For many organisations migrating to cloud, the opportunity to run workloads from energy-efficient cloud data centres is a significant advantage. However, carbon emissions can vary from one country to another and if left unmonitored, will gradually increase over time as cloud use grows. This issue will become increasingly important as we move into the era of compute-intensive AI and the burden of cloud on natural resources will shift further into the spotlight.
The International Energy Agency (IEA) estimates that data centres are responsible for up to 1.5% of global electricity use and 1% of GHG emissions. Cloud providers have recognised this and are committed to change. Between 2025 and 2030, all hyperscalers – AWS, Azure, Google, and Oracle included – expect to power their global cloud operations entirely with renewable sources.
Chasing the Sun
Cloud providers are shifting their sights from simply matching electricity use with renewable power purchase agreements (PPA) to the more ambitious goal of operating 24/7 on carbon-free sources. A defining characteristic of renewables though is intermittency, with production levels fluctuating based on the availability of sunlight and wind. Leading cloud providers are using AI to dynamically distribute compute workloads throughout the day to regions with lower carbon intensity. Workloads that are processed with solar power during daylight can be shifted to nearby regions with abundant wind energy at night.
Addressing Water Scarcity
Many of the largest cloud data centres are situated in sunny locations to take advantage of solar power and proximity to population centres. Unfortunately, this often means that they are also in areas where water is scarce. While liquid-cooled facilities are energy efficient, local communities are concerned on the strain on water sources. Data centre operators are now committing to reduce consumption and restore water supplies. Simple measures, such as expanding humidity (below 20% RH) and temperature tolerances (above 30°C) in server rooms have helped companies like Meta to cut wastage. Similarly, Google has increased their reliance on non-potable sources, such as grey water and sea water.
From Waste to Worth
Data centre operators have identified innovative ways to reuse the excess heat generated by their computing equipment. Some have used it to heat adjacent swimming pools while others have warmed rooms that house vertical farms. Although these initiatives currently have little impact on the environmental impact of cloud, they suggest a future where waste is significantly reduced.
Greening the Grid
The giant facilities that cloud providers use to house their computing infrastructure are also set to change. Building materials and construction account for an astonishing 11% of global carbon emissions. The use of recycled materials in concrete and investing in greener methods of manufacturing steel are approaches the construction industry are attempting to lessen their impact. Smaller data centres have been 3D printed to accelerate construction and use recyclable printing concrete. While this approach may not be suitable for hyperscale facilities, it holds potential for smaller edge locations.
Rethinking Hardware Management
Cloud providers rely on their scale to provide fast, resilient, and cost-effective computing. In many cases, simply replacing malfunctioning or obsolete equipment would achieve these goals better than performing maintenance. However, the relentless growth of e-waste is putting pressure on cloud providers to participate in the circular economy. Microsoft, for example, has launched three Circular Centres to repurpose cloud equipment. During the pilot of their Amsterdam centre, it achieved 83% reuse and 17% recycling of critical parts. The lifecycle of equipment in the cloud is largely hidden but environmentally conscious users will start demanding greater transparency.
Recommendations
Organisations should be aware of their cloud-derived scope 3 emissions and consider broader environmental issues around water use and recycling. Here are the steps that can be taken immediately:
- Monitor GreenOps. Cloud providers are adding GreenOps tools, such as the AWS Customer Carbon Footprint Tool, to help organisations measure the environmental impact of their cloud operations. Understanding the relationship between cloud use and emissions is the first step towards sustainable cloud operations.
- Adopt Cloud FinOps for Quick ROI. Eliminating wasted cloud resources not only cuts costs but also reduces electricity-related emissions. Tools such as CloudVerse provide visibility into cloud spend, identifies unused instances, and helps to optimise cloud operations.
- Take a Holistic View. Cloud providers are being forced to improve transparency and reduce their environmental impact by their biggest customers. Getting educated on the actions that cloud partners are taking to minimise emissions, water use, and waste to landfill is crucial. In most cases, dedicated cloud providers should reduce waste rather than offset it.
- Enable Remote Workforce. Cloud-enabled security and networking solutions, such as SASE, allow employees to work securely from remote locations and reduce their transportation emissions. With a SASE deployed in the cloud, routine management tasks can be performed by IT remotely rather than at the branch, further reducing transportation emissions.

2024 has started cautiously for organisations, with many choosing to continue with tech projects that have already initiated, while waiting for clearer market conditions before starting newer transformation projects. This means that tech providers must continue to refine their market messaging and enhance their service/product offerings to strengthen their market presence in the latter part of the year. Ecosystm analysts present five key considerations for tech providers as they navigate evolving market and customer trends, this year.
Navigating Market Dynamics

