The next phase of a post-COVID world will be one of reduced physical contact, tighter regulations, and new habits and hygiene practices. This will translate into significant process changes which will be deeply enabled by mobile technology. All mobile form factors will be more integrated into how we interact. Interactional changes will be found in our homes, offices, public spaces and services.
In this blog post I address two fundamental questions as a technologist on the underpinnings of this shift:
- How can enterprises find ways of rebuilding and cementing trusted relationships using mobile technology?
- How does our infrastructural foundations support mobile technology for contactless transactions? (privacy, two-factor authentication, data quality and so on)
Situational shift to mobile
Given the rapid shifts in the last six months in how we can interact with each other, enterprises will have to be agile and flexible in process design going forward to optimize opportunities for customer engagements.
We will continue to have further disruptions on how we live and work in the next 12 to 18 months and potentially beyond. Some of the shifts towards mobile have been expected for a while, yet this crisis has pushed the timeline ahead as to how we engage.
Use cases in the “new normal”
Here are some use case examples in this next phase of business where mobile enables the transaction between consumer and environment:
Education. The reskilling and training certification that will be necessary to address unemployment, will be on Mobile First. Because of bandwidth, learner attention span, and form factor, there will be retooling of educational programs to be bite-sized and more media oriented.
Retail. Retail and delivery businesses shifting to remote first, with drop-off points that use mobile for contactless signatory and payment.
Healthcare. Telemedicine primarily by mobile devices (phone, laptop, phablet). Personal medical data sharing over mobile will require enhanced data encryption and two-factor authentication, which needs addressing via encryption and authentication.
Entrepreneurship. More side hustles that are mobile-based and mobile administered. Any authorization and transaction-oriented activities will be driven by mobile.
Government. Requests for document renewal or identity authentication for approval or submission of materials, with one-touch request.
Supply chain. Visibility and tracking of inbound and outbound materials. One-click reordering, and contactless payment verification.
Workplace. Contactless engagement with mobile as authentication of actions (coffee machine payment, copier usage, keyless office, meeting room allocation).
Facilities management. Hygiene controls with personnel health detail tracking (who cleans what room when). Deep cleaning management tools for audit trails, liability.
Role of mobile in creating engagement
Building trust
As we filter through the level of rubbish coming at us via social media, websites and our email, most of us are looking for a trusted information source. Our mobile is our window to the world, and many are applying appropriate filtration to make that world a bit more manageable.
The reason that people did previously download an app was partly based on what information had to be handed over in terms of permissions. The app builder needs to build a trusted relationship on benefit, not on what can be leveraged from the consumer.
To build that trust and create a closer engagement – albeit driven by situational need vs. consumer want – app developers need to consider these consumer needs:
- Level of trust in quality of information provided (e.g. weather info vs something more critical)
- Trust in app data usage and functionality (does it work?)
- Privacy of data being used and being held (statements and auditability)
- Location of data (on whose device: client or server)
- Speed and reaction time (Is there edge computing or the use of IoT to help push mobile information quickly?)
- Loss of data or loss of device and the impact on app access (More than lost passwords, lost processes and lost data)
Technological foundations for mobile usage
Network and bandwidth
We have all experienced bandwidth issues in the last few months, either sharing bandwidth with loved ones in lockdown to peak periods of video conferencing activity across geographic regions. Entertainment content providers such as Netflix and Disney+ were asked to lower the quality of the data streaming.
But then what online activity will take priority? Will we start to see pricing differentials for guarantees of availability? What about subscription models with platinum, gold and silver memberships (as in frequent flyer programmes) as to the network bandwidth you or your activity is allocated? Will things be done over VPN not only for privacy but for priority? I also see VPN as a possible solution towards issues like Zoom bombing and other intrusions to daily business operations.
We come to the role of a pandemic in 5G investment, which is similar to the role of investment in R&D during an economic downturn. Clearly, the world needs better bandwidth with more agility and future-proofed for functionality. You cannot drive a fast car on a bumpy road with potholes.
But for countries losing thousands of citizens to a virus with critical infrastructure at risk, where is the priority of a better telecom infrastructure? My colleague Shamir Amanullah wrote a report prior to the pandemic about the Race for 5G in Southeast Asia which is a good barometer for other regions. There is a good CNBC article from Todd Wassermann on the US situation, and a rather excellent survey on consumer sentiment on 5G from February 2020 by Politico.
Role of data quality and its security
Going back to my previous statement about rubbish and social media, the validation and quality of data exchange is part of the value proposition of using mobile technology.
What aspects of our current IT infrastructure create that ‘data value add’?
