Trust in the Banking, Financial Services, and Insurance (BFSI) industry is critical – and this amplifies the value of stolen data and fuels the motivation of malicious actors. Ransomware attacks continue to escalate, underscoring the need for fortified backup, encryption, and intrusion prevention systems. Similarly, phishing schemes have become increasingly sophisticated, placing a burden on BFSI cyber teams to educate employees, inform customers, deploy multifactor authentication, and implement fraud detection systems. While BFSI organisations work to fortify their defences, intruders continually find new avenues for profit – cyber protection is a high-stakes game of technological cat and mouse!
Some of these challenges inherent to the industry include the rise of cryptojacking – the unauthorised use of a BFSI company’s extensive computational resources for cryptocurrency mining.
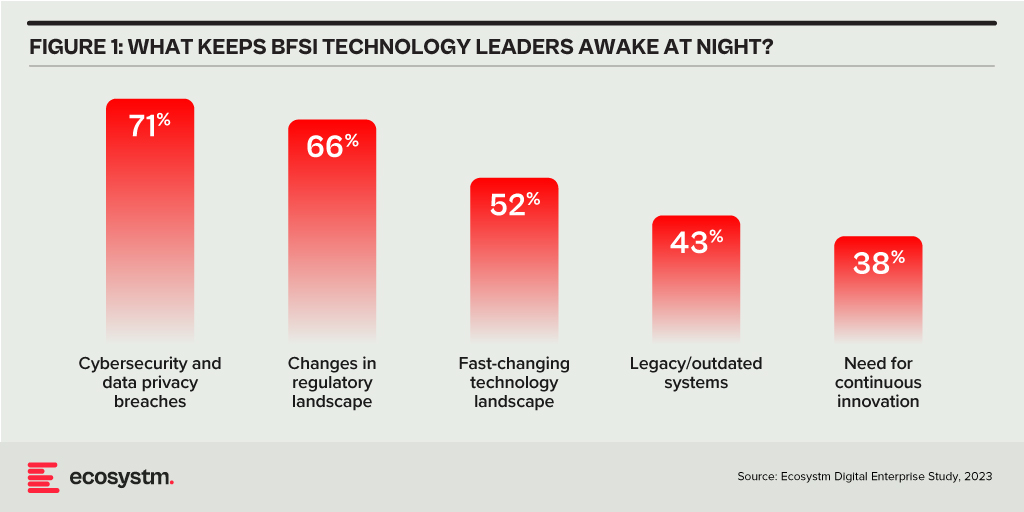
Building Trust Amidst Expanding Threat Landscape
BFSI organisations face increasing complexity in their IT landscapes. Amidst initiatives like robo-advisory, point-of-sale lending, and personalised engagements – often facilitated by cloud-based fintech providers – they encounter new intricacies. As guest access extends to bank branches and IoT devices proliferate in public settings, vulnerabilities can emerge unexpectedly. Threats may arise from diverse origins, including misconfigured ATMs, unattended security cameras, or even asset trackers. Ensuring security and maintaining customer trust requires BFSI organisations to deploy automated and intelligent security systems to respond to emerging new threats.
Ecosystm research finds that nearly 70% of BFSI organisations have the intention of adopting AI and automation for security operations, over the next two years. But the reality is that adoption is still fairly nascent. Their top cyber focus areas remain data security, risk and compliance management, and application security.
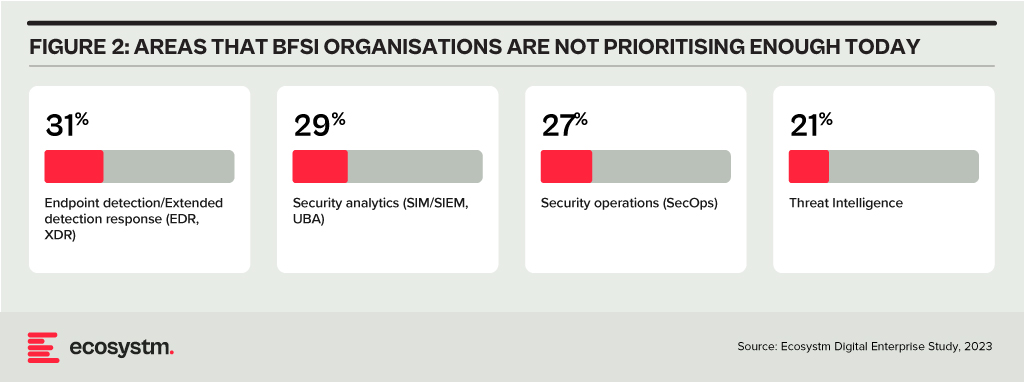
Addressing Alert Fatigue and Control Challenges
According to Ecosystm research, 50% of BFSI organisations use more than 50 security tools to secure their infrastructure – and these are only the known tools. Cyber leaders are not only challenged with finding, assessing, and deploying the right tools, they are also challenged with managing them. Management challenges include a lack of centralised control across assets and applications and handling a high volume of security events and false positives.