Continuing Economic Uncertainties. Organisations will focus on ongoing projects and consider expanding initiatives in the latter part of the year. This means that tech providers should maintain visibility and trust with existing clients. They also need to help their customers meet multiple KPIs.
Popularity of Generative AI. For organisations, this will be the time to go beyond the novelty factor and assess practical business outcomes, allied costs, and change management. Tech providers need to include ROI discussions for short-term and mid-term perspectives as organisations move beyond pilots.
Infrastructure Market Disruption. Tech leaders will keep an eye out for advancements and disruptions in the market (likely to originate from the semiconductor sector). The disruptions might require tech vendors to re-assess the infrastructure partner ecosystem.
Need for New Tech Skills. Tech leaders will evaluate Generative AI’s impact on AIOps and IT Architecture; invest in upskilling for talent retention. Tech providers must prioritise creating user-friendly experiences to make technology accessible to business users. Training and partner enablement will also need a higher focus.
Increased Focus on Governance. Tech leaders will consult tech vendors on how to implement safeguards for data usage, sharing, and cybersecurity. This opens up opportunities in offering governance-related services.
5 Key Considerations for Tech Vendors
#1 Get Ready for the Year of the AI Startup

While many AI companies have been around for years, this will be the year that many of them make a significant play into enterprises in Asia Pacific. This comes at a time when many organisations are attempting to reduce tech debt and simplify their tech architecture.
For these AI startups to succeed, they will need to create watertight business cases, and do a lot of the hard work in pre-integrating their solutions with the larger platforms to reduce the time to value and simplify the systems integration work.
To respond to these emerging threats, existing tech providers will need to not only accelerate their own use of AI in their platforms, but also ramp up the education and promotion of these capabilities.
#2 Lead With Data, Not AI Capabilities

Organisations recognise the need for AI to enhance their workforce, improve customer experience, and automate processes. However, the initial challenge lies in improving data quality, as trust in early AI models hinges on high-quality training data for long-term success.
Tech vendors that can help with data source discovery, metadata analysis, and seamless data pipeline creation will emerge as trusted AI partners. Transformation tools that automate deduplication and quality assurance tasks empower data scientists to focus on high-value work. Automation models like Segment Anything enhance unstructured data labeling, particularly for images. Finally synthetic data will gain importance as quality sources become scarce.
Tech vendors will be tempted to capitalise on the Generative AI hype but for sake of positive early experiences, they should begin with data quality.
#3 Prepare Thoroughly for AI-driven Business Demand

Besides pureplay AI opportunities, AI will drive a renewed and increased interest in data and data management. Tech and service providers can capitalise on this by understanding the larger picture around their clients’ data maturity and governance. Initial conversations around AI can be door openers to bigger, transformational engagements.
Tech vendors should avoid the pitfall of downplaying AI risks. Instead, they should make all efforts to own and drive the conversation with their clients. They need to be forthcoming about their in-house responsible AI guidelines and understand what is happening in AI legislation world-wide (hint: a lot!)
Tech providers must establish strong client partnerships for AI initiatives to succeed. They must address risk and benefit equally to reap the benefits of larger AI-driven transformation engagements.
#4 Converge Network & Security Capabilities

Networking and security vendors will need to develop converged offerings as these two technologies increasingly overlap in the hybrid working era. Organisations are now entering a new phase of maturity as they evolve their remote working policies and invest in tools to regain control. They will require simplified management, increased visibility, and to provide a consistent user experience, wherever employees are located.
There has already been a widespread adoption of SD-WAN and now organisations are starting to explore next generation SSE technologies. Procuring these capabilities from a single provider will help to remove complexity from networks as the number of endpoints continue to grow.
Tech providers should take a land and expand approach, getting a foothold with SASE modules that offer rapid ROI. They should focus on SWG and ZTNA deals with an eye to expanding in CASB and FWaaS, as customers gain experience.
#5 Double Down on Your Partner Ecosystem

The IT services market, particularly in Asia Pacific, is poised for significant growth. Factors, including the imperative to cut IT operational costs, the growing complexity of cloud migrations and transformations, change management for Generative AI capabilities, and rising security and data governance needs, will drive increased spending on IT services.
Tech services providers – consultants, SIs, managed services providers, and VARs – will help drive organisations’ tech spend and strategy. This is a good time to review partners, evaluating whether they can take the business forward, or whether there is a need to expand or change the partner mix.
Partner reviews should start with an evaluation of processes and incentives to ensure they foster desired behaviour from customers and partners. Tech vendors should develop a 21st century partner program to improve chances of success.

Hewlett Packard Enterprise (HPE) has entered into a definitive agreement to acquire Juniper Networks for USD 40 per share, totaling an equity value of about USD 14 Billion. This strategic move is aimed to enhance HPE’s portfolio by focusing on higher-growth solutions and reinforcing their high-margin networking business. HPE expects to double their networking business, positioning the combined entity as a leader in networking solutions. With the growing demand for secure, unified technology driven by AI and hybrid cloud trends, HPE aims to offer comprehensive, disruptive solutions that connect, protect, and analyse data from edge to cloud.
This would also be the organisation’s largest deal since becoming an independent company in 2015. The acquisition is expected to be completed by late 2024 or early 2025.
Ecosystm analysts Darian Bird and Richard Wilkins provide their insights on the HPE acquisition and its implications for the tech market.

