Cyber threats are growing in volume, intensity, and complexity and are here to stay. Basic endpoint attacks are becoming intricate, multi-stage operations. Cybercriminals are launching highly coordinated and advanced attacks. This evolving threat landscape affects businesses of all sizes, jeopardising data, operations, and finances.
In the face of massive data leaks, costly ransomware payments, and an ever-expanding and complex threat landscape, the need to strengthen digital defences has driven significant advancements in cybersecurity.
Read on to find out how organisations, governments, industry associations and technology providers are evolving ways to combat cybercrime.
Download ‘Securing the Future: Cyber Resiliency in the Digital World’ as a PDF

Ecosystm recently partnered with Asavie to conduct a study into the opportunity and outlook for the “Branch of One”. One of the challenges was actually defining what the Branch of One is. Here’s what we came up with:
Branch of One enables Office Anywhere by delivering secure, frictionless access to all business resources, with full mobility – meeting the security and manageability requirements of CIOs and CISOs.
Basically it is all the data and systems you need to get your job done, in your pocket. Secure. Easy to manage.
What I really like about the idea is that it describes what business is trying to achieve and it gives a common language and outcome for IT and business leaders. Consider all the things that IT and security teams need to do to enable access to applications and data in remote branches – from connectivity to security to data and system access. Often it takes days, weeks or months to open a new office or branch, or to provision a new retail store. Now, imagine having the ability to roll out all of these systems and services in seconds. To a single user or to thousands. Without consideration for location. Business leaders will understand this benefits and will support it.
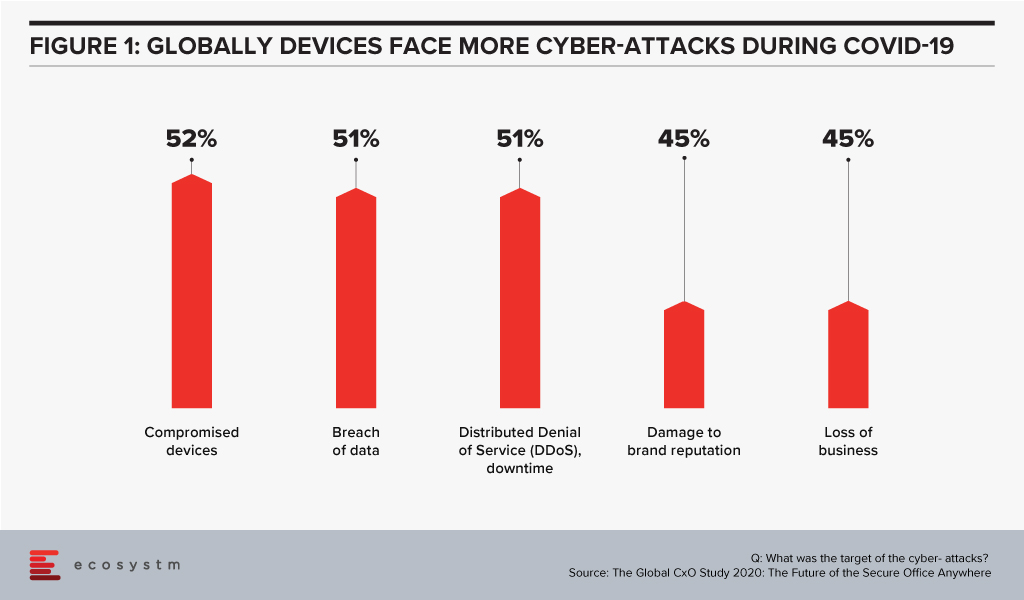
It also has the opportunity to help nearly every business today. Of the 1005 businesses we interviewed across the globe in our Global CxO Study 2020, 44% admitted to suffering cyber-attack incidents during COVID-19 due to employees working from home – and over half of these attacks were on mobile devices. Compromised devices were the number one target for cyber-attacks in 2020.
Businesses need a new way to manage the devices and applications of their remote employees. They need to be able to extend the benefits of the WAN to them without the downsides of VPNs. Every business we interviewed saw benefits of bringing devices, locations and offices inside the WAN. Turning every device and office into a Branch of One.
