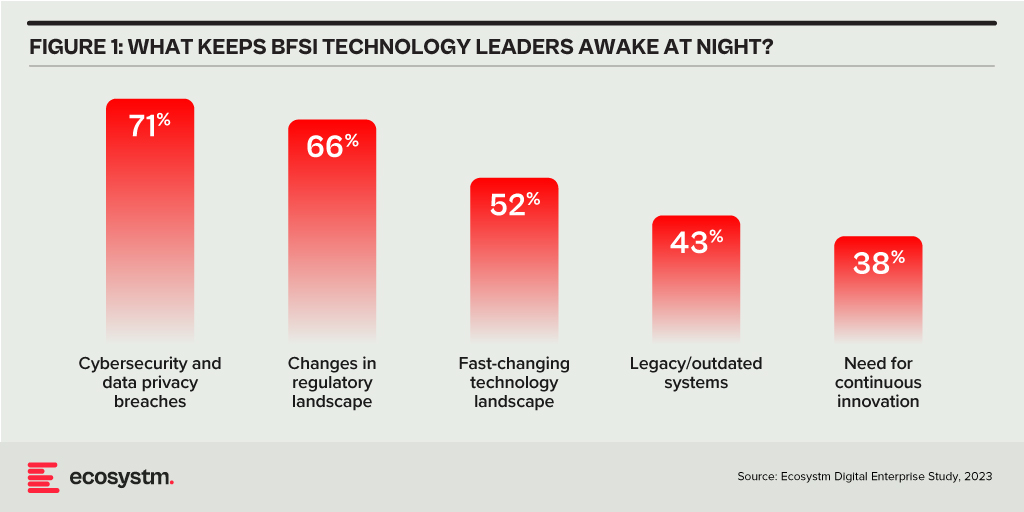
Ecosystm research reveals a stark reality: 75% of technology leaders in Financial Services anticipate data breaches.
Given the sector’s regulatory environment, data breaches carry substantial financial implications, emphasising the critical importance of giving precedence to cybersecurity. This is compelling a fresh cyber strategy focused on early threat detection and reduction of attack impact.
Read on to find out how tech leaders are building a culture of cyber-resilience, re-evaluating their cyber policies, and adopting technologies that keep them one step ahead of their adversaries.
Download ‘Cyber-Resilience in Finance: People, Policy & Technology’ as a PDF

Trust in the Banking, Financial Services, and Insurance (BFSI) industry is critical – and this amplifies the value of stolen data and fuels the motivation of malicious actors. Ransomware attacks continue to escalate, underscoring the need for fortified backup, encryption, and intrusion prevention systems. Similarly, phishing schemes have become increasingly sophisticated, placing a burden on BFSI cyber teams to educate employees, inform customers, deploy multifactor authentication, and implement fraud detection systems. While BFSI organisations work to fortify their defences, intruders continually find new avenues for profit – cyber protection is a high-stakes game of technological cat and mouse!
Some of these challenges inherent to the industry include the rise of cryptojacking – the unauthorised use of a BFSI company’s extensive computational resources for cryptocurrency mining.
Building Trust Amidst Expanding Threat Landscape
BFSI organisations face increasing complexity in their IT landscapes. Amidst initiatives like robo-advisory, point-of-sale lending, and personalised engagements – often facilitated by cloud-based fintech providers – they encounter new intricacies. As guest access extends to bank branches and IoT devices proliferate in public settings, vulnerabilities can emerge unexpectedly. Threats may arise from diverse origins, including misconfigured ATMs, unattended security cameras, or even asset trackers. Ensuring security and maintaining customer trust requires BFSI organisations to deploy automated and intelligent security systems to respond to emerging new threats.
Ecosystm research finds that nearly 70% of BFSI organisations have the intention of adopting AI and automation for security operations, over the next two years. But the reality is that adoption is still fairly nascent. Their top cyber focus areas remain data security, risk and compliance management, and application security.