Converging Networking and Security
One of the big drawcards for HPE is Juniper’s Mist AI. The networking vendors have been racing to catch up – both in capabilities and in marketing. The acquisition though will give HPE a leadership position in network visibility and manageability. With GreenLake and soon Mist AI, HPE will have a solid AIOps story across the entire infrastructure.
HPE has been working steadily towards becoming a player in the converged networking-security space. They integrated Silver Peak well to make a name for themselves in SD-WAN and last year acquiring Axis Security gave them the Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB) modules in the Secure Service Edge (SSE) stack. Bringing all of this to the market with Juniper’s networking prowess positions HPE as a formidable player, especially as the Secure Access Service Edge (SASE) market gains momentum.
As the market shifts towards converged SASE, there will only be more interest in the SD-WAN and SSE vendors. In just over one year, Cato Networks and Netskope have raised funds, Check Point acquired Perimeter 81, and Versa Networks has made noises about an IPO. The networking and security players are all figuring out how they can deliver a single-vendor SASE.
Although HPE’s strategic initiatives signal a robust market position, potential challenges arise from the overlap between Aruba and Juniper. However, the distinct focus on the edge and data center, respectively, may help alleviate these concerns. The acquisition also marks HPE’s foray into the telecom space, leveraging its earlier acquisition of Athonet and establishing a significant presence among service providers. This expansion enhances HPE’s overall market influence, posing a challenge to the long-standing dominance of Cisco.

The strategic acquisition of Juniper Networks by HPE can make a transformative leap in AIOps and Software-Defined Networking (SDN). There is a potential for this to establish a new benchmark in IT management.
AI in IT Operations Transformation
The integration of Mist’s AI-driven wireless solutions and HPE’s SDN is a paradigm shift in IT operations management and will help organisations transition from a reactive to a predictive and proactive model. Mist’s predictive analytics, coupled with HPE’s SDN capabilities, empower networks to dynamically adjust to user demands and environmental changes, ensuring optimal performance and user experience. Marvis, Mist’s Virtual Network Assistant (VNA), adds conversational troubleshooting capabilities, enhancing HPE’s network solutions. The integration envisions an IT ecosystem where Juniper’s AI augments HPE’s InfoSight, providing deeper insights into network behaviour, preemptive security measures, and more autonomous IT operations.
Transforming Cloud and Edge Computing
The incorporation of Juniper’s AI into HPE’s cloud and edge computing solutions promises a significant improvement in data processing and management. AI-driven load balancing and resource allocation mechanisms will significantly enhance multi-cloud environment efficiency, ensuring robust and seamless cloud services, particularly vital in IoT applications where real-time data processing is critical. This integration not only optimises cloud operations but also has the potential to align with HPE’s commitment to sustainability, showcasing how AI advancements can contribute to energy conservation.
In summary, HPE’s acquisition of Juniper Networks, and specifically the integration of the Mist AI platform, is a pivotal step towards an AI-driven, efficient, and predictive IT infrastructure. This can redefine the standards in AIOps and SDN, creating a future where IT systems are not only reactive but also intuitively adaptive to the evolving demands of the digital landscape.

2023 has been an eventful year. In May, the WHO announced that the pandemic was no longer a global public health emergency. However, other influencers in 2023 will continue to impact the market, well into 2024 and beyond.
Global Conflicts. The Russian invasion of Ukraine persisted; the Israeli-Palestinian conflict escalated into war; African nations continued to see armed conflicts and political crises; there has been significant population displacement.
Banking Crisis. American regional banks collapsed – Silicon Valley Bank and First Republic Bank collapses ranking as the third and second-largest banking collapses in US history; Credit Suisse was acquired by UBS in Switzerland.
Climate Emergency. The UN’s synthesis report found that there’s still a chance to limit global temperature increases by 1.5°C; Loss and Damage conversations continued without a significant impact.
Power of AI. The interest in generative AI models heated up; tech vendors incorporated foundational models in their enterprise offerings – Microsoft Copilot was launched; awareness of AI risks strengthened calls for Ethical/Responsible AI.
Click below to find out what Ecosystm analysts Achim Granzen, Darian Bird, Peter Carr, Sash Mukherjee and Tim Sheedy consider the top 5 tech market forces that will impact organisations in 2024.
Click here to download ‘Ecosystm Predicts: Tech Market Dynamics 2024’ as a PDF
#1 State-sponsored Attacks Will Alter the Nature Of Security Threats
It is becoming clearer that the post-Cold-War era is over, and we are transitioning to a multi-polar world. In this new age, malevolent governments will become increasingly emboldened to carry out cyber and physical attacks without the concern of sanction.
Unlike most malicious actors driven by profit today, state adversaries will be motivated to maximise disruption.
Rather than encrypting valuable data with ransomware, wiper malware will be deployed. State-sponsored attacks against critical infrastructure, such as transportation, energy, and undersea cables will be designed to inflict irreversible damage. The recent 23andme breach is an example of how ethnically directed attacks could be designed to sow fear and distrust. Additionally, even the threat of spyware and phishing will cause some activists, journalists, and politicians to self-censor.

#2 AI Legislation Breaches Will Occur, But Will Go Unpunished
With US President Biden’s recently published “Executive order on Safe, Secure and Trustworthy AI” and the European Union’s “AI Act” set for adoption by the European Parliament in mid-2024, codified and enforceable AI legislation is on the verge of becoming reality. However, oversight structures with powers to enforce the rules are currently not in place for either initiative and will take time to build out.
In 2024, the first instances of AI legislation violations will surface – potentially revealed by whistleblowers or significant public AI failures – but no legal action will be taken yet.