IoT and Edge Computing. Most of us are not going to be comfortable in crowds going forward. If I can reserve a space, or I can use a sensor to see how full an environment currently is, it will impact my decision to go somewhere. The faster that real-time information is processed and available, the better the outcome.
Blockchain technology is functioning enough to address the challenge of how to secure the data and prevent malicious cyber-attacks. This includes medical data hacking, supply chain theft, and other data-oriented safety issues on hygiene and product providence that we are experiencing now.
Final thoughts
At Ecosystm, we highlight how and where enterprises plan to invest and adopt technology while adding insights and expertise on to the use cases and trends. We are also able to reflect upon the agility of the same enterprises to make that technology investment count towards the next phase of their business model. In a post-COVID situation we see inventive ways enterprises are using technology. This is not only for societal benefit, but to make a difference in the marketplace. And mobile plays a key role in this next phase of engagements.
The nature of the workplace has changed over the years and so has the number of devices being used by today’s employees. More and more organisations are adopting a ‘Mobile First’ strategy – designing an online experience for Mobile users before designing it for the desktop/ Web. This is a paradigm shift from the past, where enterprises modified or adapted their websites, business processes and digital means of communications, to fit Mobile users.
Mobile First Drives the Adoption of UEM
Mobile First application designs take into consideration that Mobile users are constantly on the move. Information needs to be presented to them on smaller screens/displays with multi-media interfaces (voice/video), and multiple network connectivity options (Wi-Fi, cellular, and so on).
The global Ecosystm Mobility Study reveals that 73% of organisations have a Mobile First Strategy in place and are at various stages of implementation. About another 25% of organisations feel the need for a Mobile First vision and are formulating a strategy.
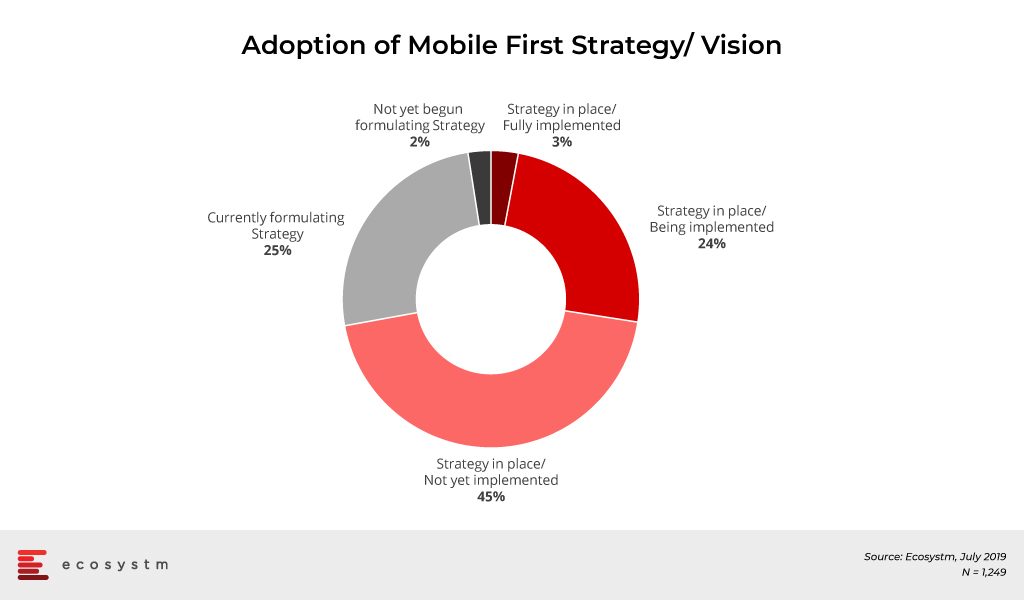
With Mobile First strategies, organisations are adding a wide range of devices and operating systems (OSs), regular innovative mobile-centric workload rollouts, new mobile apps across multiple functions, and IoT initiatives. As a result, organisations now have the need to support multiple devices and endpoints (including IoT sensors and wearables) multiple OSs, applications, and mobility policies such as BYOD. Organisations struggle to manage these devices, their data, apps and software updates across heterogeneous OSs and platforms. “The way companies are growing and fuelling their teams with devices now, shows the trend that these organisations will follow in the next few years, which will require a higher level of sophistication from the Unified Endpoint Management (UEM) solutions in the market,” says Amit Sharma, Principal Advisor, Ecosystm.
How does UEM Help?
