have been taken into consideration. Moreover, the CIO may not have full visibility of how and where the organisation is looking to scale up or down. It is the CEO’s responsibility to share that vision with the CIO to guide Cloud investments.
#3 Cloud will increasingly be part of all tech adoption considerations
In this disruptive world, CEOs should explore possibilities and understand the technical capabilities which can give organisations an edge over their competitors. It is then up to the CIOs to implement that vision with this larger context in mind. As organisations look to leverage emerging technologies, organisations will adopt Cloud to optimise their resources and workloads.
AI is changing the way organisations need to store, process and analyse the data to derive useful insights and decision-making practices. This is pushing the adoption of Cloud, even in the most conservative organisations. Cloud is no longer only required for infrastructure and back-up – but actually improving business processes, by enabling real-time data and systems access. Similarly, IoT devices will grow exponentially. Today, data is already going into the Cloud and data centres on a real-time basis from sensors and automated devices. However, as these devices become bi-directional, decisions will need to be made in real-time as well. Edge Computing will be essential in this intelligent and automated world. Cloud platform vendors are building on their edge solutions and tech buyers are increasingly getting interested in the Edge allowing better decision-making through machine learning and AI.
In view of the recent global crisis, we will see a sharp uptake of Cloud solutions across tech areas. IaaS will remain the key area of focus in the near future, especially Desktop-as-as-Service. Organisations will also look to evaluate more SaaS solutions, in order to empower a mobile and remote workforce. This will allow the workforce of the future to stay connected, informed and make more decisions. More than ever, CEOs have to drive business growth with innovative products and services – not understanding the capabilities and challenges of Cloud adoption and the advancements in the technology can be a serious handicap for CEOs.
#4 Your IT Team may be more complacent about Cloud security than you think
Another domain that requires the CEO’s attention is cybersecurity. The Cloud is used for computing operations and to store data including, intellectual property rights, financial information, employee details and other sensitive data. Cybersecurity breaches have immense financial and reputational implications and IT Teams cannot solely be responsible for it. Cybersecurity has become a Board-level conversation and many organisations are employing a Chief Information Security Officer (CISO) who reports directly into the CEO. Cybersecurity is an aspect of an organisation’s risk management program.
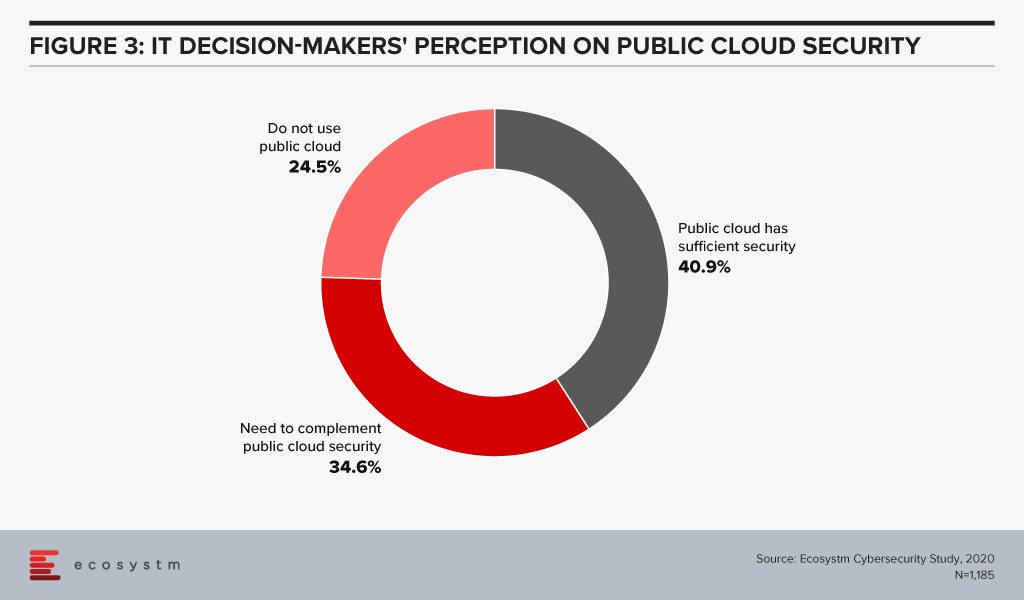
Evaluating the security features of the Cloud offerings, therefore, becomes an important aspect of an IT decision-maker’s job. While security remains a key concern when it comes to Cloud adoption, Cloud is often regarded as a more secure option than on-premise. Cloud providers have dedicated security focus, constantly upgrade their security capabilities in response to newer threats and evolve their partner ecosystem. There is also better traceability with the Cloud as every virtual activity can be tracked, monitored, and logged. Ecosystm research finds that more than 40% of IT decision-makers think the Public Cloud has enough security measures and does not need complementing (Figure 3).
However, the Cloud is as secure as an organisation makes it. The perception that there is no need to supplement Public Cloud security features can have disastrous outcomes. It is important to supplement the Cloud provider’s security with event-driven security measures within an organisation’s applications and cloud interface.
It is the job of the CEO – through the CISO – to evaluate how cyber ready the IT Team really is. Do they know enough about shared responsibility? Do they have full cognizance of the SLAs of their Cloud providers? Do they have sufficient internal cybersecurity skills? Do they understand that data breaches can have cost and reputational impacts? As cybersecurity breaches begin to have more financial implications than ever and can derail an organisation, a CEO should have visibility of the risks of the organisation’s Cloud adoption.
Cloud is no longer just a technological decision – it is a business decision and takes into account the organisation’s vision. A full visibility of the Cloud roadmap – including the pitfalls, the risks and the immense potential – will empower a CEO immensely.

Identifying and selecting a vendor for your tech project can be a daunting task – especially when it comes to emerging technologies or when implementing a tech solution for the first time. Organisations look for a certain degree of alignment with their tech vendors – in terms of products and pricing, sure, but also in terms of demonstrable areas of expertise and culture. Several factors are involved in the selection process – vendors’ ability to deliver, to match expected quality standards, to offer the best pricing, to follow the terms of the contract and so on. They are also evaluated based on favourable reviews from the tech buyer community.