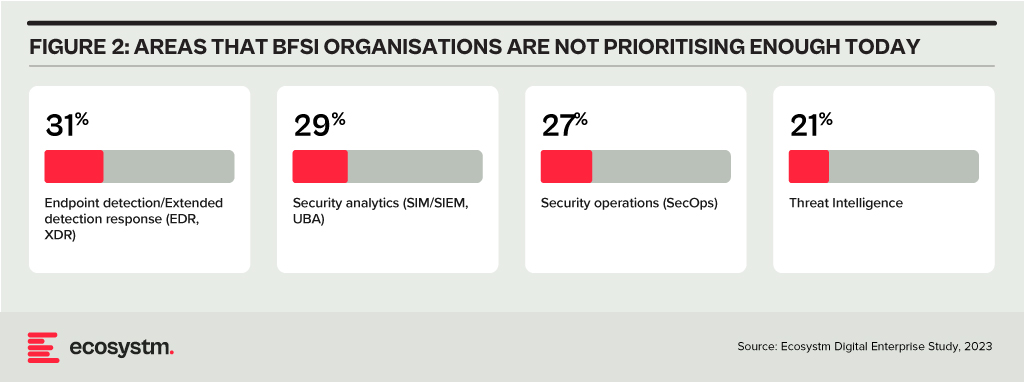
Addressing Alert Fatigue and Control Challenges
According to Ecosystm research, 50% of BFSI organisations use more than 50 security tools to secure their infrastructure – and these are only the known tools. Cyber leaders are not only challenged with finding, assessing, and deploying the right tools, they are also challenged with managing them. Management challenges include a lack of centralised control across assets and applications and handling a high volume of security events and false positives.
Software updates and patches within the IT environment are crucial for security operations to identify and address potential vulnerabilities. Management of the IT environment should be paired with greater automation – event correlation, patching, and access management can all be improved through reduced manual processes.
Security operations teams must contend with the thousands of alerts that they receive each day. As a result, security analysts suffer from alert fatigue and struggle to recognise critical issues and novel threats. There is an urgency to deploy solutions that can help to reduce noise. For many organisations, an AI-augmented security team could de-prioritise 90% of alerts and focus on genuine risks.
Taken a step further, tools like AIOps can not only prioritise alerts but also respond to them. Directing issues to the appropriate people, recommending actions that can be taken by operators directly in a collaboration tool, and rules-based workflows performed automatically are already possible. Additionally, by evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where security operations are completely automated.
Threat Intelligence and Visibility for a Proactive Cyber Approach
New forms of ransomware, phishing schemes, and unidentified vulnerabilities in cloud are emerging to exploit the growing attack surface of financial services organisations. Security operations teams in the BFSI sector spend most of their resources dealing with incoming alerts, leaving them with little time to proactively investigate new threats. It is evident that organisations require a partner that has the scale to maintain a data lake of threats identified by a broad range of customers even within the same industry. For greater predictive capabilities, threat intelligence should be based on research carried out on the dark web to improve situational awareness. These insights can help security operations teams to prepare for future attacks. Regular reporting to keep CIOs and CISOs informed of the changing threat landscape can also ease the mind of executives.
To ensure services can be delivered securely, BFSI organisations require additional visibility of traffic on their networks. The ability to not only inspect traffic as it passes through the firewall but to see activity within the network is critical in these increasingly complex environments. Network traffic anomaly detection uses machine learning to recognise typical traffic patterns and generates alerts for abnormal activity, such as privilege escalation or container escape. The growing acceptance of BYOD has also made device visibility more complex. By employing AI and adopting a zero-trust approach, devices can be profiled and granted appropriate access automatically. Network operators gain visibility of unknown devices and can easily enforce policies on a segmented network.
Intelligent Cyber Strategies
Here is what BFSI CISOs should prioritise to build a cyber resilient organisation.