#3 AI Will Increase Net-New Carbon Emissions
In an age focused on reducing carbon and greenhouse gas emissions, AI is contributing to the opposite. Organisations often fail to track these emissions under the broader “Scope 3” category. Researchers at the University of Massachusetts, Amherst, found that training a single AI model can emit over 283T of carbon dioxide, equal to emissions from 62.6 gasoline-powered vehicles in a year.
Organisations rely on cloud providers for carbon emission reduction (Amazon targets net-zero by 2040, and Microsoft and Google aim for 2030, with the trajectory influencing global climate change); yet transparency on AI greenhouse gas emissions is limited. Diverse routes to net-zero will determine the level of greenhouse gas emissions.
Some argue that AI can help in better mapping a path to net-zero, but there is concern about whether the damage caused in the process will outweigh the benefits.

#4 ESG Will Transform into GSE to Become the Future of GRC
Previously viewed as a standalone concept, ESG will be increasingly recognised as integral to Governance, Risk, and Compliance (GRC) practices. The ‘E’ in ESG, representing environmental concerns, is becoming synonymous with compliance due to growing environmental regulations. The ‘S’, or social aspect, is merging with risk management, addressing contemporary issues such as ethical supply chains, workplace equity, and modern slavery, which traditional GRC models often overlook. Governance continues to be a crucial component.
The key to organisational adoption and transformation will be understanding that ESG is not an isolated function but is intricately linked with existing GRC capabilities.
This will present opportunities for GRC and Risk Management providers to adapt their current solutions, already deployed within organisations, to enhance ESG effectiveness. This strategy promises mutual benefits, improving compliance and risk management while simultaneously advancing ESG initiatives.

#5 Productivity Will Dominate Workforce Conversations
The skills discussions have shifted significantly over 2023. At the start of the year, HR leaders were still dealing with the ‘productivity conundrum’ – balancing employee flexibility and productivity in a hybrid work setting. There were also concerns about skills shortage, particularly in IT, as organisations prioritised tech-driven transformation and innovation.
Now, the focus is on assessing the pros and cons (mainly ROI) of providing employees with advanced productivity tools. For example, early studies on Microsoft Copilot showed that 70% of users experienced increased productivity. Discussions, including Narayana Murthy’s remarks on 70-hour work weeks, have re-ignited conversations about employee well-being and the impact of technology in enabling employees to achieve more in less time.
Against the backdrop of skills shortages and the need for better employee experience to retain talent, organisations are increasingly adopting/upgrading their productivity tools – starting with their Sales & Marketing functions.