Often businesses in a particular industry tend to have their unique challenges; for example, the Financial Services industries have their specific set of compliance laws which might need to be built into their CRM systems. Over the years, vendors have built on their industry expertise and have industry teams that can advise organisations on how their business requirements can be met through technology adoption. These experts speak in the language of the industry and understand their business and technology pain points. They are able to customise their product and service offerings to the needs of the industry for a single client – which can then be repeated for other businesses in that industry. Vendors arm themselves with a portfolio of industry use cases, especially when they are entering a new market – and this often gives them an upper hand at the evaluation stage. In the end, organisations want less customisations to keep the complexity and costs down.
Do organisations evaluate vendors on industry experience?
Ecosystm research finds that industry experience can be a significant vendor selection criterion for some tech areas (Figure 1), especially in emerging technologies such as AI. AI and automation applications and algorithms are considered to be distinctive to each industry. While a vendor may have the right certifications and a team of skilled professionals, there is no substitute for experience. With that in mind, a vendor with experience in building machine learning models for the Telecommunications industry might not be perceived as the right fit for a Utilities industry implementation.
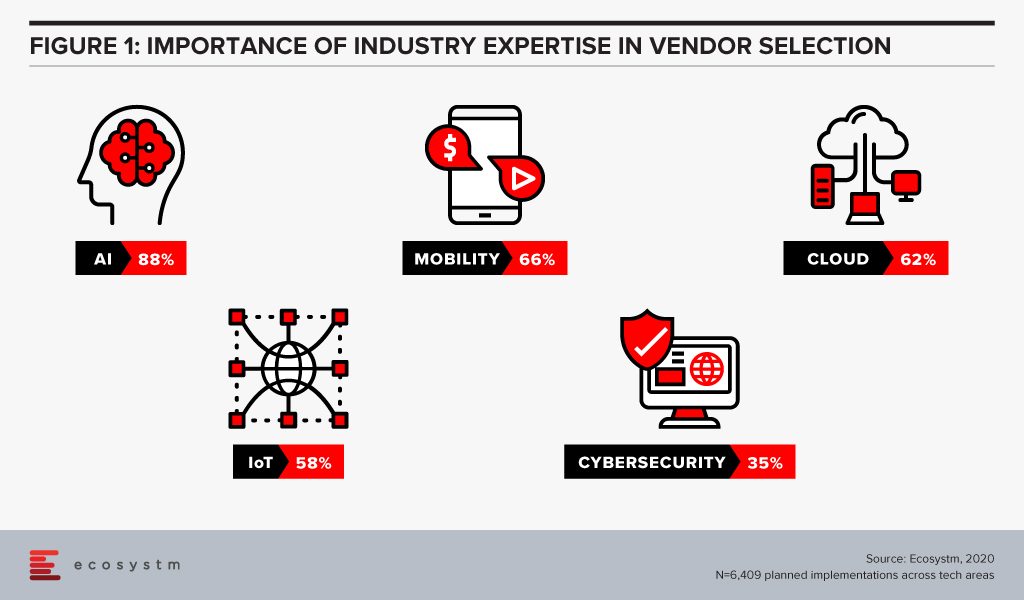
Whereas, we find that cybersecurity is at the other end of the spectrum, and organisations perceive that industry expertise is not required as network, applications and data protection requirements are not considered unique to any industry.
Is that necessarily the right approach?
Yes and no. If we look at the history of the ERP solution, as an example, we find that it was initially meant for and deeply entrenched in Manufacturing organisations. In fact, the precursor to modern-day ERP is the Manufacturing Resource Planning (MRP II) software of the 1980s. Now, we primarily look at ERP as a cross-industry solution. Every business has taken lessons on inventory and supply chain management from the Manufacturing industry and has an enterprise-wide system. However, there are industries such as Hospitality and Healthcare that have their niche vendors who bundle in ERP features with their industry-specific solutions. This will be the general pattern that all tech solutions will follow: a) an industry use case will become popular; b) other industries will try to incorporate that solution, and in the process; c) create their own industry-specific customisations. It is important, therefore, for those who are evaluating emerging technologies to cast their net wide to identify use cases from other industries.
AI and automation is one such tech area where organisations should look to leverage cross-industry expertise. They should ask their vendors about their implementations in other allied industries and, in some cases, in industries that are not allied.
For cybersecurity, their approach should be entirely different. As companies move on from network security to more specific areas such as data security and emerging areas such as GRC communication, it will be important to evaluate industry experience. Data protection and compliance laws are often specific to industries – for example, while customer-focused industries are mandated on how to handle customer data, the Banking, Insurance, Healthcare and Public Sector industries have the need to store more sensitive data than other industries. They should look at solutions that have in-built checks and balances in place, incorporating their GRC requirements.
So, the answer to whether organisations should look for industry expertise in their vendors is that they should for more mature tech areas. An eCommerce company should look for industry experience when choosing a web hosting partner, but should look for experience in other industries such as Banking, when they are looking to invest in virtual assistants.
Are some industries more focused on industry experience than others?
Ecosystm research also sought to find out which industries look for industry expertise more than others (Figure 2). Surprisingly, there are no clear differences across industries. The Services, Healthcare and Public Sector industries emphasise marginally more on industry expertise – but the differences are almost negligible.