An UEM solution can configure, monitor and manage multiple OSs, devices including IoT sensors, and gateways, and
- Unify application and configuration
- Manage profiles
- Monitor compliance
- Enforce Data Protection policies
- Provide a single view of multiple users
- Collate data for Analytics
It can ease the burden of management activity of internal IT teams and allow organisations to create a more streamlined lifecycle that secures mission-critical technology. It can also offer proactive threat monitoring, access control and identity, and patch management.
A good UEM solution provides IT managers with a transparent and traceable overview of all endpoints within the network as well as the power to manage all connected devices from a single platform. It maps out the network setup and structure by carrying out a complete inventory of all network devices, configurations, installed software, and the drivers for endpoint subsystems.
There are simply too many endpoints within Industrial IoT (IIoT) for IT managers to efficiently monitor manually. Mistakes will be made, and opportunities to stop breaches before they escalate will be missed. “An UEM solution not only shows the software and licensing situation but scans the IT environment for any irregularities or vulnerabilities and allows risk assessment and patch installation where it is necessary”, says Sharma. “Providing IT administrators with automated vulnerability management will enable them to filter and set search criteria by device, security vulnerability and threat level for the higher and most timely degree of protection.”
Industry Adoption of UEM
Customer-focused industries, with mobile workforces, are adopting UEM faster than other industries. The global Ecosystm Mobility study found the top industries that have implemented UEM or plan to in the near future. Most of the top industries cater to a high percentage of mobile workers. Their need to adopt UEM can come from different angles. According to the study, the Telecommunications industry leads in Mobile Content Management (MCM) adoption, and mobile apps for logistics and operations appear to be the key driver for the industry uptake of Mobile Applications Management (MAM).
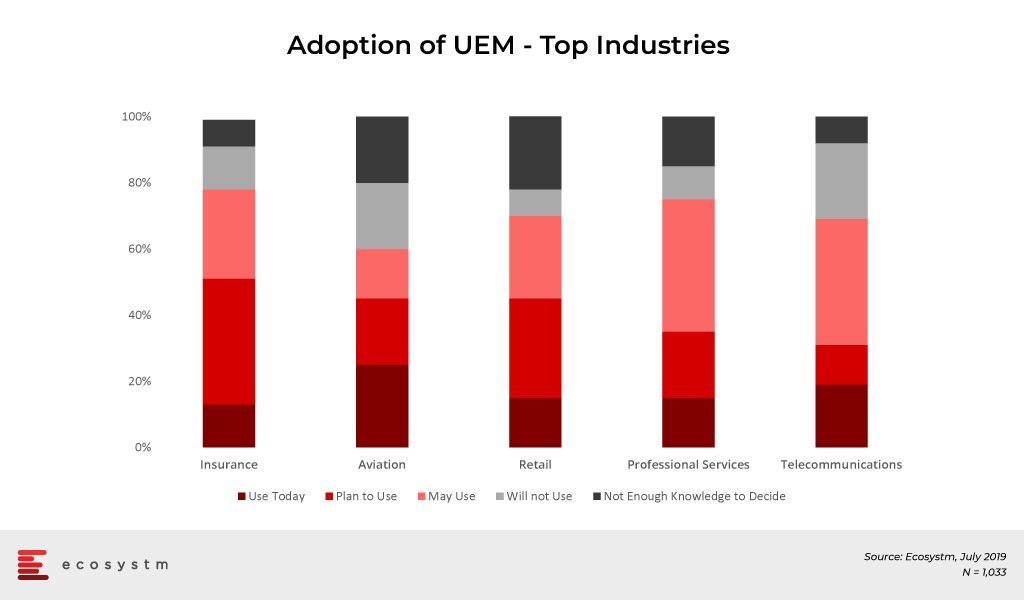
Other industries to look out for in the future are Banking and Healthcare, as they lead the pack when it comes to MDM adoption. Banks are incorporating technologies, such as mobile banking, and enabling payments via smartphones to provide enhanced services to customers. We have also seen the advent of Smart Point of Sale devices which are managed remotely on cloud infrastructure and these millions of devices will also be required to be managed by the banks that issued the devices.
The healthcare industry is another vertical where we can expect a higher uptake of UEM in the coming years. Clinicians and care providers are increasingly mobile, switching from device to device, depending on the task and location. Accessing mHealth applications and patient data from any device securely enables caregivers to focus on patients and outcomes. It also allows them to complete critical tasks from any device whether they are on call or off work. UEM makes HIPAA, SOC 2 and other healthcare regulation compliance easy for the providers.
Challenges of UEM Implementation
User experience must be at the centre of any mobility initiative. If the device, app management, or content is not something users want or are able to use, then it simply will not be adopted. The success of an UEM solution lies in the ability of users to quickly authenticate and gain seamless access to corporate apps and data from their devices. Users should also have access to self-service tools that help them manage basic device features and troubleshoot problems quickly.