The Banking, Financial Services, and Insurance (BFSI) industry, known for its cautious stance on technology, is swiftly undergoing a transformational modernisation journey. Areas such as digital customer experiences, automated fraud detection, and real-time risk assessment are all part of a technology-led roadmap. This shift is transforming the cybersecurity stance of BFSI organisations, which have conventionally favoured centralising everything within a data centre behind a firewall.
Ecosystm research finds that 75% of BFSI technology leaders believe that a data breach is inevitable. This requires taking a new cyber approach to detect threats early, reduce the impact of an attack, and avoid lateral movement across the network.
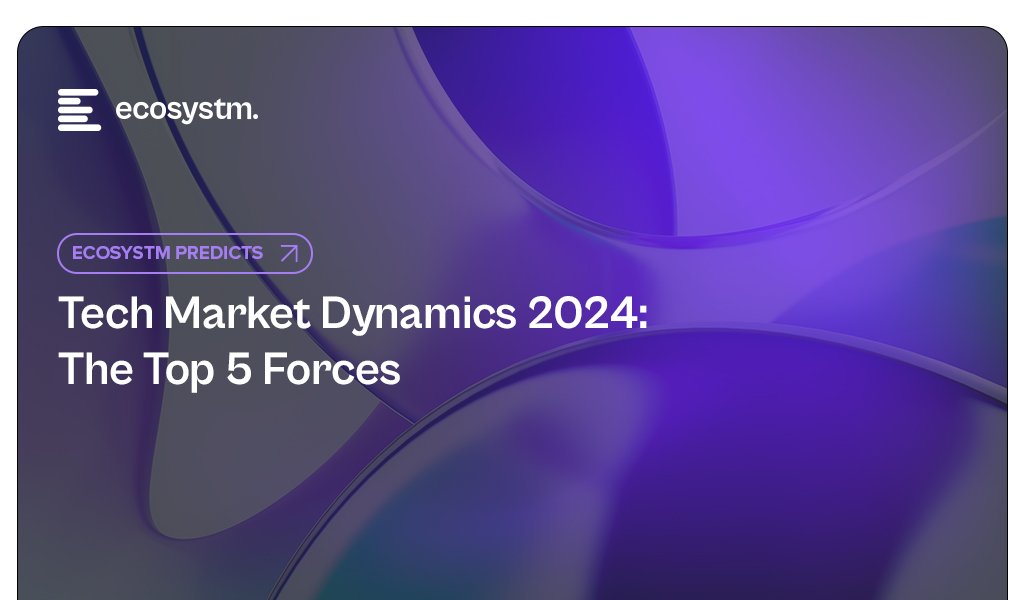
BFSI organisations will boost investments in two main areas over the next year: updating infrastructure and software, and exploring innovative domains like digital workplaces and automation. Cybersecurity investments are crucial in both of these areas.
As a regulated industry, breaches come with significant cost implications, underscoring the need to prioritise cybersecurity. BFSI cybersecurity and risk teams need to constantly reassess their strategies for safeguarding data and fulfilling compliance obligations, as they explore ways to facilitate new services for customers, partners, and employees.
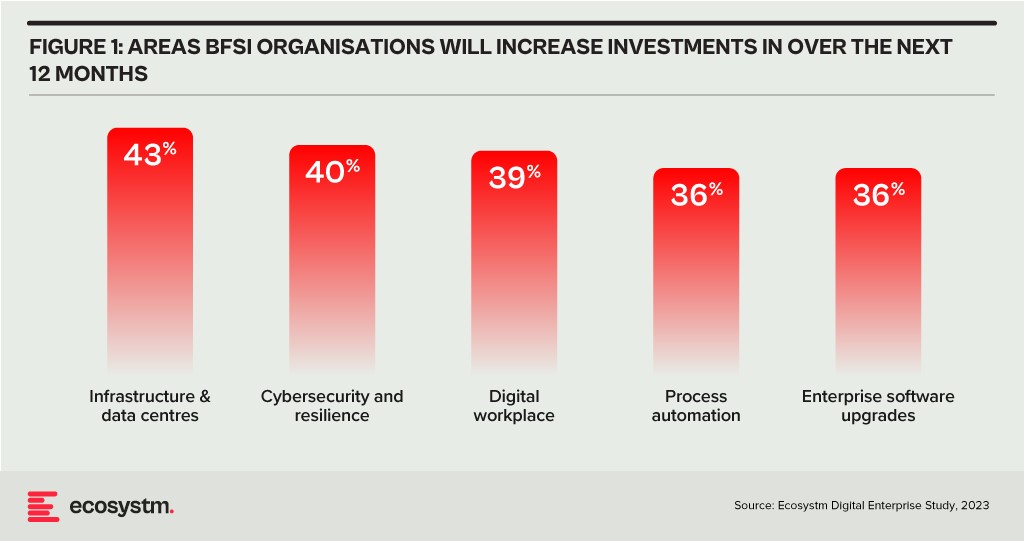
The primary concerns of BFSI CISOs can be categorised into two distinct groups:
- Expanding Technology Use. This includes the proliferation of applications and devices, as well as data access beyond the network perimeter.
- Employee-Related Vulnerabilities. This involves responses to phishing and malware attempts, as well as intentional and unintentional misuse of technology.
Vulnerabilities Arising from Employee Actions
Security vulnerabilities arising from employee actions and unawareness represent a significant and ongoing concern for businesses of all sizes and industries – the risks are just much bigger for BFSI. These vulnerabilities can lead to data breaches, financial losses, damage to reputation, and legal ramifications. A multi-pronged approach is needed that combines technology, training, policies, and a culture of security consciousness.
Training and Culture. BFSI organisations prioritise comprehensive training and awareness programs, educating employees about common threats like phishing and best practices for safeguarding sensitive data. While these programs are often ongoing and adaptable to new threats, they can sometimes become mere compliance checklists, raising questions about their true effectiveness. Conducting simulated phishing attacks and security quizzes to assess employee awareness and identify areas where further training is required, can be effective.
To truly educate employees on risks, it’s essential to move beyond compliance and build a cybersecurity culture throughout the organisation. This can involve setting organisation-wide security KPIs that cascade from the CEO down to every employee, promoting accountability and transparency. Creating an environment where employees feel comfortable reporting security concerns is critical for early threat detection and mitigation.
Policies. Clear security policies and enforcement are essential for ensuring that employees understand their roles within the broader security framework, including responsibilities on strong password use, secure data handling, and prompt incident reporting. Implementing the principle of least privilege, which restricts access based on specific roles, mitigates potential harm from insider threats and inadvertent data exposure. Policies should evolve through routine security audits, including technical assessments and evaluations of employee protocol adherence, which will help organisations with a swifter identification of vulnerabilities and to take the necessary corrective actions.
However, despite the best efforts, breaches do happen – and this is where a well-defined incident response plan, that is regularly tested and updated, is crucial to minimise the damage. This requires every employee to know their roles and responsibilities during a security incident.
Tech Expansion Leading to Cyber Complexity