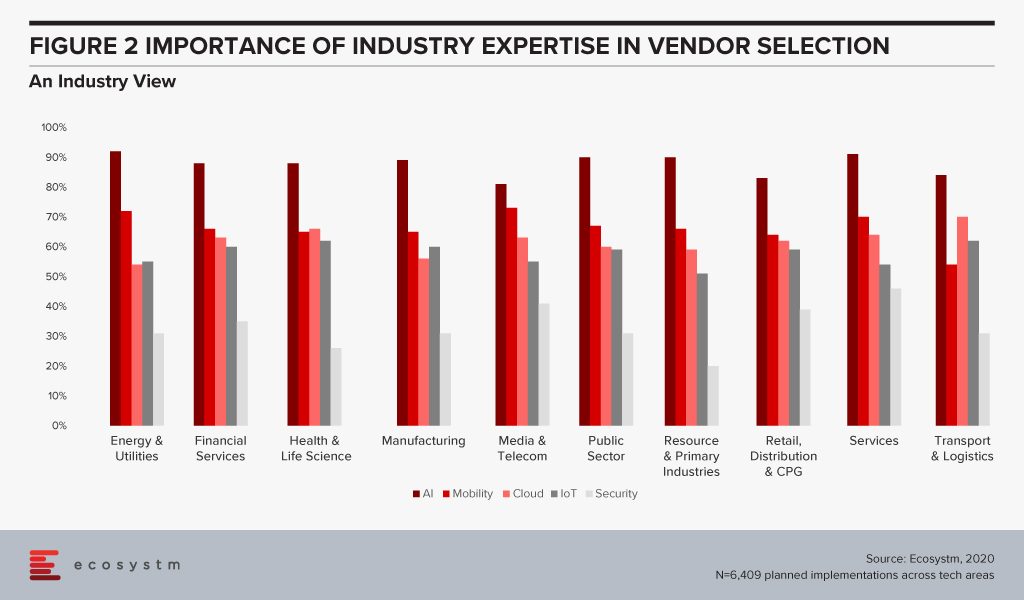
There are some differences when we look at specific tech areas, however. For example, industries that may be considered early adopters of IoT – Transportation, Manufacturing and Healthcare – tend to give more credit to industry experience because there are previous use cases that they can leverage. There are industries that are still formulating standards when it comes to IoT and they will be more open to evaluating vendors that have a successful solution for their requirement – irrespective of the industry.
The Healthcare Industry Example
Ecosystm Principal Analyst, Sash Mukherjee says, “In today’s fast-evolving technology market, it is important to go beyond use cases in only your industries and look for vendors that have a demonstrated history of innovation and experience in delivering measurable results, irrespective of the industry.” Mukherjee takes the example of the Healthcare industry. “No one vendor can provide the entire gamut of functionalities required for patient lifecycle management. In spite of recent trends of multi-capability vendors, hospitals need multiple vendors for the hospital information systems (HIS), ERP, HR systems, document management systems, auxiliary department systems and so on. For some areas such as electronic health records (EHR) systems, obviously industry expertise is paramount. However, if healthcare organisations continue to look for industry expertise and partner with the same vendors, they miss out on important learnings from other industries.”
Talking about industries that have influenced and will influence the Healthcare industry in the very near future, Mukherjee says, “Healthcare providers have learnt a lot from the Manufacturing industry – and several organisations have evaluated and implemented Lean Healthcare and Six Sigma to improve clinical outcomes. The industry has also learnt from the Retail and Hospitality industries on how to be customer focused. In the Top 5 Healthtech trends for 2020, I had pointed out the similarities between the Financial and Healthcare industries (stringent regulations, process-based legacy systems and so on). As the Healthcare industry focuses on value-based outcomes, governments introduce more regulations around accountability and transparency, and people expect the experience that they get out of their retail interactions, Healthtech start-ups will become as mainstream as Fintech start-ups.”
It is time for tech buyers to re-evaluate whether they are restricting themselves by looking at industry use cases, especially for emerging technologies. While less industry customisations mean easier deployments, it may also hamper innovation.
Telecom operators are fervently working towards 5G network and services deployment in order to be an early mover in the market. Operators are investing in Digital Transformation (DX) as well as inking partnerships with other players in the ecosystem to monetise on exciting new use cases in the enterprise segment and make market inroads.
The consumer market has become a retention play and on the whole many operators are experiencing declining margins and it appears unlikely that the consumer will pay more for higher speeds. Device affordability for mass-market remains a challenge though Chinese smartphone vendors are expected to release sub US$ 300 5G smartphones later this year. 5G can be expected to arrest the lengthening consumer upgrade cycle due to the attractions of not only faster speeds but improved streaming and cloud gaming. Data services revenues will continue to generate growth but this will be offset by losses in mobile voice services.
5G – An enterprise value proposition
Telecom operators have thus far been largely unsuccessful in penetrating the enterprise ICT market due to a variety of reasons including the slow pace of innovation, lack of a one-stop-shop offering, insufficient channel to market to especially small and medium enterprises (SMEs), and lack of skills in offering non-network services. 5G technology presents operators with another opportunity to address this long-standing challenge with the flexible features of enhanced mobile broadband (eMBB), Ultra-Reliable Low Latency Communications (URLLC) and massive machine type communication (mMTC) enabling tailored network and services offerings. 5G promises to revolutionise various industry solutions based on required data rates, low latency, reliability, and machine-type communications.
Monetising 5G is a key topic among leading executives and new business models are being devised. Connectivity services will be offered with a mix and match of throughput, bandwidth volumes and latency requirements. Fixed Wireless in Southeast Asia will be very popular considering the low penetration of fibre to the home and will provide enterprises with a viable secondary connection to the internet. Popular applications including video streaming and gaming which are speed, latency and volume hungry will also be a target market for operators.
More speed, latency and number of connections
5G offers theoretical speeds of 20 times that of 4G, low latency of 1 millisecond (ms), a million connections per kilometre and is expected to power a new era of mobile Internet of Everything (IoE). Offering high speed is the initial offering to the market and operators are going to be offering minimum guaranteed speeds for the first time. A high definition movie could be downloaded in 10 seconds while low latency means better performance for live sports, gaming, mission-critical automation and driverless cars – among others.
Fixed Wireless Access is the new wireless fibre
5G will offer fixed wireless access (FWA) or “wireless fibre” to households as an alternative to fixed broadband. It can be ideal as a redundant second link offering when the primary link is down. FWA broadband services offer a serious alternative to fixed broadband services which is plagued by the high cost of civil works for fibre optic deployment and expansion of the network to reach the rural population. FWA is expected to make strong inroads into households in Southeast Asia with the exception of Singapore, as many nations lag in fixed broadband penetration. As a comparison, ITU reports that fixed broadband penetration in countries such as South Korea (41.6%) and Hong Kong (36.8%) lead their Southeast Asian counterparts – Singapore (28.0%), Vietnam (13.6%), Thailand (13.2%) and Malaysia (8.6%).
A boon for Video and Gaming industry
Gaming is huge in Southeast Asia, notably in Thailand and Indonesia, and operators can take advantage of this offering with partnerships and value-added services with cloud gaming, high bandwidth and low latency packages. With cloud gaming, gamers can access a library of popular high-quality games minus the need for expensive hardware which has been the case in the past. This platform allows content creators and publishers to access the huge Southeast Asian market and monetise.
