Last week, the Australia government joined other countries in the Asia Pacific region in highlighting the growth of attack surface in the midst of the COVID-19 pandemic.
In our recently launched study Digital Priorities in the New Normal, we find that 87% of organisations in the Asia Pacific have increased investments in one or more cybersecurity solutions. However, this has to be backed by a reassessment of organisations’ risk positions and a re-evaluation of data protection and compliance policies.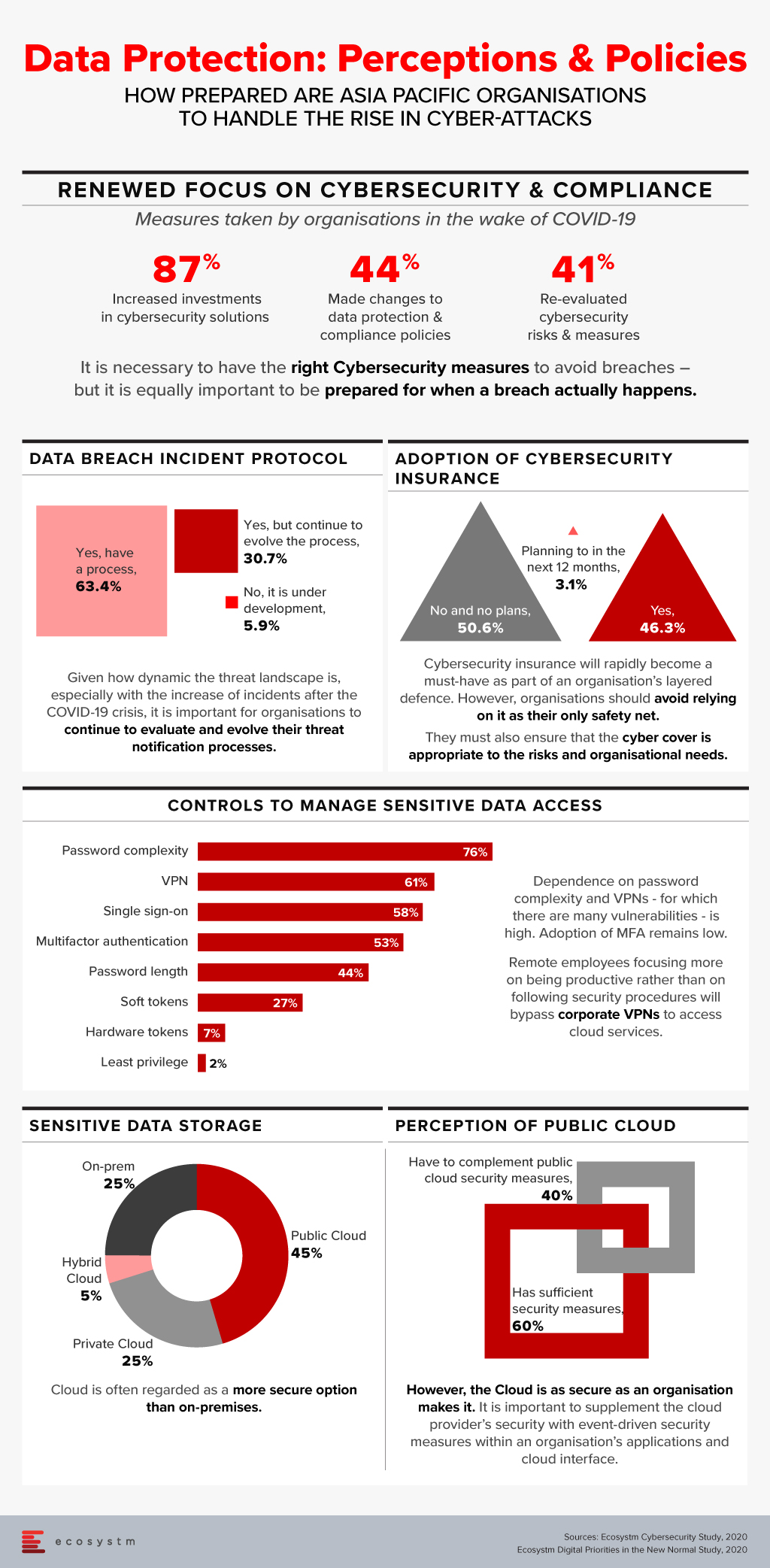

One of the questions that organisations are asked in the global Ecosystm Cybersecurity Study, is how they rate their cybersecurity measures and controls (on a scale of 1-10, where 10 is extremely mature). Organisations that rate themselves at an 8-10, are considered ‘mature’ in their cybersecurity measures while those that rate themselves at 1-7 are evolving their cybersecurity practices. Clear differences in priorities and investments can be seen between the mature and evolving adopters of cybersecurity measures.
