The last few months have been full of bad news for some of the organisations currently recognised as the most innovative firms on the planet. Netflix has been losing subscribers, Amazon’s revenue growth is slowing dramatically, and Tesla now has serious competition in the EV market, with its dominance beginning to wane. In Australia – my home country – some of the “fintech” banks have closed their virtual doors over the past six months, leaving the market to the traditional players.
And many of the traditional businesses are turning themselves around. Foxtel, the “legacy” cable TV provider in Australia, has grown its subscriber base by 19% off the back of its streaming services – where subscriber numbers are growing at over 60% YoY. ComfortDelgro – a transport provider based out of Singapore – is seeing its revenue start to increase again after being hit hard by digital competitors and the pandemic. CBA’s “Ceba” virtual assistant is winning plaudits in Australia and globally.
It’s Not Too Late to Catch-up!
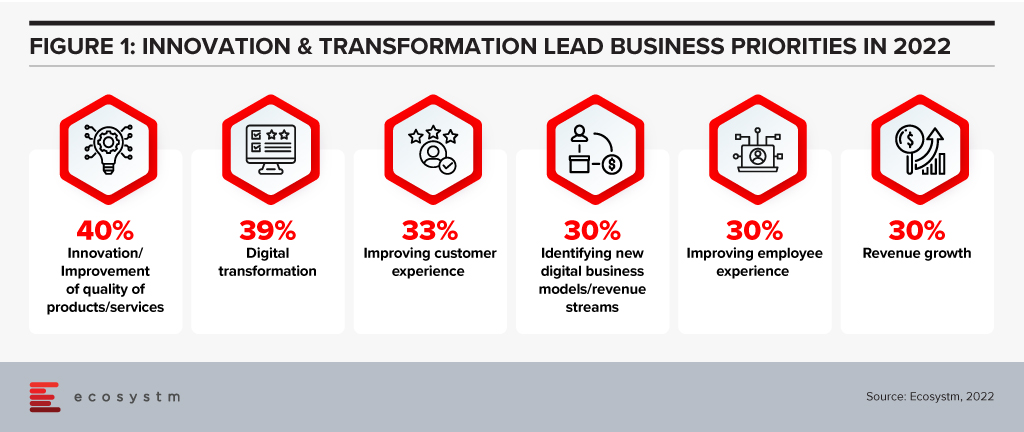
In many respects, the fact that the digital disruptors got SO far ahead is an indication of just how slow the rest of the market was to respond, and a credit to the significant investments these innovators made to get ahead. But now that the rest of the market is catching up shows that there is no secret sauce when it comes to innovation. What Uber, Tesla, Amazon and every other digital innovator has done is replicable. Your business just needs to make the necessary changes to give you the ability to catch up to the digital innovators in your industry – do it well and you will even keep up with them or get ahead. And innovation is the leading business priority for most organisations today!
What all of the digital disruptors did fifteen years ago, and many other businesses have done since then, is develop the ability to create and improve digital customer experiences at pace. Nearly every customer experience is digital – at least in part. So creating great digital experiences will go a long way to creating great customer experiences. Sounds easy right?
However, what this actually means is they changed their culture, structure, KPIs, technology, skills and the nature of their business. Many organisations have beaten the path to becoming digital businesses – in fact, it is a well-worn path. When you set off on the journey you are no longer taking risks or heading out alone. There is a very clear playbook as to how to become a digital business today.
What Does a Digital Business Look Like?
If you are part of your organisation’s tech team and wondering how digital your business is, ask these questions:
- Do you mainly deploy new technology services with the Waterfall project methodology?
- Do all of the development work with the IT team (and not in business or customer teams)?
- Does it take months or years to deploy new services?
- Are your KPIs the same as they were 5-10 years ago?
If the answer to some or all of these questions is YES, then it is likely that you are working for a business that will not catch up with or get ahead of your competitors. You might have a few initiatives that see you make some ground on them – but innovation today is not about leaps and bounds – it is about continual improvement. If you catch up today but don’t have the ability to continually improve, you will have fallen behind again tomorrow…
The good news is it is never too late to start this journey. It typically starts from the top of your business – the CIO cannot make the entire business agile. The head of the digital cannot change the culture of the entire organisation. But the IT and digital teams can get the ball rolling by changing their structure and work processes. Start by moving some developers into the Customer Experience team (if you have one!). Stop funding projects and start funding squads, tribes and teams. Structure the team around the customer journey – or at least make it easier for customers to get value from the digital assets and services you offer. Hopefully, someone will notice the fact that the tech team is helping a business unit or team to operate with agility and they’ll start asking why they cannot have that same ability?