Automation. The volume of incoming threats has grown beyond the capability of human operators to investigate manually. Increase the level of automation in your SOC to minimise the routine burden on the security operations team and allow them to focus on high-risk threats.
Cyberattack simulation exercises. Many security teams are too busy dealing with day-to-day operations to perform simulation exercises. However, they are a vital component of response planning. Organisation-wide exercises – that include security, IT operations, and communications teams – should be conducted regularly.
An AIOps topology map. Identify where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of threats, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
A trusted intelligence partner. Extend your security operations team by working with a partner that can provide threat intelligence unattainable to most individual organisations. Threat intelligence providers can pool insights gathered from a diversity of client engagements and dedicated researchers. By leveraging the experience of a partner, BFSI organisations can better plan for how they will respond to inevitable breaches.
Conclusion
An effective cybersecurity strategy demands a comprehensive approach that incorporates technology, education, and policies while nurturing a culture of security awareness throughout the organisation. CISOs face the daunting task of safeguarding their organisations against relentless cyber intrusion attempts by cybercriminals, who often leverage cutting-edge automated intrusion technologies.
To maintain an advantage over these threats, cybersecurity teams must have access to continuous threat intelligence; automation will be essential in addressing the shortage of security expertise and managing the overwhelming volume and frequency of security events. Collaborating with a specialised partner possessing both scale and experience is often the answer for organisations that want to augment their cybersecurity teams with intelligent, automated agents capable of swiftly

A lot gets written about cybersecurity – and organisations spend a lot on it! Ecosystm research finds that 63% of organisations across Asia Pacific are planning to increase their cyber budget for the next year. As budgets continue to rise, the threat landscape continues to get more complex and difficult to navigate. Despite increasing spend, 69% of organisations believe a breach is inevitable. And breaches can be EXPENSIVE! Medibank, in Australia, was breached in (or around) October, 2022. The cost of the breach is expected to reach around USD 52 million when everything is done and dusted – and this does not include the impacts of any potential findings or outcomes from regulatory investigations or litigation.
Recovering Strong
While cybersecurity is still crucially important, the ability to recover from breaches quickly and cost-effectively is also imperative. How you recover from a breach will ultimately determine your organisation’s long-term viability and success. The capabilities needed to recover quickly include:
- A well-documented and practices incident response plan. The plan should outline the roles and responsibilities of all team members, communication protocols, and steps to be taken in the event of a breach.
- Backup and Disaster Recovery (DR) solutions. Regular backups of critical data and systems are essential to quickly recover from a breach. Backup solutions should include offsite or cloud-based options that are isolated from the main network. DR solutions ensure that critical systems can be quickly restored and made operational after a breach.
- Cybersecurity awareness training. Investing in regular training for all employees is crucial to ensure they are aware of the latest threats and know how to respond in the event of a breach.
- Automated response tools. Automation can help speed up the response time during a breach by automatically blocking malicious IPs, quarantining infected devices, or taking other predefined actions based on the nature of the attack.
- Threat intelligence. This can help organisations stay ahead of the latest threats and vulnerabilities and frame quicker responses if a breach occurs.
Backup and Disaster Recovery is Evolving
Most organisations already have backup and disaster recovery capabilities in place – but too often they are older systems, designed more as a “just in case” versus a “will keep us in business” capability. Backup and DR systems are evolving and improving – and with the increased likelihood of a breach, it is a good time to consider what a modern Backup and DR system can provide to your organisation. Here are some of the key trends and considerations that technology leaders should be aware of:
- Cloud-based solutions. More organisations are moving towards cloud-based backup and DR solutions. Cloud solutions offer several advantages, including scalability, cost-effectiveness, and the ability to access data and systems from anywhere. However, technology leaders need to consider data security, compliance requirements, and the reliability of the cloud service provider.
- Hybrid options. As hybrid cloud becomes the norm for most organisations, hybrid solutions backup and DR that combine on-premises and cloud-based backups are becoming more popular. This approach provides the best of both worlds – the security and control of on-premises backups with the scalability and flexibility of the cloud.