B2B2x is not a new concept where operators partner with leading providers of video streaming services through direct billing and 5G will be able to offer low latency, for example for live events. This brings in not just a commission per subscriber but additional revenue for the additional network features such as low latency.
Video streaming providers such as Netflix, Viu, Hooq and Iflix are worthy partners for a subscription – so are ad-based video-on-demand services. Live sports streaming service also makes for a very lucrative opportunity with 5G features of high data throughput and low latency.
Readiness through digital transformation
Efforts for preparedness for this business shift means significant operational and technology platform improvements, operating on the cloud, ease of incorporating the partner ecosystem and supporting a multitude of pricing models. DX should run parallel to the build of 5G public and private networks for a telecom provider to be in a leadership position and for them to be able to fully monetise 5G. Operators will be making major changes to OSS and BSS to support 5G use cases with the ultimate goal of ensuring customer-centricity.
Ecosystm research finds that nearly two-thirds of telecom providers are looking to increase their cybersecurity spending in the year. It is also clear that the biggest driver of that spend are their DX projects (Figure 1).
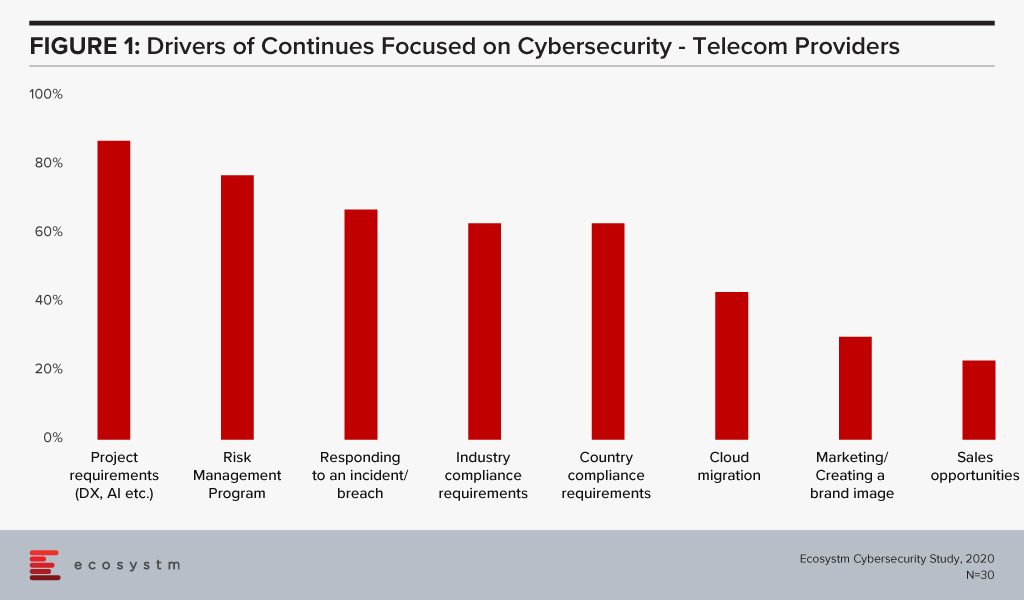
Cybersecurity is of paramount importance more than ever now with the increase in devices, software-based network services and edge computing. It is essential that a robust cybersecurity framework is in place as 5G will drive DX in enterprises, power the Digital Economy and provide the critical core infrastructure for Industry 4.0. Operators need to ramp up investment in cybersecurity technology, processes and people. A telecom operator’s compromised security can have country-wide, and even global consequences. As networks become more complex with numerous partnerships, there is a need for strategic planning and implementation of cybersecurity, with clear accountability defined for each party.
While Vodafone remains one of the leading global telecommunications providers, they face the need to transform their services and reach out to a wider audience. The customer base of a typical telecom provider is shifting, and they can no longer afford to just focus on consumers and need to include enterprises in their go-to-market strategy. Beyond the usual offerings of connectivity and mobile plans, Vodafone Business has solutions for Unified Communications, IoT and Cloud, to help grow their enterprise customer base. Ecosystm Principal Advisor, Tim Sheedy says, “Vodafone is one of the most successful telecom providers in the business space. Vodafone Business already represents around 30% of the Vodafone Group revenue, and unlike most in the telecommunications sector, they are showing growth (albeit moderate!).”
The Role of Telecom Providers in the Cybersecurity Market
An area where enterprises continue to need guidance and support is cybersecurity. The results of the UK Government’s Cyber Security Breaches Survey 2019 found that 32% of UK businesses had experienced a cyber-attack in the previous 12 months. More than a third of UK organisations have made changes in their cyber policies because of the GDPR – a majority focusing on policies first. It is not surprising therefore that Vodafone should identify cybersecurity as the next area of focus for their enterprise offerings.
Sheedy says, ”Cybersecurity services are one of the fastest-growing areas in technology. But because of this, it is a also a crowded market with everyone – from the big telecom providers, IT services providers, big audit firms, mid-sized technology providers down to the smaller cybersecurity experts – playing for this growing spend. It can, however, be argued that telecom providers have some of the deepest experience in cybersecurity and managing the risks – their networks are probably the most targeted by hackers and malicious actors. Telecom providers have massive teams just to stop threats from one or two countries. With all the work they do to protect their own network, they should have the skills to help protect the networks and assets of their clients.”
Ecosystm Principal Advisor, Alex Woerndle concurs, “Telecom providers are perfectly positioned to transition into managed security service providers (MSSPs). They already have the experience in providing a range of managed services, the ability to scale to support clients and some ready-made expertise internally in their in-house cybersecurity capabilities.”
Vodafone’s Foray into Cybersecurity
Vodafone Cyber Enhanced focuses on selected cybersecurity areas – threat analysis and intelligence, managed firewall and managed security services. The global Ecosystm Cybersecurity study finds that the solutions that organisations will invest in most in 2020 are Security Operations (SecOps) & Incident Response (by a third of global organisations) and Threat Analysis & Intelligence (by 20% of global organisations).