Cloud. Initially hesitant to transition essential workloads to the cloud, the BFSI industry has experienced a shift in perspective due to the rise of inventive SaaS-based Fintech tools and hybrid cloud solutions, that have created new impetus for change. This new distributed architecture requires a fresh look at cyber measures. Secure Access Service Edge (SASE) providers are integrating a range of cloud-delivered safeguards, such as FWaaS, CASB, and ZTNA with SD-WAN to ensure organisations can securely access the cloud without compromising on performance.
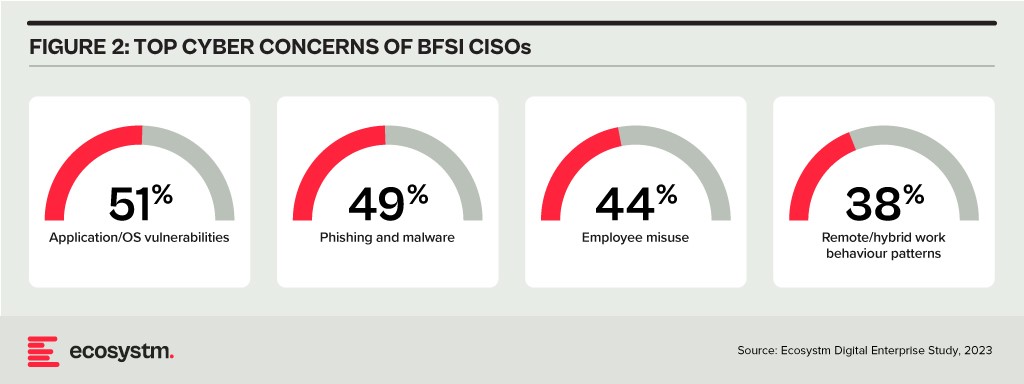
Data & AI. Data holds paramount importance in the BFSI industry for informed decision-making, personalised customer experiences, risk assessment, fraud prevention, and regulatory compliance. AI applications are being used to tailor products and services, optimise operational efficiency, and stay competitive in an evolving market. As part of their technology modernisation efforts, 47% of BFSI institutions are refining their data and AI strategies. They also acknowledge the challenges associated – and satisfying risk, regulatory, and compliance requirements is one of the biggest challenges facing BFSI organisations in the AI deployments.
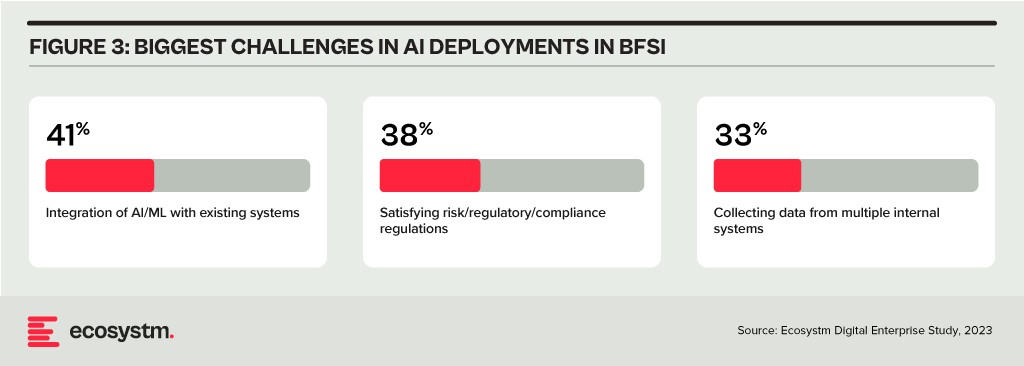
The rush to experiment with Generative AI and foundation models to assist customers and employees is only heightening these concerns. There is an urgent need for policies around the use of these emerging technologies. Initiatives such as the Monetary Authority of Singapore’s Veritas that aim to enable financial institutions to evaluate their AI and data analytics solutions against the principles of fairness, ethics, accountability, and transparency (FEAT) are expected to provide the much-needed guidance to the industry.
Digital Workplace. As with other industries with a high percentage of knowledge workers, BFSI organisations are grappling with granting remote access to staff. Cloud-based collaboration and Fintech tools, BYOD policies, and sensitive data traversing home networks are all creating new challenges for cyber teams. Modern approaches, such as zero trust network access, privilege management, and network segmentation are necessary to ensure workers can seamlessly but securely perform their roles remotely.
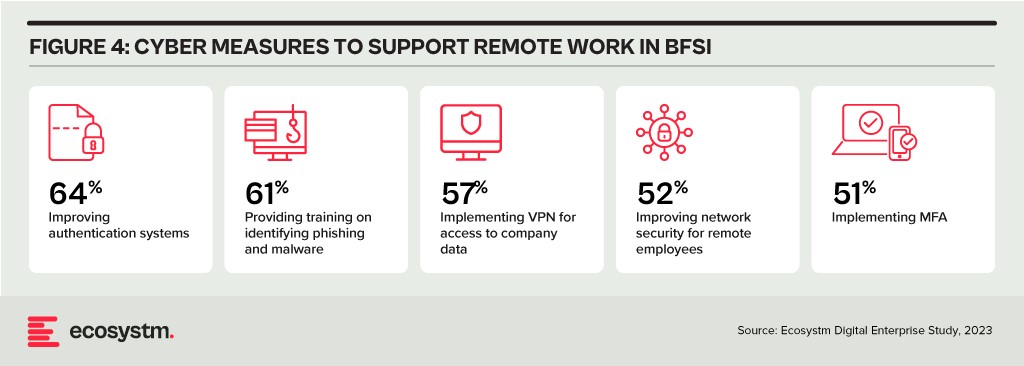
Looking Beyond Technology: Evaluating the Adequacy of Compliance-Centric Cyber Strategies
The BFSI industry stands among the most rigorously regulated industries, with scrutiny intensifying following every collapse or notable breach. Cyber and data protection teams shoulder the responsibility of understanding the implications of and adhering to emerging data protection regulations in areas such as GDPR, PCI-DSS, SOC 2, and PSD2. Automating compliance procedures emerges as a compelling solution to streamline processes, mitigate risks, and curtail expenses. Technologies such as robotic process automation (RPA), low-code development, and continuous compliance monitoring are gaining prominence.
The adoption of AI to enhance security is still emerging but will accelerate rapidly. Ecosystm research shows that within the next two years, nearly 70% of BFSI organisations will have invested in SecOps. AI can help Security Operations Centres (SOCs) prioritise alerts and respond to threats faster than could be performed manually. Additionally, the expanding variety of network endpoints, including customer devices, ATMs, and tools used by frontline employees, can embrace AI-enhanced protection without introducing additional onboarding friction.
However, there is a need for BFSI organisations to look beyond compliance checklists to a more holistic cyber approach that can prioritise cyber measures continually based on the risk to the organisations. And this is one of the biggest challenges that BFSI CISOs face. Ecosystm research finds that 72% of cyber and technology leaders in the industry feel that there is limited understanding of cyber risk and governance in their organisations.
In fact, BFSI organisations must look at the interconnectedness of an intelligence-led and risk-based strategy. Thorough risk assessments let organisations prioritise vulnerability mitigation effectively. This targeted approach optimises security initiatives by focusing on high-risk areas, reducing security debt. To adapt to evolving threats, intelligence should inform risk assessment. Intelligence-led strategies empower cybersecurity leaders with real-time threat insights for proactive measures, actively tackling emerging threats and vulnerabilities – and definitely moving beyond compliance-focused strategies.