Software updates and patches within the IT environment are crucial for security operations to identify and address potential vulnerabilities. Management of the IT environment should be paired with greater automation – event correlation, patching, and access management can all be improved through reduced manual processes.
Security operations teams must contend with the thousands of alerts that they receive each day. As a result, security analysts suffer from alert fatigue and struggle to recognise critical issues and novel threats. There is an urgency to deploy solutions that can help to reduce noise. For many organisations, an AI-augmented security team could de-prioritise 90% of alerts and focus on genuine risks.
Taken a step further, tools like AIOps can not only prioritise alerts but also respond to them. Directing issues to the appropriate people, recommending actions that can be taken by operators directly in a collaboration tool, and rules-based workflows performed automatically are already possible. Additionally, by evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where security operations are completely automated.
Threat Intelligence and Visibility for a Proactive Cyber Approach
New forms of ransomware, phishing schemes, and unidentified vulnerabilities in cloud are emerging to exploit the growing attack surface of financial services organisations. Security operations teams in the BFSI sector spend most of their resources dealing with incoming alerts, leaving them with little time to proactively investigate new threats. It is evident that organisations require a partner that has the scale to maintain a data lake of threats identified by a broad range of customers even within the same industry. For greater predictive capabilities, threat intelligence should be based on research carried out on the dark web to improve situational awareness. These insights can help security operations teams to prepare for future attacks. Regular reporting to keep CIOs and CISOs informed of the changing threat landscape can also ease the mind of executives.
To ensure services can be delivered securely, BFSI organisations require additional visibility of traffic on their networks. The ability to not only inspect traffic as it passes through the firewall but to see activity within the network is critical in these increasingly complex environments. Network traffic anomaly detection uses machine learning to recognise typical traffic patterns and generates alerts for abnormal activity, such as privilege escalation or container escape. The growing acceptance of BYOD has also made device visibility more complex. By employing AI and adopting a zero-trust approach, devices can be profiled and granted appropriate access automatically. Network operators gain visibility of unknown devices and can easily enforce policies on a segmented network.
Intelligent Cyber Strategies
Here is what BFSI CISOs should prioritise to build a cyber resilient organisation.
Automation. The volume of incoming threats has grown beyond the capability of human operators to investigate manually. Increase the level of automation in your SOC to minimise the routine burden on the security operations team and allow them to focus on high-risk threats.
Cyberattack simulation exercises. Many security teams are too busy dealing with day-to-day operations to perform simulation exercises. However, they are a vital component of response planning. Organisation-wide exercises – that include security, IT operations, and communications teams – should be conducted regularly.
An AIOps topology map. Identify where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of threats, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
A trusted intelligence partner. Extend your security operations team by working with a partner that can provide threat intelligence unattainable to most individual organisations. Threat intelligence providers can pool insights gathered from a diversity of client engagements and dedicated researchers. By leveraging the experience of a partner, BFSI organisations can better plan for how they will respond to inevitable breaches.
Conclusion
An effective cybersecurity strategy demands a comprehensive approach that incorporates technology, education, and policies while nurturing a culture of security awareness throughout the organisation. CISOs face the daunting task of safeguarding their organisations against relentless cyber intrusion attempts by cybercriminals, who often leverage cutting-edge automated intrusion technologies.
To maintain an advantage over these threats, cybersecurity teams must have access to continuous threat intelligence; automation will be essential in addressing the shortage of security expertise and managing the overwhelming volume and frequency of security events. Collaborating with a specialised partner possessing both scale and experience is often the answer for organisations that want to augment their cybersecurity teams with intelligent, automated agents capable of swiftly

As organisations stride towards digitalisation, re-evaluating their business continuity plans and defining how the Future of Work will look for them, cloud adoption is expected to surge. Almost all technologies being evaluated by organisations today have cloud as their pillar. Cloud will the key enabler for ease of doing business, real-time data access for productivity increase, and process automation.