Here are the key differences that emerge and should allow organisations to benchmark their cybersecurity practices against those of the mature adopters of cybersecurity solutions.
#1 Do you have the Right Motives?
There is no denying that organisations have to continue to evolve their cybersecurity measures with the evolving threat landscape. There is a need to have a continued focus on cybersecurity. However, are they doing it to address the right issues and threats? Mature organisations have their cybersecurity measures entrenched within the organisation’s risk management programs which help them align their investments to their risk position (Figure 1). Very often these programs have their technology landscape – special projects for digital transformation (DX) – and industry compliance laws built into them. Mature organisations also have a proactive approach to incidents and breaches, continuing to evolve their cybersecurity practices.
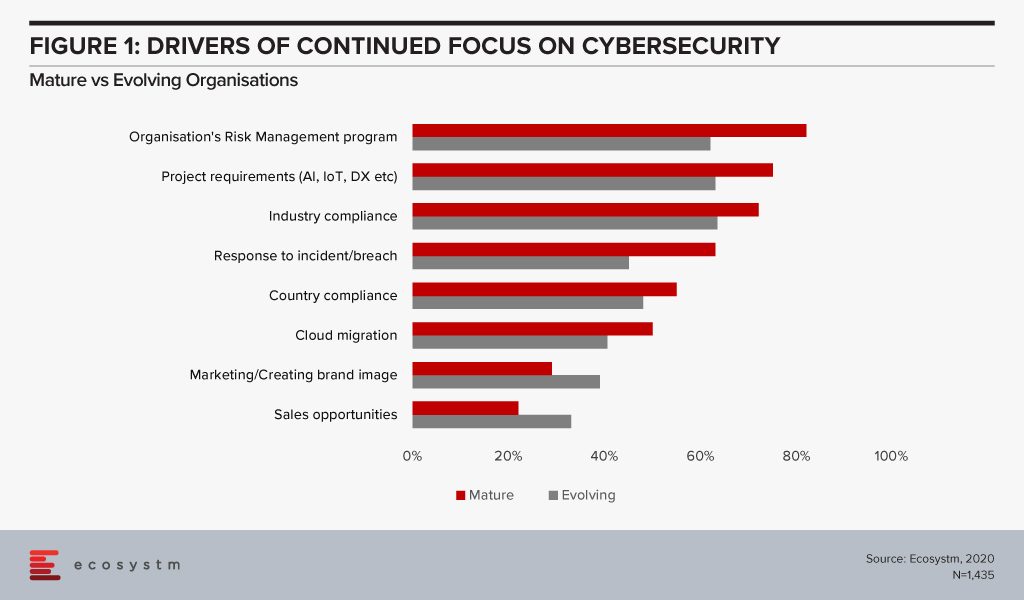
While cybersecurity practices can help with an organisation’s go-to-market messaging, the reasons for investing in robust cybersecurity practices should be more aligned to the organisation’s risk strategies. Also, it should not be restricted to compliance alone and should be much more proactive than merely ticking the right boxes.
#2 Are you focusing on the Right Challenges?
As solution complexity increases, organisations are challenged by their cybersecurity deployments (Figure 2). Cybersecurity measures must be applied across the entire organisation and systems, including applications, database, and storage whether on-prem or on cloud (public, private or hybrid). This adds to the complexity of the solutions and the associated integration challenges.
While it is not possible to have an unlimited budget for cybersecurity measures, once it is treated like a business issue, and the risks associated (including financial and reputational) are conveyed to the key stakeholders cybersecurity budgets become part of the organisational strategy consideration. If your security team is still struggling to procure what they think is the right budget, there is a mismatch in expectations and miscommunication between the security team and executive management. “A risk focussed approach enables organisations to understand the ROI on security measures and therefore invest in the most impactful areas of cyber risk for their business”, says Alex Woerndle, Principal Advisor Ecosystm.