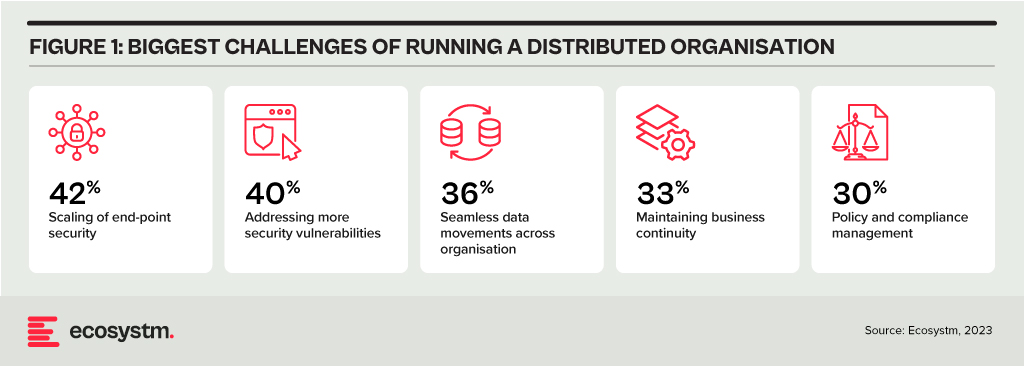
Traditional network architectures are inherently fragile, often relying on a single transport type to connect branches, production facilities, and data centres. The imperative for networks to maintain resilience has grown significantly, particularly due to the delivery of customer-facing services at branches and the increasing reliance on interconnected machines in operational environments. The cost of network downtime can now be quantified in terms of both lost customers and reduced production.
Distributed Enterprises Face New Challenges
As the importance of maintaining resiliency grows, so does the complexity of network management. Distributed enterprises must provide connectivity under challenging conditions, such as:
- Remote access for employees using video conferencing
- Local breakout for cloud services to avoid backhauling
- IoT devices left unattended in public places
- Customers accessing digital services at the branch or home
- Sites in remote areas requiring the same quality of service
Network managers require intelligent tools to remain in control without adding any unnecessary burden to end users. The number of endpoints and speed of change has made it impossible for human operators to manage without assistance from AI.
AI-Enhanced Network Management
Modern network operations centres are enhancing their visibility by aggregating data from diverse systems and consolidating them within a unified management platform. Machine learning (ML) and AI are employed to analyse data originating from enterprise networks, telecom Points of Presence (PoPs), IoT devices, cloud service providers, and user experience monitoring. These technologies enable the early identification of network issues before they reach critical levels. Intelligent networks can suggest strategies to enhance network resilience, forecast how modifications may impact performance, and are increasingly capable of autonomous responses to evolving conditions.
Here are some critical ways that AI/ML can help build resilient networks.
- Alert Noise Reduction. Network operations centres face thousands of alerts each day. As a result, operators battle with alert fatigue and are challenged to identify critical issues. Through the application of ML, contemporary monitoring tools can mitigate false positives, categorise interconnected alerts, and assist operators in prioritising the most pressing concerns. An operations team, augmented with AI capabilities could potentially de-prioritise up to 90% of alerts, allowing a concentrated focus on factors that impact network performance and resilience.
- Data Lakes. Networking vendors are building their own proprietary data lakes built upon telemetry data generated by the infrastructure they have deployed at customer sites. This vast volume of data allows them to use ML to create a tailored baseline for each customer and to recommend actions to optimise the environment.
- Root Cause Analysis. To assist network operators in diagnosing an issue, AIOps can sift through thousands of data points and correlate them to identify a root cause. Through the integration of alerts with change feeds, operators can understand the underlying causes of network problems or outages. By using ML to understand the customer’s unique environment, AIOps can progressively accelerate time to resolution.
- Proactive Response. As management layers become capable of recommending corrective action, proactive response also becomes possible, leading to self-healing networks. With early identification of sub-optimal conditions, intelligent systems can conduct load balancing, redirect traffic to higher performing SaaS regions, auto-scale cloud instances, or terminate selected connections.
- Device Profiling. In a BYOD environment, network managers require enhanced visibility to discover devices and enforce appropriate policies on them. Automated profiling against a validated database ensures guest access can be granted without adding friction to the onboarding process. With deep packet inspection, devices can be precisely classified based on behaviour patterns.
- Dynamic Bandwidth Aggregation. A key feature of an SD-WAN is that it can incorporate diverse transport types, such as fibre, 5G, and low earth orbit (LEO) satellite connectivity. Rather than using a simple primary and redundant architecture, bandwidth aggregation allows all circuits to be used simultaneously. By infusing intelligence into the SD-WAN layer, the process of path selection can dynamically prioritise traffic by directing it over higher quality or across multiple links. This approach guarantees optimal performance, even in the face of network degradation.
- Generative AI for Process Efficiency. Every tech company is trying to understand how they can leverage the power of Generative AI, and networking providers are no different. The most immediate use case will be to improve satisfaction and scalability for level 1 and level 2 support. A Generative AI-enabled service desk could provide uninterrupted support during high-volume periods, such as during network outages, or during off-peak hours.
Initiating an AI-Driven Network Management Journey
Network managers who take advantage of AI can build highly resilient networks that maximise uptime, deliver consistently high performance, and remain secure. Some important considerations when getting started include:
- Data Catalogue. Take stock of the data sources that are available to you, whether they come from network equipment telemetry, applications, or the data lake of a managed services provider. Understand how they can be integrated into an AIOps solution.
- Start Small. Begin with a pilot in an area where good data sources are available. This will help you assess the impact that AI could have on reducing alerts, improving mean time to repair (MTTR), increasing uptime, or addressing the skills gap.
- Develop an SD-WAN/SASE Roadmap. Many advanced AI benefits are built into an SD-WAN or SASE. Most organisations already have or will soon adopt SD-WAN but begin assessing the SASE framework to decide if it is suitable for your organisation.