- Increased use of automation. Automation is becoming more prevalent in backup and DR solutions. Automation helps reduce the time it takes to backup data, restore systems, and test DR plans. It also minimises the risk of human error. Technology leaders should look for solutions that offer automation capabilities while also allowing for manual intervention when necessary.
- Cybersecurity integration. With the rise of cyberattacks, especially ransomware, it is crucial that backup and DR solutions are integrated with an organisation’s cybersecurity strategy. Backup data should be encrypted and isolated from the main network to prevent attackers from accessing or corrupting it. Regular testing of backup and DR plans should also include scenarios where a cyberattack, such as ransomware, is involved.
- More frequent backups. Data is becoming more critical to business operations, so there is a trend towards more frequent backups, even continuous backups, to minimise data loss in the event of a disaster. Technology leaders need to balance the need for frequent backups with the cost and complexity involved.
- Super-fast data recovery. Some data recovery platforms can recover data FAST – in as little as 6 seconds. The ability to recover data faster than the bad actors can delete it makes organisations less vulnerable and buys more time to plug the gaps that the attackers are exploiting to gain access to data and systems.
- Monitoring and analytics. Modern backup and DR solutions offer advanced monitoring and analytics capabilities. This allows organisations to track the performance of their backups, identify potential issues before they become critical, and optimise their backup and DR processes. Technology leaders should look for solutions that offer comprehensive monitoring and analytics capabilities.
- Compliance considerations. With the increasing focus on data privacy and protection, organisations need to ensure that backup and DR solutions are compliant with relevant regulations, often dictated at the industry level in each geography. Technology leaders should work with their legal and compliance teams to ensure that their backup and DR solutions meet all necessary requirements.
The sooner you evolve and modernise your backup and disaster recovery capabilities, the more breathing room your cybersecurity team has, to improve the ability to repel threats. New security architectures and postures – such as Zero Trust and SASE are emerging as better ways to build your cybersecurity capabilities – but they won’t happen overnight and require significant investment, training, and business change to implement.

Last week AT&T announced a partnership with Fortinet to expand their managed security services portfolio. This partnership provides global managed Secure Access Service Edge (SASE) solutions at scale. The solution uses Fortinet’s SASE stack which unifies software-defined wide-area network (SD-WAN) and network security capabilities into AT&T managed cybersecurity framework. Additionally, AT&T SASE and Fortinet will integrate with AT&T Alien Labs Threat Intelligence platform, a threat intelligence unit to enhance detection and response. AT&T has plans to update its managed SASE service during the year and will continue to bring more options.
Talking about the AT&T-Fortinet partnership, Ecosystm Principal Advisor, Ashok Kumar says, “This move continues the trend of the convergence of networking and security solutions. AT&T is positioning themselves well with their integrated offer of network and security services to address the needs of global enterprises.”
Convergence of Network & Security
AT&T’s improved global managed security service includes features such as secure web gateway, firewall-as-a service, cloud access security broker (CASB) and zero-trust access, which provides security teams and analysts with unified capabilities across the cloud, networks and endpoints. The solution aims to enable enterprises to create a more resilient network bringing the core capabilities of the two companies that will reduce operational costs and deliver a unified offering.
Last year AT&T also partnered with Cisco to expand its SD-WAN solution and to support AT&T Managed Services using Cisco’s vManage controller through a single management interface. Over the past years multiple vendors including Fortinet have developed comprehensive SASE solution capabilities through partnerships or acquisitions to provide a unified offering. Last year Fortinet acquired Opaq, a SASE cloud provider to bolster their security capabilities through OPAQ’s patented Zero Trust Network Access (ZTNA) cloud solution and to strengthen SD-WAN, security and edge package.
The Push Towards Flexible Networking
Kumar says, “The pandemic has created a higher demand and value for secure networking services. Enterprises experienced greater number of phishing and malware attacks last year with the sudden increase in work-from-home users. The big question enterprises need to ask themselves is whether legacy networks can support their evolving business priorities.”