Commenting on the areas Vodafone is focusing on, Woerndle says, “Threat analysis and intelligence is where a lot of established SecOps providers and MSSPs are really focusing now. Previously it was simply a matter of monitoring alerts and reporting. Businesses and in-house security teams are now seeking more proactive assistance in searching for threats, before they become attacks. The challenge they face is catching up – effectively jumping from just being another SecOps centre (SOC) monitoring and reporting alerts, to matching the more mature SOCs with proactive threat intelligence to help clients mitigate before an attack is launched. This takes time, as it needs maturity of the SOC and the team, and also data, which established providers have accrued plenty of, over an extended period. While a managed firewall is not really a new service, it makes some sense to couple it with other managed security services to deliver a broader program. Vodafone is absolutely targeting the areas that businesses are looking into presently.”
Woerndle adds, “MSSPs will be crucial to the security sector moving forward. There has been a rapid growth of vendor solutions creating a very confusing market for tech buyers. This is coupled with a tight labour market for skilled people who can manage the tools. It is not surprising , therefore, that 86% of organisations across the world will look to engage with an MSSP when deploying a cybersecurity solution, according to Ecosystm research.”
Sheedy sees an opportunity for Vodafone to go global with their cybersecurity capabilities. “If Vodafone can compete with the bigger players (and perhaps partner with or complement the offerings of the smaller ones), then they should find a significant opportunity, especially within their larger clients – particularly as they move into the software-defined networking space. However, given the confusion around cybersecurity, they should expand their focus beyond larger enterprises to businesses over about 100 employees. As one of the largest global telecom providers, with one of the largest networks, they can be an important player in the cybersecurity space – growing the spend in their business clients. And while this is a UK play for now, one assumes that they will look to expand across their operating countries as Vodafone Cyber Enhanced gains traction.”
In our blog, Artificial Intelligence – Hype vs Reality, published last month we explored why the buzz around AI and machine learning have got senior management excited about future possibilities of what technology can do for their business. AI – starting with automation – is being evaluated by organisations across industries. Several functions within an organisation can leverage AI and the technology is set to become part of enterprise solutions in the next few years. AI is fast becoming the tool which empowers business leaders to transform their organisations. However, it also requires a rethink on data integration and analysis, and the use of the intelligence generated. For a successful AI implementation, an organisation will have to leverage other enabling technologies.
Technologies Enabling AI
IoT
Organisations have been evaluating IoT – especially for Industry 4.0 – for the better part of the last decade. Many organisations, however, have found IoT implementations daunting for various reasons – concerns around security, technology integration challenges, customisation to meet organisational and system requirements and so on. As the hype around what AI can do for the organisation increases, they are being forced to re-look at their IoT investments. AI algorithms derive intelligence from real-time data collected from sensors, remote inputs, connected things, and other sources. No surprise then that IoT Sensor Analytics is the AI solution that is seeing most uptake (Figure 1).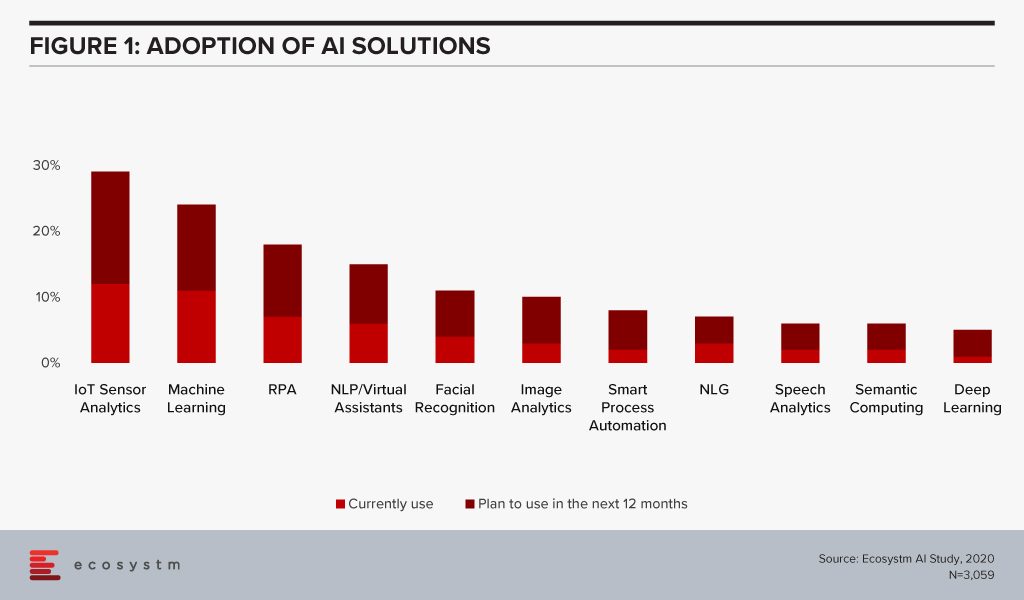
This is especially true for asset and logistics-driven industries such as Resource & Primary, Energy & Utilities, Manufacturing and Retail. Of the AI solutions, the biggest growth in 2020 will also come from IoT Analytics – with Healthcare and Transportation ramping up their IoT spend. And industries will also look at different ways they can leverage the IoT data for operational efficiency and improved customer experience (CX). For instance, in Transportation, AI can use IoT sensor data from a fleet to help improve time, cost and fuel efficiency – suggesting less congested routes with minimal stops through GPS systems, maintaining speeds with automated speed limiters – and also in predictive fleet maintenance.
IoT sensors are already creating – and will continue to create large amounts of data. As organisations look to AI-enabled IoT devices, there will be a shift from one-way transactions (i.e. collecting and analysing data) to bi-directional transactions (i.e. sensing and responding). Eventually, IoT as a separate technology will cease to exist and will become subsumed by AI.
Cloud
AI is changing the way organisations need to store, process and analyse the data to derive useful insights and decision-making practices. This is pushing the adoption of cloud, even in the most conservative organisations. Cloud is no longer only required for infrastructure and back-up – but actually improving business processes, by enabling real-time data and systems access.