“We can expect most Enterprise Mobility Management (EMM) and MDM suites to migrate to complete UEM suites that manage personal computers, mobile devices and Internet of Things (IoT) and Enterprise of Things (EoT) deployments,” forecasts Sharma. “Organisations should look for a purpose-built UEM solution which is platform-neutral and which cultivates a thriving ecosystem of complimentary mobile solution providers.”
However, there are several challenges that organisations face when they are developing and deploying an UEM solution. Sharma lists the top UEM implementation challenges that can be broadly classified into the following five categories.

“As AI finds its way into mobile devices and virtual personal assistants proliferate in offices and boardrooms, IT admins will have to manage more – and more sophisticated – endpoints. AI will continue its push into mobile hardware and enterprise communication devices, challenging IT shops’ EMM capabilities while at the same time offering potential security benefits.” Sharma adds. “Also, in 2019, voice-activated assistants such as Amazon Alexa and Cisco Spark Assistant will find their way into more corporate offices and conference rooms – becoming yet one more enterprise device encouraging the adoption of an UEM strategy.”
Have you adopted an UEM strategy in your organisation yet? Share your experience with us in the comments section.
Today Samsung announced their new “Samsung Galaxy Fold” device – and while it won’t be available until at least April 26. This foldable hybrid phone/tablet device is not the first foldable phone – but it will likely be the first one to have mass market availability and will be the first that businesses consider deploying.
But what is the business opportunity for the Samsung Galaxy Fold? It is not a slim, sexy phone, and it is not a large screen tablet like an iPad or Galaxy Tab S4 (although the screen is actually bigger than the smaller screen Tab A 7” tablet). It will be an expensive device (US$1,980) – but depending on the configuration will likely be cheaper than a high-end phone plus a high-end tablet. It doesn’t come with a stylus, but has the ability to help users multi-task (supporting up to three apps at the same time) and also supports DeX – Samsung’s under-rated ability to turn the phone into a PC-like experience. It also supports Samsung Knox, so the security capabilities that Samsung is becoming well known for will be supported by the Galaxy Fold.

Initially, it looks like a device that could replace the “phone and tablet” combination, but the reality is that many of the types of role that have both devices (engineers, repair people etc) typically require ruggedized devices – even a white goods repair person is working in wet and dirty environments and would at least have some type of case on their device. The unique nature of the Galaxy Fold likely prohibits a ruggedized case – and possibly any case at all (as the fingerprint sensor is on the side of the device).
A “Shareable” Device
One factor that strikes me about the Fold is the fact that large screens not only make content easier to consume – but also easier to share. Travelling salespeople – who typically do meetings in cafes or offsite meeting rooms often pull out their tablet or laptop to demonstrate a product or show a presentation or video. Laptops are not great for this – as the interface is designed for one user – not multiple, and many don’t have 4G connections.
You often see software salespeople pull out their tablet to demonstrate their SaaS platform – so this is one of the use cases for the Galaxy Fold – it is a pocketable tablet that has 4G (or 5G) connectivity. Any situation where a white collar executive is sharing information is a potential opportunity for the Galaxy Fold. Only time will tell whether such executives are willing to accept the compromises (thicker device, smaller front screen).
The Ultra-Portable Laptop
The Fold could be the device that shows the real benefit of Samsung DeX – the extra memory and processing power might convince some businesses or end-user computing teams to dump the laptop for some of their employees – and give them a device that can be a phone, tablet and PC. Carrying your laptop between work and home in your pocket might be an attractive option for some users.
An Executive Status Symbol
The Fold will make its way into the senior management ranks too. The device will draw attention and interest – so those who seek such attention will be drawn to it. But if you look around the senior executive community you see those who don’t mind having a larger device in their pocket normally do so because they have covered the phone in a massive “Otter Box” case – they are looking to protect their asset – again the lack of protection may be an inhibitor for this buyer. And the other execs who like a slim, sexy device may be put off by the size. It is hard to know exactly where the Galaxy Fold will land.
Whatever happens, it is great to see the rate of innovation in the smartphone market start to accelerate again after 3-4 years of stagnation. From an engineering and design perspective, the Fold looks incredible. What role it takes in the end-user computing strategy of businesses across the globe isn’t yet clear – but the idea of a device that helps your business users better share content could certainly be an opportunity.
If you’d like to discuss your End User Computing strategy feel free to reach out to me at: tim.sheedy@ecosystm360.com – or if you have any thoughts of other use cases for the Samsung Galaxy Fold please post them in the comments below – let’s keep the conversation going!