“As global economies look to recover, securing remote users working from anywhere, with full mobility, will be a high priority for all enterprises. Enterprises need to evaluate mobile SASE services that provide frictionless identity management with seamless user experiences, and be compatible with the growing adoption of 5G services in 2021 and beyond.”
The Top 5 Telecommunications & Mobility Trends that will dominate the telecom industry to watch out for in 2021. Signup for Free to download the report.

Ecosystm research finds that 47% of organisations re-evaluated cybersecurity risks and management making it the biggest measure undertaken by IT Teams when COVID-19 hit. There is no denying any more that cybersecurity is a key business enabler. This year witnessed cybercrime escalating in all parts of the world and several governments issued advisories warning enterprises and citizens of the increase in the threat landscape, during and post COVID-19. Against this backdrop, Ecosystm Advisors, Alex Woerndle, Andrew Milroy, Carl Woerndle and Claus Mortensen present the top 5 Ecosystm predictions for Cybersecurity & Compliance in 2021.
This is a summary of the predictions, the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Cybersecurity & Compliance Trends for 2021
- There will be Further Expansion of M&A Activities Through 2021 and Beyond
As predicted last year, the market is set to witness mergers and acquisitions (M&As) to consolidate the market. The pandemic has slowed down M&A activities in 2020. However, the market remains fragmented and there is a demand for consolidation. As the cyber market continues to mature, we expect M&A activities to ramp up over the next couple of years especially once we emerge from COVID-19. Some organisations that understand the full impact of the shift to remote working and the threats it creates have embraced the opportunity to acquire, based on perceived value due to COVID-19. The recent acquisition of Asavie by Akamai Technologies is a case in point. Asavie’s platform is expected to strengthen Akamai’s IoT and mobile device security and management services.
- After a Year of Pandemic Leniency, Regulators will Get Stricter in 2021
The regulators in the EU appear to have gone through a period of relative leniency or less activity during the first few months of the pandemic and have started to increase their efforts after the summer break. Expect regulators – even outside the EU – to step up their enforcement activities in 2021 and seek larger penalties for breaches.
Governments continue to evolve their Compliance policies across broader sectors, which will impact all industries. As an example, in Australia, the Federal Government has made changes to its definition of critical infrastructure, which brings mandates to many more organisations. Governments have shown an acute awareness of the rise in cyber-attacks highlighted by several high-profile breaches reported in mainstream media. Insider threats – highlighted by Tesla, where an employee raised the allegations of bribery by unknown third parties in exchange for exfiltrating corporate information – will also lead regulators to double down on their enforcement activities.
- The Zero Trust Model Will Gain Momentum
Remote working has challenged the traditional network security perimeter model. The use of personal and corporate devices to access the network via public networks and third-party clouds is creating more opportunity for attackers. Organisations have started turning to a Zero Trust security model to mitigate the risk, applying advanced authentication and continuous monitoring. We expect the adoption of the Zero Trust model to gain momentum through 2021. This will also see an increase in managed services around active security monitoring such as Threat Detection & Response and the increased adoption of authentication technologies. With an eye on the future, especially around quantum computing, authentication technologies will need to continually evolve.
- The Endpoint Will be the Weakest Link
The attack surface continues to grow exponentially, with the increase in remote working, IoT devices and multicloud environments. Remote endpoints require the same, if not higher levels of security than assets that sit within corporate firewalls, and it will become very clear to organisations that endpoints are the most vulnerable. Remote workers are often using unsecure home Wi-Fi connections and unpatched VPNs, and are increasingly vulnerable to phishing attacks. IoT device passwords are often so weak that brute-force attackers can enter networks in milliseconds.
Although endpoint security can be dealt with through strict policies together with hardware or software authentication, the difficult part is to adopt an approach that retains a relatively high level of security without having a too negative an impact on the employee experience. Experience shows that if the security measures are too cumbersome, employees will find ways to circumvent them.