Over the next decades, IoT devices will grow exponentially. Today, data is already going into the cloud and data centres on a real-time basis from sensors and automated devices. However, as these devices become bi-directional, decisions will need to be made in real-time as well. This has required cloud environments to evolve as the current cloud environments are unable to support this. Edge Computing will be essential in this intelligent and automated world. Tech vendors are building on their edge solutions and tech buyers are increasingly getting interested in the Edge allowing better decision-making through machine learning and AI. Not only will AI drive cloud adoption, but it will also drive cloud providers to evolve their offerings.
The global Ecosystm AI study finds that four of the top five vendors that organisations are using for their AI solutions (across data mining, computer vision, speech recognition and synthesis, and automation solutions) today, are also leading cloud platform providers (Figure 2).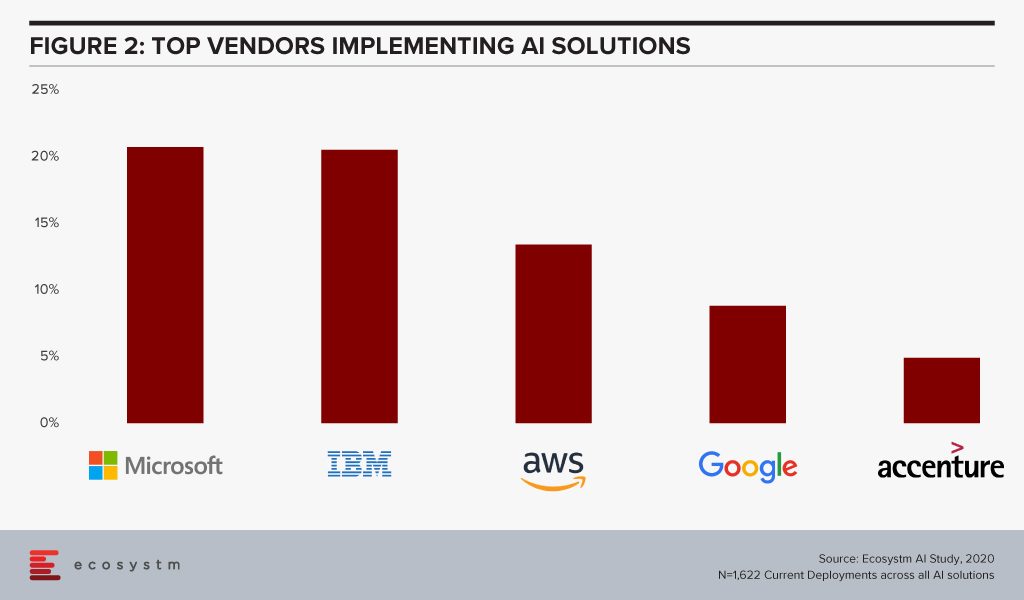
The fact that intelligent solutions are often composed of multiple AI algorithms gives the major cloud platforms an edge – if they reside on the same cloud environment, they are more likely to work seamlessly and without much integration or security issues. Cloud platform providers are also working hard on their AI capabilities.
Cybersecurity & AI
The technology area that is getting impacted by AI most is arguably Cybersecurity. Security Teams are both struggling with cybersecurity initiatives as a result of AI projects – and at the same time are being empowered by AI to provide more secure solutions for their organisations.
The global Ecosystm Cybersecurity study finds that one of the key drivers that is forcing Security Teams to keep an eye on their cybersecurity measures is the organisations’ needs to handle security requirements for their Digital Transformation (DX) projects involving AI and IoT deployments (Figure 3).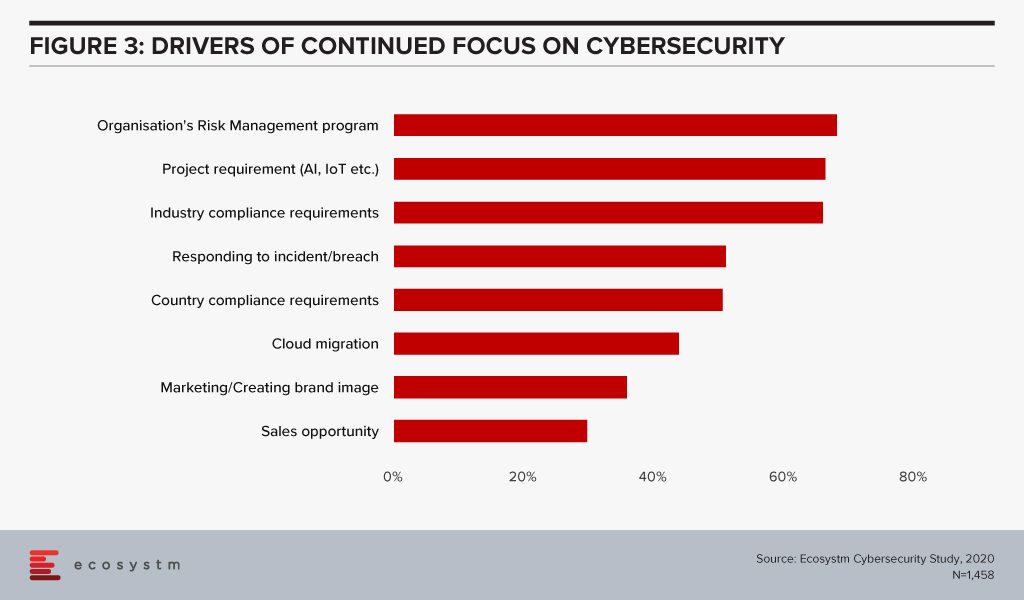
While AI deployments keep challenging Security Teams, AI is also helping cybersecurity professionals. Many businesses and industries are increasingly leveraging AI in their Security Operations (SecOps) solutions. AI analyses the inflow and outflow of data in a system and analyses threats based on the learnings. The trained AI systems and algorithms help businesses to curate and fight thousands of daily breaches, unsafe codes and enable proactive security and quick incident response. As organisations focus their attention on Data Security, SecOps & Incident Response and Threat Analysis & Intelligence, they will evaluate solutions with embedded AI.
AI and the Experience Economy
AI has an immense role to play in improving CX and employee experience (EX) by giving access to real-time data and bringing better decision-making capabilities.