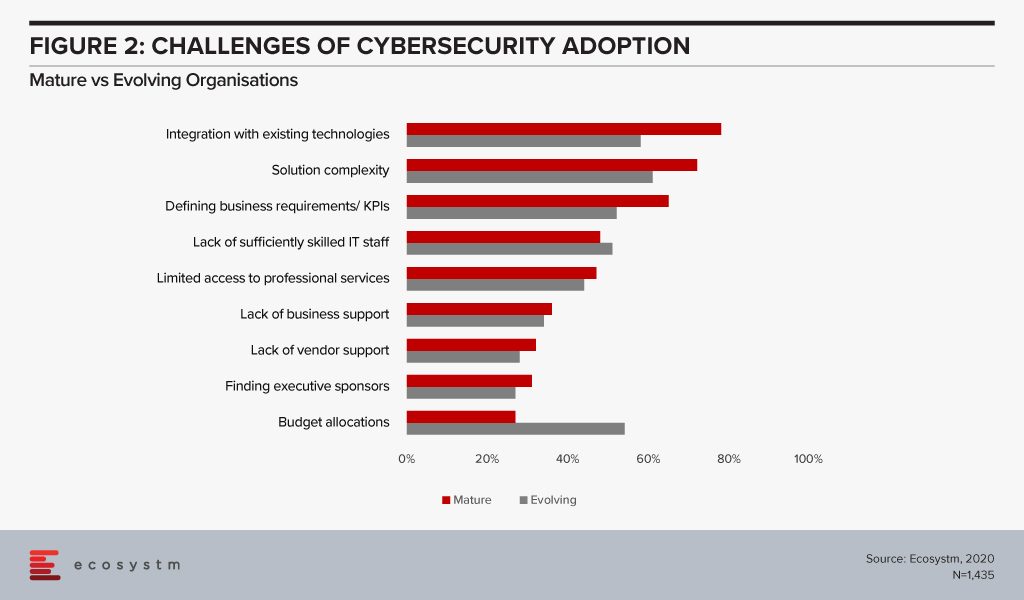
A real challenge that all organisations face is skills shortage. However, it is time to align business and security strategies and look beyond IT for security analysts – professionals who can translate what the Board’s priorities are into defining the security strategy.
#3 Do you have a dedicated Cybersecurity Role?
While the Board will often be involved in evaluating the risk exposure of an organisation, there is need for a dedicated role that can traverse both the business and the technological needs in deciding the right cybersecurity framework.
Organisations should have a dedicated responsibility for their cybersecurity practice – the CISO/CSO is the key data protection lead in mature organisations (Figure 3). CISOs should be reporting into the CFO, Chief Risk Officer or the CEO and not the CIO to avoid a conflict of interest. Alex says, “While the most common reporting line for CISOs is still to the CIO, there is a fundamental conflict of interest with this model – being part of the risk function, or reporting directly to the CEO, provides the level of independence required for good governance of cyber risk.”
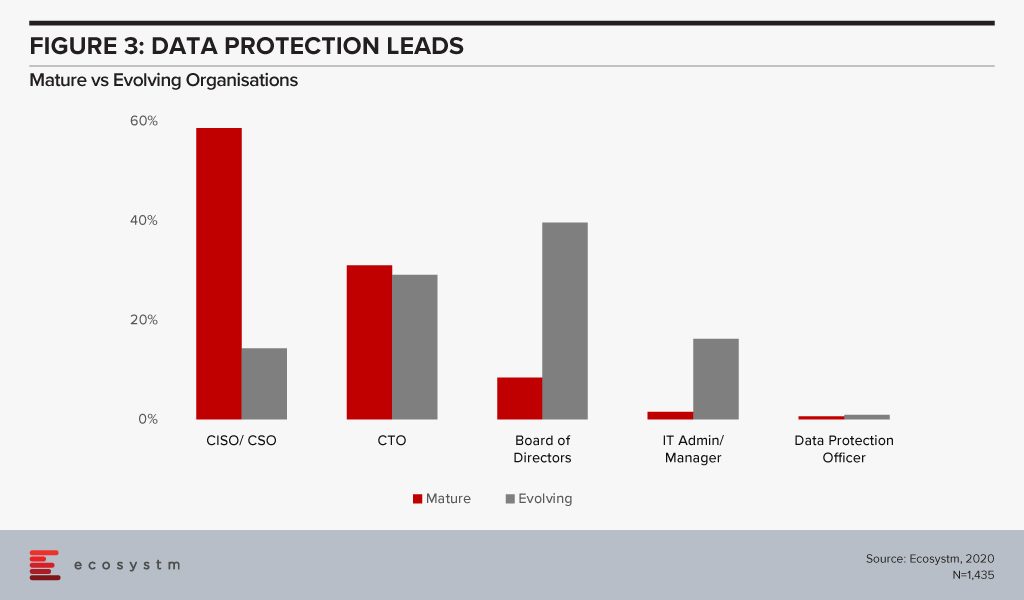
The reality is that many organisations – especially small and medium enterprises that have small dedicated security teams – will find it difficult to appoint a dedicated CSO/CISO. The study also finds that 80% of evolving organisations have less than 10 employees in their security teams as compared to only a third of mature organisations. Carl Woerndle, Principal Advisor Ecosystm, suggests these organisations look at the option of hiring a vCISO (virtual CISO). “A vCISO can help your organisation deliver a full security program within a fixed budget. Hiring someone external also has the added benefits of bringing objectivity to your security strategies and providing guidance on newer skills and technologies to your security teams.”