- Hackers Will Turn the Table on AI Security
Cybersecurity vendors are increasingly offering solutions that leverage AI to identify and stop cyber-attacks with less human intervention than is typically expected or needed with traditional security approaches. AI can enhance cybersecurity by better predicting attacks enabling more proactive countermeasures, shortening response times, and potentially saving cybersecurity investment costs. The problem is that the exact same thing applies to the hackers. By leveraging AI, the costs and efforts needed to launch and coordinate large hacker attacks will also go down. Hackers can automate their attacks well beyond the use of botnets, target and customise their attacks with more granularity than before and can effectively target the biggest weakness of any IT security system – people.
Already, phishing attacks account for many of the breaches we see today typically by employees being tricked into sharing their IT credentials via email or over the phone. As we move forward, these types of attacks will become much more sophisticated. Many of the deepfake videos we see have been made using cheap or free AI-enabled apps that are easy enough for even a child to use. As we move into 2021, this ability to manipulate both video and audio will increasingly enable attackers to accurately impersonate individuals.

In recent times, there appears to be a shift in motive for cyber-attacks – along with common data theft, there is a proliferation of attacks aimed at the business interruption and physical incapacitation of business operations. We have witnessed an alarming increase in high-profile attacks on manufacturing businesses and critical infrastructure providers, globally.
This appears to be a global phenomenon. Honda manufacturing plants went offline in June after a cyber-attack compromised some of the Japanese automaker’s facilities. The same pattern emerged in a separate attack at the same time targeting Edesur S.A., a company belonging to the Enel Group that confirmed its internal IT network was disrupted due to a ransomware attack, which was caught by antivirus software before the malware could infect. Both companies had machines with Internet-accessible remote desktop servers, which is a favorite infection method among attackers nowadays. One of Australia’s largest brewers, Lion also faced a ransomware outbreak, last month. In Israel, it was reported that a cyber-attack very nearly poisoned the water supply with the attackers attempting to overload the water system with chlorine, and in recent days, a fire and explosion at an Iranian nuclear plant is suspected of being caused by cyber-attack.
These attacks highlight the need for appropriate investments in cybersecurity by companies and municipalities that own or operate critical infrastructure, properties (including places of public congregation, retailers and others) that are rapidly deploying a suite of operational technologies, and businesses in the manufacturing sector.
Operational Technology (OT) is the backbone of modern industrial operations and is a network of multiple computing systems that perform operations including production line management, operations control and industrial monitoring. OT can further include specific computing systems like industrial control systems (ICS) which is a collection of control systems used to operate and/or automate industrial processes. There are several types of ICSs, the most common of which are Supervisory Control and Data Acquisition (SCADA) systems, and Distributed Control Systems (DCS). With such industrial systems and smart end-user products connected by a common network, several vulnerabilities may appear.
In OT security, the focus is much less on information, but more on the industrial process that technology controls. Hence, availability and integrity are often more important than confidentiality. Any organisation employing OT should employ continual risk-based assessments of their cybersecurity posture to prioritise and tailor recommended guidelines and solutions to fit specific security, business, and operational requirements.
Why is OT More Vulnerable?
OT systems are versatile and can be found in all kinds of industrial settings and infrastructures like smart buildings, oil and gas, energy generation/distribution, mining, wastewater treatment/distribution, manufacturing, food production, consumer devices and transport. In fact, almost every business in 2020 has an element of IoT within their operations.
A big issue with OT is that a lot of the technology in place is over 20 years old and therefore was not designed to provide the security capabilities required to face cyber threats in 2020. Legacy technology often requires legacy hardware and software to support it – much of which is the end of life and unsupported by the vendors (for example, consider SCADA systems still reliant on Windows NT or older Unix based systems, which have not been supported by their vendors for many years).