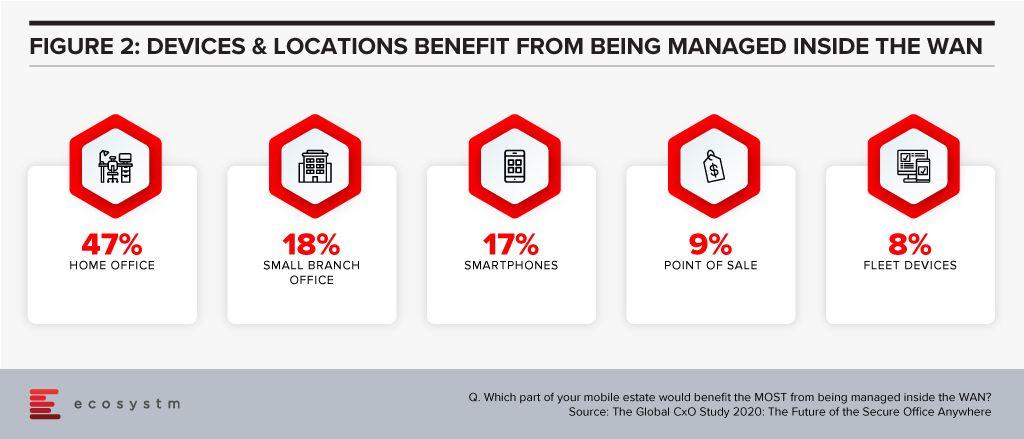
A few security and network technologies have promised this capability – SDNs can offer a similar service, but they require client software to be installed. 78% of businesses we interviewed are using VPNs to bring devices inside the WAN – but again, they require client software, and can be inconsistent (and insecure!) on mobile devices.
Companies that embrace the Branch of One can provision new users in a few clicks. No software to install, no cables to connect, no hardware to provision – it makes life easier for technology and security professionals. The Branch of One gives your employees the systems and data they need to get their job done – delivered securely across the mobile network.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

Last week, trading on the New Zealand Exchange (NZX) was disrupted on four consecutive days as a result of a sustained cyber-attack on to push market updates to the public as their website crashed and as a precautionary measure, NZX halted the trading sessions. Ecosystm Principal Advisor, Andrew Milroy says, “The recent NZX attack overwhelmed its public-facing NZX.com website and its Market Announcement Platform (MAP). This meant that investors could not see company announcements in real-time, preventing NZX from complying with regulatory requirements for continuous disclosure.”
The attacks which began on Tuesday came from overseas and made NZX struggle in recovering connectivity, over a five-day period. The cyber-attackers targeted NZX through distributed denial-of-service (DDoS) attacks which is a common way to overwhelm the network with sheer amount of traffic until it disrupts the services.
Milroy says, “It is not clear yet clear who launched the attack, but it is likely to be either an extortion attempt by a large cyber gang or a nation state attack. The attack was a very large, persistent, and sophisticated volumetric DDoS attack. A typical response to such an attack is to increase network bandwidth. However, additional bandwidth is becoming less effective at preventing DDoS attacks. DDoS attacks are getting larger and no amount of bandwidth can address the largest attacks, some of which exceed 1Tbps. DDoS attackers are increasingly focusing on the harder to protect application layer, rather than the network layers.”
The Government Communications Security Bureau (GCSB), network provider Spark, and international bodies provided assistance to NZX to mitigate the attack. Milroy adds, “NZX has also turned to Akamai for additional DDoS protection. Akamai’s Kona Site Defender is understood to be the solution being used. The product is designed to deflect network-layer DDoS traffic and absorb application-layer DDoS traffic at the edge. Mitigation capabilities aim to protect against attacks in the cloud.”
Growing Importance of Government Advisories and Investments
In November 2019, CERT NZ warned financial organisations of several global attacks including ransomware. The attacks were reportedly from Russia-based hacking groups. In an advisory, CERT NZ suggested businesses should implement DDoS protection services, and check network ports connected to avoid vulnerabilities and not pay any ransom to cybercriminals.
Following the CERT NZ warning last year, and considering the recent cyberattacks, GCSB has issued a security advisory to all businesses in New Zealand to be cautious on cyber incidents such as DDoS and ransomware attacks. The advisory comes from the GCSB’s National Cyber Security Centre. This is particularly aimed at small businesses that might have limited cybersecurity resources. The agency has asked them to report such incidents to Cert NZ. Advice includes:
- Approaching cybersecurity services providers to immediately implement any responsive actions (warning that organisations might incur additional fees)
- Temporarily transferring online services to a cloud-based hosting service
- Avoiding the disclosure of the IP address of the origin web server, and using a firewall, if using a content delivery network
- Using a DDOS mitigation service for the duration of attacks, in case they face attacks
- Disabling functionality or removing content from vulnerable online services
As a part of the New Zealand government’s cybersecurity strategy, last year the Government announced the allocation of USD 5.38 million to focus on security over the next four years, on top of USD 6.26 million funding for CERT NZ. The attack landscape and frequency has since increased in the aftermath of COVID-19.
Milroy says, “It will become increasingly important for governments the world over to make a concerted effort to protect their critical infrastructure, data assets and especially empower their SME communities with the right cybersecurity measures and timely guidance.”