#4 Are you aware of Cloud Risk?
Cloud adoption has become mainstream, especially as organisations ramp up their digitalisation initiatives. It adds scale and agility to the organisation’s transformation investments. While security remains a key concern when it comes to cloud adoption, cloud is often regarded as a more secure option than on-premise. Cloud providers have dedicated security focus, constantly upgrade their security capabilities in response to newer threats and evolve their partner ecosystem. There is also better traceability with cloud as every virtual activity can be tracked, monitored, and is loggable.
However, mature organisations not only use on-prem options more for their sensitive data storage (Figure 4), they are also more skeptical about relying only on public cloud security features. Only 34% of mature organisations feel that public cloud security features do not need to be complemented while 52% of evolving organisations share that perception.
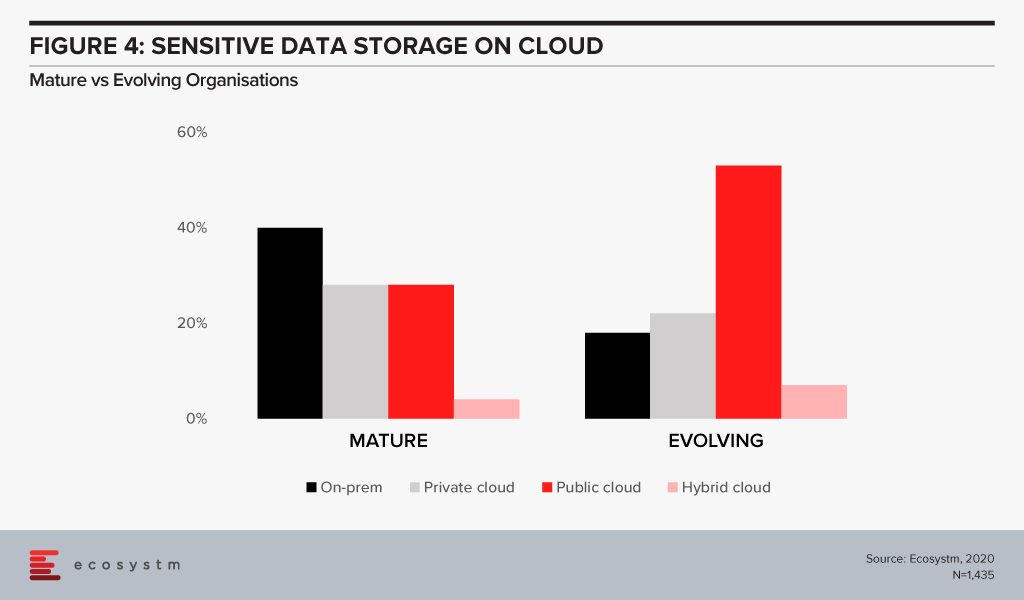
The cloud is as secure as an organisation makes it. The perception that there is no need to supplement public cloud security features can have disastrous outcomes. It is important to supplement the cloud provider’s security with event-driven security measures within an organisation’s applications and cloud interface. Alex says, “Assuming the big cloud providers have security covered for you is a huge mistake. Understanding the shared responsibility model is crucial in your public cloud adoption journey. The tools are available – but typically at an extra cost, and you need to employ, configure and continually manage them for effective security.”