OT systems have also been damaged as unintended side effects of problems starting in corporate networks that took advantage of increasing connectivity, proving clearly that the standard PCs that now form part of a typical organisation’s IT environment are in turn used to manage OT systems and become a major vector for such cyber-attacks.
When it comes to OT, safety and reliability are the primary concerns as attackers aim to disrupt the critical services industry and their customers rely upon them. Given the increasing propensity of connecting OT systems with corporate networks for ease of management and the growing use of IoT systems, the likelihood of such systems being affected by vulnerabilities exploitable over the network is increasing exponentially.
For almost every business – not just critical infrastructure providers – most technologies we deploy include connectivity to the internet. Not knowing what systems and external access to these systems that your business is introducing in its everyday technology investment create significant risks to the broader business operations.
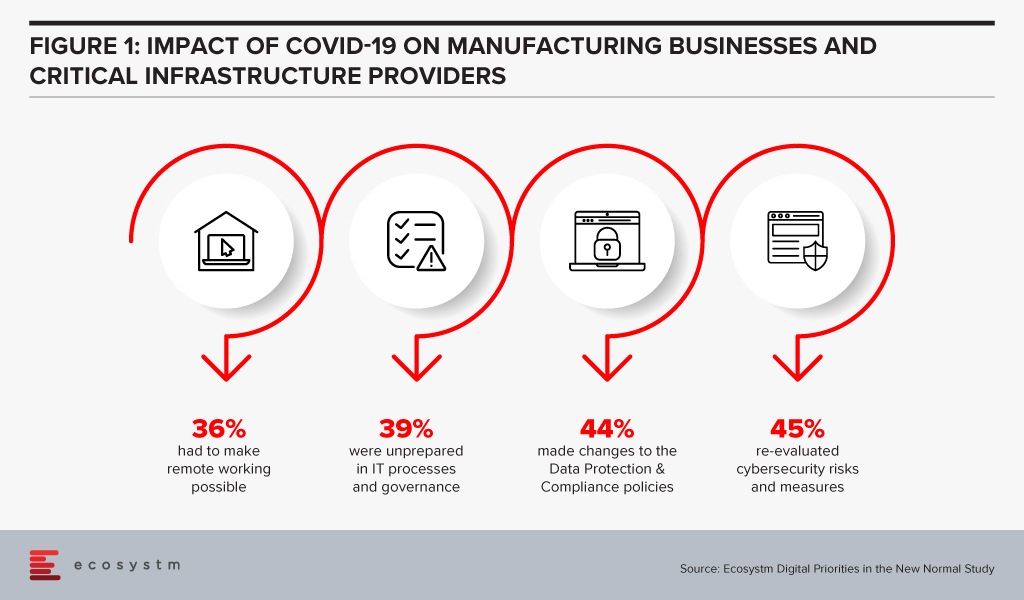
Manufacturing businesses and critical infrastructure providers realise that there is need to re-evaluate their cybersecurity measures, in the wake of the COVID-19 crisis, according to the findings of the Ecosystm’s ongoing “Digital Priorities in the New Normal” study (Figure 1).
But these measures may not be sufficient, as indicated by the slew of cyber-attacks on these organisations.
Why are these attacks successful?
There are several reasons why OT attacks are successful:
- Unauthorised access to internet-facing systems (e.g. deploying an IoT with the default username and password)
- Introduction of a compromised device (e.g. USB stick) to the environment that infects the network (often employee action)
- Exploitation of zero-day vulnerabilities in control devices and software
- Propagated malware infections within isolated computer networks (i.e. The attacker can place a receiving device to make contact over a channel that can propagate across the isolated network)
- SQL injection via exploitation of web application vulnerabilities
- Network scanning and probing
- Lateral movement (i.e. inadequate segmentation which results in attackers being able to move between systems, groups of systems, network zones and even geographical locations.)
How can they be prevented?