Ecosystm Advisors Claus Mortensen, Darian Bird and Tim Sheedy present the top 5 Ecosystm predictions for Cloud Trends in 2021. This is a summary of our cloud predictions – the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Cloud Trends for 2021
- 2021 Will be All About SaaS
2020 was a breakout year for SaaS providers – and a tough one for a lot of on-premises software vendors. SaaS (or mainly SaaS) providers like Salesforce, Zoom, Microsoft had record growth and some of the best quarters in their history, while other mainly on-premises software providers have had poor quarters. SAP is even accelerating the transition to a 100% cloud-based business as their revenue suffers. The race to deploy SaaS tools and platforms is well and truly happening. Many of the usual ROI models and business cases have been abandoned as the need for agility – to drive business change at pace trumps most other business needs. Ecosystm data validates this
This trend will continue in 2021 – in fact, we expect it to accelerate. Most SaaS solutions (such as CRM, ERP, SCM, HRM etc.) are implemented by less than 30% of businesses today – which means the upside for the SaaS providers is huge.
- Hybrid Cloud Will Finally Become Mainstream
The sudden move to remote working in 2020 forced most organisations to increase their use and reliance on cloud-based applications. Employees have relied on collaborative tools such as Zoom, Microsoft Teams and WebEx to conduct virtual meetings, call centre workers had to respond to calls from home – most if not all relying on cloud-based apps and platforms. This trend is set to continue going forward. Ecosystm research finds that 44% of organisations will spend more on cloud-based collaboration tools in the next 6-12 months.
But the forced adoption of these tools has also prompted many – especially larger organisations – to worry about losing control of their IT resources, including worries related to security and compliance, cost, and reliability. As for the latter, both Microsoft Azure and Zoom experienced outages after the pandemic hit and this has made many organisations wary of relying too much on a single public cloud platform. Ecosystm therefore expects a sharp increase in focus on hybrid cloud platforms in 2021 as IT Teams seek to regain control of the apps and services their employees rely the most upon.
- Carrier Investment in 5G Will Give Edge Computing a Boost
The gap between the hype around edge computing and the actual capabilities it offers will narrow in 2021 as 5G networks are built out. One of the most promising methods of deploying edge computing involves carriers embedding cloud capacity in their own data centres connected to their 5G networks. This ensures data does not unnecessarily leave the network, reducing latency and preserving bandwidth. This combination of 5G and the Edge will be of particular benefit to applications that until now have faced a trade-off between mobility and connectivity. Over the last twelve months, the major hyperscalers announced their 5G edge computing offerings, and some of the major global telecom providers have served as test cases by partnering with at least one hyperscaler and will likely add more over the next year. Expect this ecosystem to expand greatly in 2021.
Cloud environments can benefit from pushing computing-heavy workloads to the Edge in much the same way as IoT and provides a great platform for managing the edge computing endpoints. The flipside of pushing containers to the Edge will be the increased complexity and the fact that the number of attack surfaces will increase. Containerisation must therefore be deployed with security at its core.
- Stateful Applications Will Move to the Cloud with Containers and Orchestration
As organisations seek to migrate workloads and applications between platforms in an increasingly hybrid cloud environment, the need for “lifting and shifting”, refactoring and partitioning applications will increase. These approaches all have their shortcomings, however. Lifting and shifting an application may limit its functionality now or in the future; refactoring may take too long or be too costly; and partitioning is often not feasible or possible. A better approach to this task is to modernise the applications to make use of application containers like Docker, Windows Server Containers, Linux VServer and so on, to enable a faster and more seamless way to migrate applications between platforms. We also see container orchestration environments like Kubernetes and containerised development and deployment platforms like IBM’s Cloud Paks.
How these technologies are used to deploy stateful applications in multicloud environments will evolve. A raft of container management platforms, based on Kubernetes, are being released to simplify what was once a complex DIY process. New entrants will look to challenge the cloud hyperscalers, virtualisation giants, and Kubernetes specialists. The emerging features that previously required cobbling together third-party tools, like service mesh, data fabric, and machine learning, will speed up containerisation of stateful core applications. The deployment of containers on bare metal rather than in virtualised environments will also gather pace. The most challenging task will be delivering containerised applications at the Edge, forcing developers and platform providers to create inventive solutions.
- Serverless will take us a step closer to NoOps
As the application lifecycle speeds up and the distinction between development and operations shrinks, the motivation to adopt serverless computing will grow in 2021. While NoOps, the concept that operations could become so automated that it fades into the background, is still a distant goal, serverless computing will make a stride in that direction by abstracting the application from the infrastructure. Having seen the agility benefits of a microservices architecture, many DevOps teams will experiment with breaking services down further into functions. Moreover, the pay-as-you-go model of serverless will appeal to OpEx driven organisations. Expect stories of bill shock, however, as were seen in the early days of cloud adoption. While AWS Lambda is currently considered the serverless industry standard, it is likely that in 2021, Microsoft, Google, and IBM will ramp up efforts in this space. Each of these providers will build out their offering in terms of languages supported, event triggers, consumption plans, machine learning/AI options, observability, and user experience.