Enterprise mobility was a key area of focus when smartphones were introduced to the modern workplace. Since then enterprise mobility has evolved as business-as-usual for IT Teams. However, with the introduction of AI, organisations are being forced to re-evaluate and revamp their enterprise mobility solutions. As an example, it has made mobile app testing easier for tech teams. Mobile automation will help automate testing of a mobile app – across operating systems (Figure 4). While more organisations tend to outsource their app development functions today, mobile automation reduces the testing time cycle, allowing faster app deployments – both for internal apps (increasing employee productivity and agility) and for consumer apps (improving CX).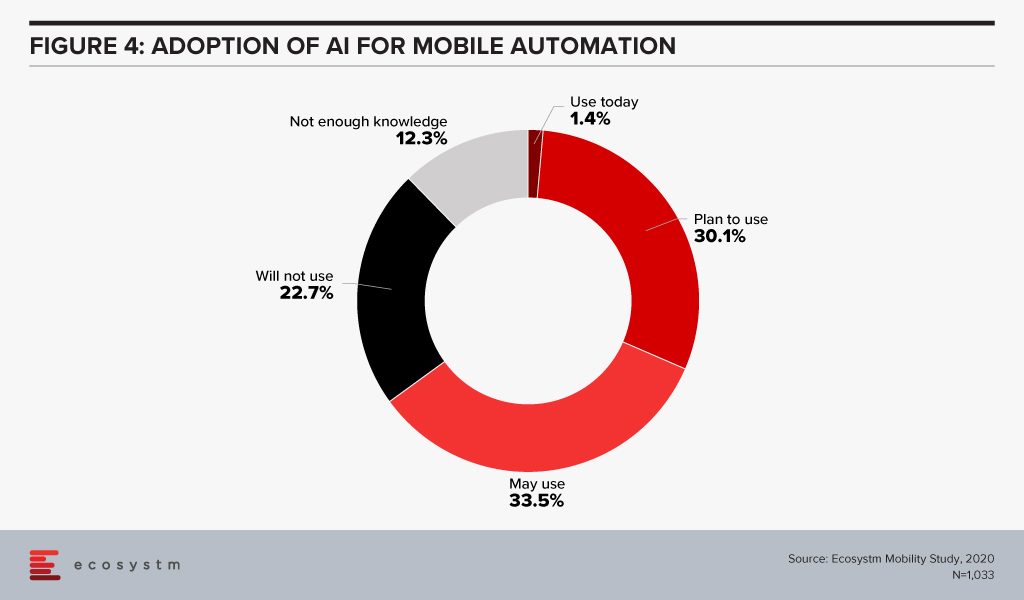
CX Teams within organisations are especially evaluating AI technologies. Visual and voice engagement technologies such as NLP, virtual assistants and chatbots enable efficient services, real-time delivery and better customer engagement. AI also allows organisations to offer personalised services to customers providing spot offers, self-service solutions and custom recommendations. Customer centres are re-evaluating their solutions to incorporate more AI-based solutions (Figure 5).
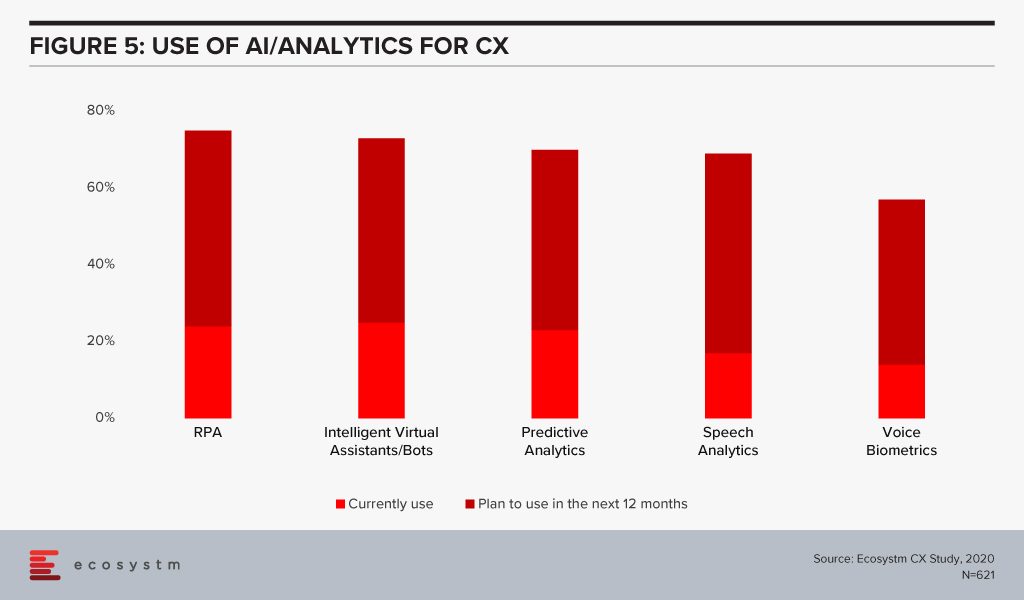
The buzz around AI is forcing tech teams to evaluate how AI can be leveraged in their enterprise solutions and at enabling technologies that will make AI adoption seamless. Has your organisation started re-evaluating other tech areas because of your AI requirements? Let us know in the comments below.

With the advancements in the technology landscape, the CIO’s role has become increasingly complex. One of the key challenges they face is in emerging and newer technology implementations, which require them to identify and partner with newer tech vendors. The common challenges that tech buyers face today include:
- The emergence of newer technologies that are catching the fancy of the C-suite and they are expected to adopt and deliver
- Getting management buy-in for IT investments (increasingly including discussions on ROI)
- Need to involve business stakeholders in tech decision-making
- Lack of sufficiently skilled internal IT
- Engagement with multiple tech vendors (including newer vendors that they have to establish a relationship with)
- Digital transformation projects that might require an overhaul (or at least a re-think) of IT systems
- Backdrop of compliance and risk management mandates
Many of these challenges will require the sourcing of new technology or a new tech partner and rethinking their vendor selection criteria. And selecting a tech vendor can be hard. The mere fact that there is an industry whose sole purpose is to help businesses select tech vendors goes to show the massive gap between what these providers sell and what businesses want. If there was easy alignment, the Tech Sourcing professionals and businesses would not have existed.