In 2023, organisations will continue to reinvent themselves to remain relevant to their customers, engage their employees and be efficient and profitable.
As per Ecosystm’s Digital Enterprise Study 2022, organisations will increase spend on digital workplace technologies, enterprise software upgrades, mobile applications, infrastructure and data centres, and hybrid cloud management.
Here are the top 5 trends for the Distributed Enterprise in 2023 according to Ecosystm analysts, Alea Fairchild, Darian Bird, Peter Carr, and Tim Sheedy.
- Deskless Workers Will Become Modern Professionals
- Need for Cost Efficiency Will Stimulate the Use of Waste Metrics in Public Cloud
- The Climate & Energy Crisis Will Change the Cloud Equation
- Industry Cloud Will Further Accelerate Business Innovation
- The SASE Piece Will Fall in Place
Read on for more details.
Download Ecosystm Predicts: The Top 5 Trends for the Distributed Enterprise in 2023

Against a backdrop of extended disruption, cybersecurity risks are expanding rapidly and current defences are inadequate. Ransomware attacks are increasing in frequency and impact, focusing more on targets where outages are not an option, such as critical infrastructure and hospitals. Supply chain attacks are creating chaos and has led to a much-needed focus on supply chain vulnerabilities.
As digitalisation continues at a faster pace, cybersecurity is too often, a secondary concern.
With the acceleration of cloud adoption; widespread remote working; the resulting proliferation of endpoints; and the expansion of attack surface for malicious actors, this is the time for organisations to transform their cybersecurity approaches.
Here are the 5 steps that you should consider:
- Having CISOs report directly into top management – bypassing CIOs
- Focusing on configuration management
- Building resilience against ransomware attacks
- Migrating away from a legacy perimeter-based approach
- Shifting to Policy-as-Code
In 2022, attacks on organisations will grow in frequency and intensity. Organisations need to transform their approaches to cybersecurity. This involves embracing new concepts such as zero-trust and Secure Access Service Edge (SASE) as well as a stronger focus on policy as code and human factors.
Click here to download Shaping your Cyber Practice in 2022 as a PDF

Cyber operations become more complex with distributed company assets due to the hybrid work model; the need to revamp supply chains; and constantly monitor business continuity measures. And of course, 2021 has shown us that hackers are getting smarter and more vicious. Attacks now often originate from what appears to be trusted devices, people, applications – that reside inside the network. This will drive organisations to continue to focus on cybersecurity, and tech providers to develop on security by design in 2022.
Read on to find out what Ecosystm Analysts, Andrew Milroy and Claus Mortensen think will be the leading cybersecurity and compliance trends in 2022.