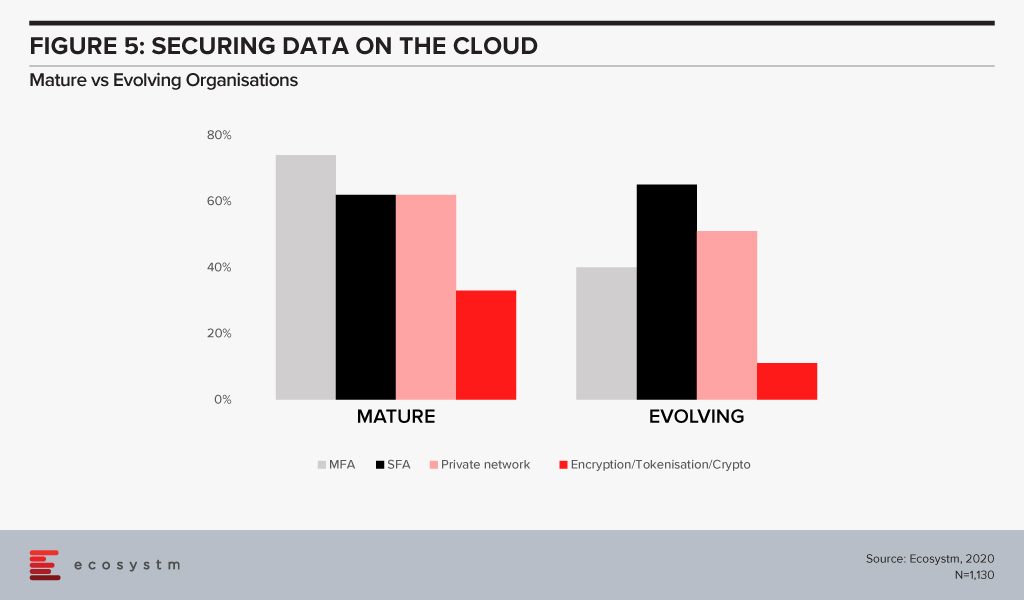
The big differentiator between mature and evolving organisations in securing cloud environments is in the use of multi-factor authentication (Figure 5). With 3/4th of mature organisations employing this as a control, it highlights that passwords – even strong passwords – alone, are not sufficient in 2020. Mature organisations are increasingly investing in encryption. But the perception of the complexity in deploying and managing encryption (and the keys) has been a challenge especially for organisations with smaller teams and less in-house technical capabilities.
#5 Are you Breach Ready?
Global organisations generally consider a data breach as inevitable – largely believing that “it is not about if, but when”(Figure 6). All organisations will face some incident, attempted breach or a breach, at some point. It is necessary to have the right cybersecurity measures to avoid breaches – but it is equally important to be prepared for when a breach actually happens. A majority of organisations, regardless of maturity, are worried about (and expect) a breach. For evolving organisations this is a troubling statistic given their use of public cloud with limited security understanding or controls – better education is needed from the public cloud providers but also the security industry.
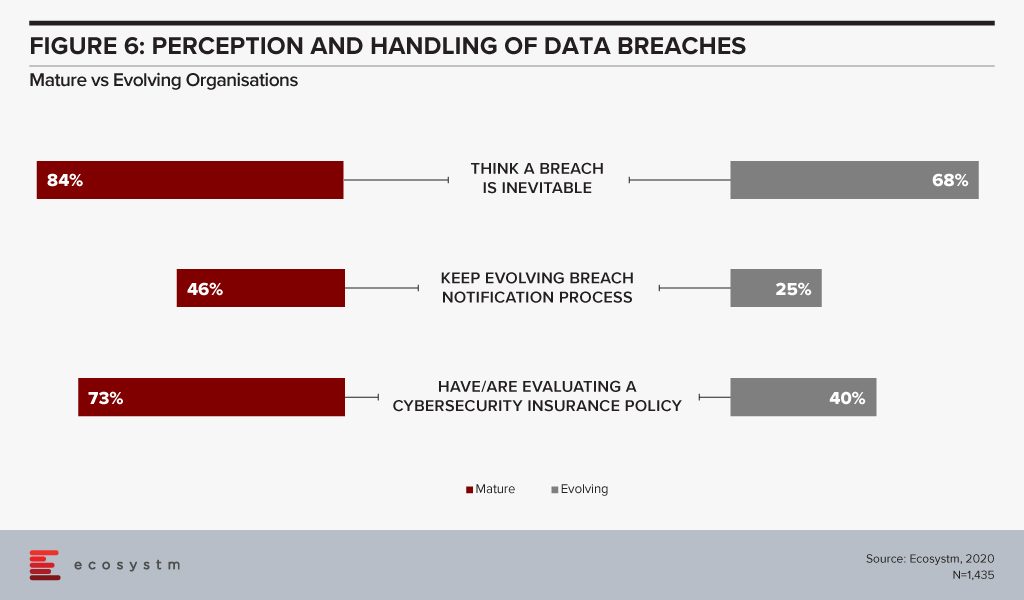
Breach notification processes need to keep evolving – and they must also include employees. Organisations should be aware of the need for people management during an incident. Policies might be clear and adhered to, but it is substantially harder to train the stakeholders involved, on how they will handle the breach emotionally. It extends to how an organisation manages their welfare both during an incident, and long after the incident response has been closed off.
“Cyber insurance has rapidly become a must-have as part of an organisation’s layered defence. While it provides a layer of support in the event of a breach, you should not rely on it as your only safety net,” Carl adds. “It is also important to ensure that your cyber cover is appropriate to your risks and organisational needs and policies should be evaluated carefully.”