But over my time working with Tech Sourcing professionals, CIOs and business leaders, I have picked up on a few key factors that you should incorporate in your vendor selection process best practices. First and foremost, you are looking for a partner – someone who will be with you through the good and bad. Someone whose skills, products, services – and most importantly – culture, match your business and its needs.
I believe that the technology ecosystem is not really as competitive as we think. Yes, in practice Google competes with Microsoft in the office productivity space. But I often hear about companies moving from one to the other not for features, function or even price – but for a cultural match. Some traditional businesses were hoping Google can help them become more innovative, but in reality, their business culture smothered Google and meant they could not benefit from the difference in the ways of working. And I am not suggesting Microsoft is not innovative – more that Office represents the traditional ways of working – and perhaps can help a business take a more stepwise approach to change its own culture.
And I regularly hear about IT services deals (managed services, systems integration, consulting etc) going to the company that made the most sense from a cultural fit – where they were willing to take on the culture of their customer and embrace that way of working. In fact, I have been brought into many deals where a company hired a strategic consultant to create a new digital strategy or AI strategy, only to receive a document that is unworkable in their business and their culture.
So, I believe every strategic technology relationship should start and end with a cultural match. This company is a partner – not just a provider. How do you determine if they are a partner and measure cultural match? Well, that is the topic of an upcoming report of mine, so watch this space!
Questions You Should Ask Before Stepping in the Ring
There are also a number of questions that you should ask along with the partnership discussion:
- How will this solution change the organisation?
- What are the risks either way (of implementing or not implementing the solution)?
- Does the solution solve a key business problem?
- Is it likely to have more impact than the solution it is replacing?
- Where will the funding for the implementation come from?
- Have you calculated the ROI and the time to deployment?
- Have you baselined the current scenario so that you can measure improvement?
These can inform you of the business impact of the solution – and what you need to do to prepare for successful implementation (if you plan for success, you are more likely to be able to get faster benefits than if you do not plan for the change!)
Engagement Criteria for Your Shortlisting Process
In order to determine vendor selection process best practices, Ecosystm research tries to unearth the top criteria that organisations employ when shortlisting the vendors that they want to engage, across multiple technologies.
There is still a skills gap in internal IT and organisations want technical guidance from their Cloud and IoT vendors. With the plethora of options available in these tech areas, CIOs and IT teams also tend to look at the brand reputation when engaging with the vendor. Very often, organisations looking to migrate their on-prem solutions on the cloud engage with existing infrastructure providers or systems integrators for guidance, and existing relationships are significant. IoT solutions tend to be very industry-specific and a portfolio of specific industry use cases (actual deployments – not proofs of concept) can be impactful when selecting a vendor for planned deployments.
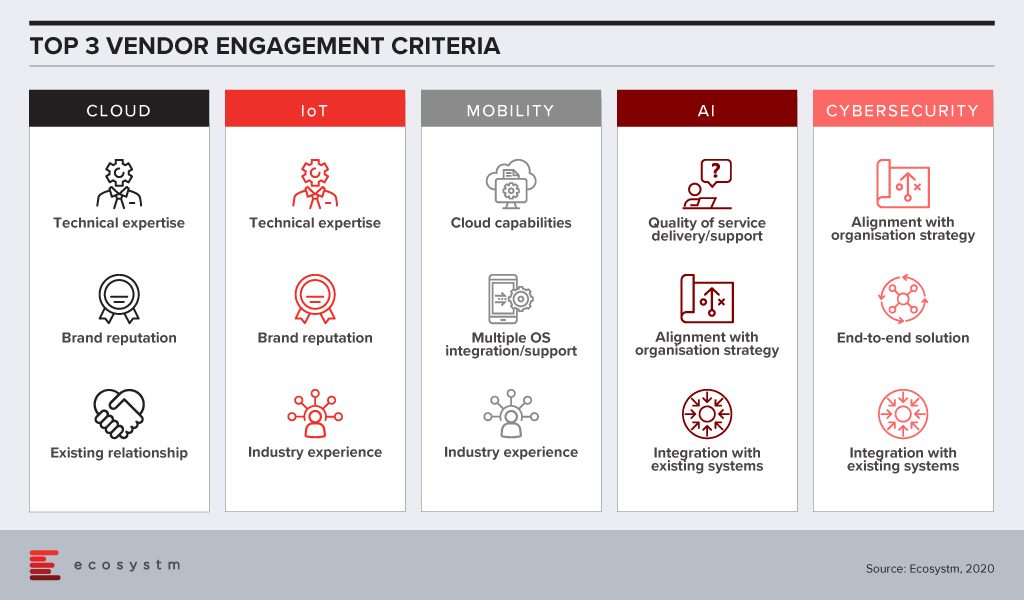
Artificial intelligence (AI) deployments are often linked with digital transformation (DX). Organisations look for a vendor that can understand the organisational strategy and customise the AI solutions to help the organisation achieve its goal. Adoption of AI is still at a nascent stage globally across all industries. Many organisations do not have the right skills, such as data scientists, yet. They appreciate that integration with internal systems will be key to reap the full benefits of the solutions, especially if the entire organisation has to benefit from the deployments. They also anticipate that they would have to have a continuous period of engagement with their vendors, right from identifying the right data set, data cleaning to the right algorithms that keep learning. Organisations will look at vendor partners who are known for delivering better customer experience.
This is true for cybersecurity solutions as well, as organisations are driven to continue their investments to adhere to the internal risk management requirements. Given how fragmented the cybersecurity landscape has become, organisations will also wish to engage with vendors that have an end-to-end offering, especially a managed security service provider (MSSP). Cybersecurity vendors are increasingly strengthening their partner ecosystem so that they can provide their client with the single-point-of-contact that they want.
Of the technologies mentioned in the figure, mobility is arguably the most mature. As organisations revisit their enterprise mobility solution as they go increasingly ‘Mobile First’, their requirements from their mobility vendors are more specific. They have decided over the years which OSs they want to support their enterprise applications and are looking for vendors with robust cloud offerings.
The vendor selection criteria will likely be different for each technology area. And as your knowledge and understanding of the technology increases, you should be able to drill the requirements down to the solution level, while making sure you engage with a vendor with the right culture.
Tim Sheedy’s upcoming report, ‘Best Practices for Vendor Evaluation and Selection’ is due to be published in February 2020.