And by then the ball is rolling down the hill and you are on your way to being a digital business – and on your way to giving customers the products, services and experiences they demand today and tomorrow.

Ecosystm research finds that 47% of organisations re-evaluated cybersecurity risks and management making it the biggest measure undertaken by IT Teams when COVID-19 hit. There is no denying any more that cybersecurity is a key business enabler. This year witnessed cybercrime escalating in all parts of the world and several governments issued advisories warning enterprises and citizens of the increase in the threat landscape, during and post COVID-19. Against this backdrop, Ecosystm Advisors, Alex Woerndle, Andrew Milroy, Carl Woerndle and Claus Mortensen present the top 5 Ecosystm predictions for Cybersecurity & Compliance in 2021.
This is a summary of the predictions, the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Cybersecurity & Compliance Trends for 2021
- There will be Further Expansion of M&A Activities Through 2021 and Beyond
As predicted last year, the market is set to witness mergers and acquisitions (M&As) to consolidate the market. The pandemic has slowed down M&A activities in 2020. However, the market remains fragmented and there is a demand for consolidation. As the cyber market continues to mature, we expect M&A activities to ramp up over the next couple of years especially once we emerge from COVID-19. Some organisations that understand the full impact of the shift to remote working and the threats it creates have embraced the opportunity to acquire, based on perceived value due to COVID-19. The recent acquisition of Asavie by Akamai Technologies is a case in point. Asavie’s platform is expected to strengthen Akamai’s IoT and mobile device security and management services.
- After a Year of Pandemic Leniency, Regulators will Get Stricter in 2021
The regulators in the EU appear to have gone through a period of relative leniency or less activity during the first few months of the pandemic and have started to increase their efforts after the summer break. Expect regulators – even outside the EU – to step up their enforcement activities in 2021 and seek larger penalties for breaches.
Governments continue to evolve their Compliance policies across broader sectors, which will impact all industries. As an example, in Australia, the Federal Government has made changes to its definition of critical infrastructure, which brings mandates to many more organisations. Governments have shown an acute awareness of the rise in cyber-attacks highlighted by several high-profile breaches reported in mainstream media. Insider threats – highlighted by Tesla, where an employee raised the allegations of bribery by unknown third parties in exchange for exfiltrating corporate information – will also lead regulators to double down on their enforcement activities.
- The Zero Trust Model Will Gain Momentum
Remote working has challenged the traditional network security perimeter model. The use of personal and corporate devices to access the network via public networks and third-party clouds is creating more opportunity for attackers. Organisations have started turning to a Zero Trust security model to mitigate the risk, applying advanced authentication and continuous monitoring. We expect the adoption of the Zero Trust model to gain momentum through 2021. This will also see an increase in managed services around active security monitoring such as Threat Detection & Response and the increased adoption of authentication technologies. With an eye on the future, especially around quantum computing, authentication technologies will need to continually evolve.
- The Endpoint Will be the Weakest Link
The attack surface continues to grow exponentially, with the increase in remote working, IoT devices and multicloud environments. Remote endpoints require the same, if not higher levels of security than assets that sit within corporate firewalls, and it will become very clear to organisations that endpoints are the most vulnerable. Remote workers are often using unsecure home Wi-Fi connections and unpatched VPNs, and are increasingly vulnerable to phishing attacks. IoT device passwords are often so weak that brute-force attackers can enter networks in milliseconds.
Although endpoint security can be dealt with through strict policies together with hardware or software authentication, the difficult part is to adopt an approach that retains a relatively high level of security without having a too negative an impact on the employee experience. Experience shows that if the security measures are too cumbersome, employees will find ways to circumvent them.
- Hackers Will Turn the Table on AI Security
Cybersecurity vendors are increasingly offering solutions that leverage AI to identify and stop cyber-attacks with less human intervention than is typically expected or needed with traditional security approaches. AI can enhance cybersecurity by better predicting attacks enabling more proactive countermeasures, shortening response times, and potentially saving cybersecurity investment costs. The problem is that the exact same thing applies to the hackers. By leveraging AI, the costs and efforts needed to launch and coordinate large hacker attacks will also go down. Hackers can automate their attacks well beyond the use of botnets, target and customise their attacks with more granularity than before and can effectively target the biggest weakness of any IT security system – people.
Already, phishing attacks account for many of the breaches we see today typically by employees being tricked into sharing their IT credentials via email or over the phone. As we move forward, these types of attacks will become much more sophisticated. Many of the deepfake videos we see have been made using cheap or free AI-enabled apps that are easy enough for even a child to use. As we move into 2021, this ability to manipulate both video and audio will increasingly enable attackers to accurately impersonate individuals.