New ‘as-a-service’ products are continuing to expand the options that are available to organisations, fragmenting the functionality used across many technology providers. Choosing the right products is getting more and more difficult – kind of like trying to choose your VOD service at home.
How many VOD networks do you use?
Do you remember the time when your access to video content was through either broadcast TV or cable TV? And when a regular trip to the video store was part of life? And you had to watch programs when the networks scheduled them?
Most programming was only available through one of those media, particularly if you wanted to see the latest series or movies. In some countries, we paid a TV license fee that partly paid for the government-funded free-to-air network. For those with access to cable or satellite TV, we paid a monthly fee for a smorgasbord of channels, most of which we never watched.
Today, we still have those options, but an explosion of video-on-demand (VOD) options has occurred. Each of them requires a separate contract that users rarely read. So we have little knowledge of what these services have contracted to deliver or how they will use our data. But we have an amazing range of content available if we want.
At least most are monthly services that we can cancel at short notice unless you take advantage of the price reduction for subscribing for a year or longer.
How many as-a-service products are you choosing?
Translate this to an organisation that is increasingly using as-a-service products. Choosing a service to use has much more complex requirements, there are more options available and happens more frequently.
If we think the domestic landscape for video is complicated, the options for as-a-service are significantly more fragmented. The most frequently used approach to selecting VOD services is to choose those that offer the content you want to see.
Choosing the appropriate as-a-service offering is much harder as the functional, security, integration and pricing requirements are much more complex than wanting to see a particular movie or drama series.
Suppliers of these services do not make it easy to understand what you get for your money. They decide to bundle or unbundle functions depending on a mix of factors to differentiate themselves for customers. This makes value and price comparisons difficult.
For example, there is a myriad of CRM suppliers out there offering a complex matrix of pricing and functionality options. And in each case, there is often an ecosystem of suppliers providing different pieces of functionality. No one provider delivers all the functionality that we desire.
Organisations wanting to choose as-a-service products need to be very clear on which requirements are the most important to them, and how well each supplier meets those specific needs. They cannot afford to be distracted by less valuable features.
It is extremely unlikely that one tech vendor will be able to provide all the desired features. Increasingly, other vendors will supplement the core functionality with niche features. So the selection has to take into account the ecosystem around the core as-a-service functionality.

Recommendations
Tech buyers should make sure they have a clear definition and priority for the features that they require for each purpose. Added to this they need to be very clear what they want in a single package, and what they are prepared to purchase from a wider ecosystem. Both need to be part of the selection criteria.
Once implemented, changing as-a-service products is a much more difficult proposition than switching VOD providers.
Tech vendors need to stay away from confusion marketing to make it possible for buyers to understand what they are getting. They need to help customers gain a clear understanding of any ecosystem they participate in, and what this means for the buyer.
The consequences of getting this choice right are dramatically more important than choosing the VOD provider with the programming you want.
And we know how difficult that choice has become.

Ecosystm recently partnered with Asavie to conduct a study on the opportunity and outlook for the “Branch of One“. The results of the study make us question whether organisations’ mobile security strategies are appropriate for the evolving business priorities, the ever-changing threat landscape, and a seamless employee experience.
To answer this question, organisations will need to examine their security frameworks.
COVID-19 has forced organisations to realise that cybersecurity is not only a business enabler – it is a business prerequisite. Our research shows that businesses world-wide no longer see the pandemic as something that we need to get through to get back to “business as usual”. Most acknowledge that remote working and access from anywhere will be the new normal for many employees and that means they need to revisit and reprioritise their spending and their focus.
In many cases, existing procedures and policies are not sufficient to cover this new working environment – and often the policies have not been clearly communicated to all employees. Moreover, many organisations still rely on legacy WAN technologies that make secure and flexible access difficult – something that my colleague, Tim Sheedy touched upon in his recent blog post.
The choice of WAN technology is an important part of any mobile security strategy, but so is the approach to securing endpoints on the WAN and – what is perhaps the weakest link – the behaviour of employees.
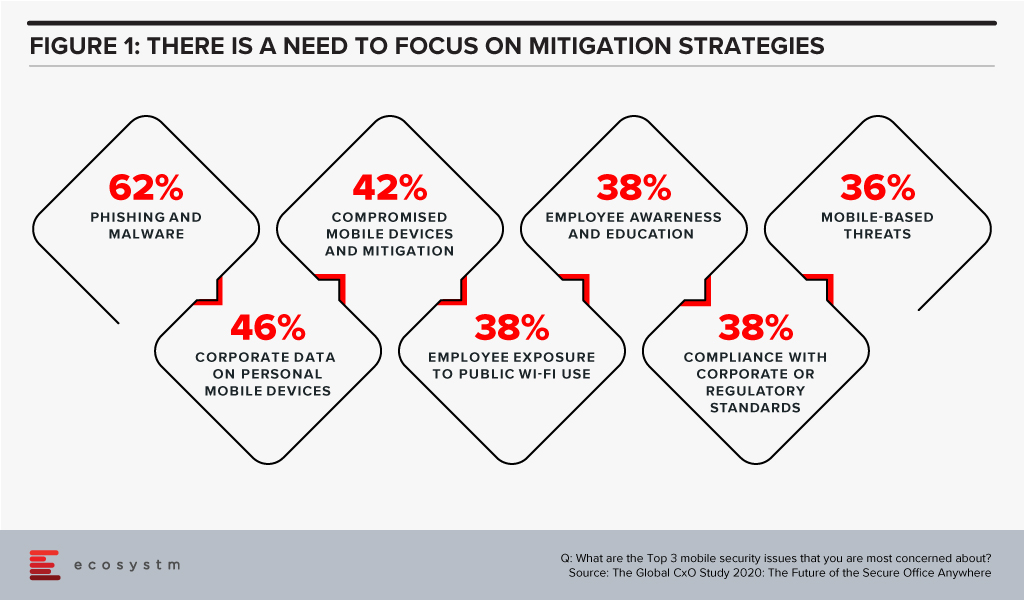
The Global CxO Study 2020: The Future of Secure Office Anywhere showed us that when it came to mobile security, organisations were mostly worried about phishing and malware – but 4 out of the top 5 mobile security concerns involved human error and failure to follow corporate IT security policies and guidelines (Figure 1).
Time to Evaluate New Mobile Security Features
This highlights the importance of a couple of “security features” that many IT organisations still tend to overlook – convenience and ease-of-use. When employees ignore IT policies, bypass security steps, use unsanctioned personal devices to process work data etc., they tend to do so for mainly one reason: because it is convenient for them. Employees just want to get the work done and following security protocols, making sure that devices have the right security software installed etc. is simply seen as too cumbersome or as slowing down the work process.
To counter this, ease-of-use and convenience need to an integral part of any security framework – especially when employees are no longer working in the office. IT managers tend to be a bit ego-centric when they think of these terms, i.e. for them ease-of-use relates to their experience in implementing and running the systems, but they really need to be extending the ease to their users – the employees – as well.
This is where Branch of One comes to the fore. It offers the convenience of employees not having to install or connect software or hardware on the mobile device and it allows administrators to easily scale and manage their mobile security framework. Security frameworks do not have to be in the way of getting the work done. Branch of One shows us that comprehensive mobile security can be nearly seamless.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.