The mitigation cannot rely solely on the organisation building security around the deployment nor can it be a reactive approach to fixing vulnerabilities in production, as they are identified. It begins with the OT vendors building security within; however, as with most IT systems and applications, this will evolve over time. For example, there is an initiative in Australia – driven by the IoT Alliance Australia (IOTAA) – to introduce a ‘Trust Mark’ for IoT devices that pass a certification process for security and privacy in product development. This is targeted to launch in September 2020 but could take many years to gain real traction. Thus, for the foreseeable future, the best operational outcomes must be planned and managed by the consumers of the technologies.
Here are the best practices to reduce exploitable IoT weaknesses and attacks occurring in your business:
- Maintain an accurate inventory of Operational Systems and eliminate any exposure of these systems to external networks
- Establish clear roles and responsibilities for your organisation and your vendors, to ensure cybersecurity risk is being addressed and managed throughout the OT lifecycle
- Implement network segmentation and apply firewalls between critical networks and systems.
- Use secure remote access methods
- Establish Role-Based Access Controls (RBAC) and implement system logging
- Use only strong passwords, change default passwords, and consider other access controls (especially for any elevated privileges) such as multi-factor authentication, privileged access management solutions, etc.
- Establish threat intelligence feeds from your OT vendors and security vendors to ensure you remain abreast of new vulnerabilities, software/firmware patches and threats targeting systems you employ
- Develop and enforce policies on mobile devices, including strict device controls for any device connecting to OT systems or network zones
- Implement an employee cybersecurity training program
- Establish and maintain rigorous testing and patching program including vulnerability assessment and penetration testing
- Implement measures for detecting compromises and develop a cybersecurity incident response plan with a specific focus on responding to a disruptive attack on your OT environment
- Maintain an up-to-date Business Continuity Plan that can be deployed rapidly in response to a significant disruption

Last week, the Australia Government announced that they have been monitoring persistent and increasing volumes of cyber-attacks by a foreign state-based actor on both government and private sector businesses. The Australian Cyber Security Centre (ACSC) reported that most of the attacks make use of existing open-source tools and packages, which ACSC has dubbed as “copy-paste compromises”. The attackers are also using other methods to exploit such as spear phishing, sending malicious files and using various websites to harvest passwords and more, to exploit systems.
Cybercrime has been escalating in other parts of the world as well. The World Health Organisation (WHO) witnessed a dramatic increase in cyber-attacks directed with scammers impersonating WHO personnel’s official emails targeting the public. The National Cyber Security Centre (NCSC) in the UK alerted the country’s educational institutions and scientific facilities on increased cyber-attacks attempting to steal research associated with the coronavirus. Earlier this month, the Singapore Computer Emergency Response Team (SingCERT) issued an advisory on potential phishing campaigns targeting six countries, including Singapore that exploit government support initiatives for businesses and individuals in the wake of the COVID-19 crisis.
Such announcements are a timely reminder to government agencies and private organisations to implement the right cybersecurity measures against the backdrop of an increased attack surface. These cyber attacks can have business impacts such as theft of business data and destruction or impairment to financial data, creating extended business interruptions. The ramifications can be far-reaching including financial and reputational loss, compliance breaches and potentially even legal action.
A Rise in Spear-Phishing
In Australia, we’re seeing attackers targeting internet-facing infrastructure relating to vulnerabilities in Citrix, Windows IIS web server, Microsoft Sharepoint, and Telerik UI.
Where these attacks fail, they are moving to spear-phishing attacks. Spear phishing is most commonly an email or SMS scam targeted towards a specific individual or organisation but can be delivered to a target via any number of electronic communication mediums. In the spear-phishing emails, the attacker attaches files or includes links to a variety of destinations that include:
- Credential harvesting sites. These genuine-looking but fake web sites prompt targets to enter username and password. Once the gullible target provides the credentials, these are then stored in the attackers’ database and are used to launch credential-based attacks against the organisation’s IT infrastructure and applications.
- Malicious files. These file attachments to emails look legitimate but once downloaded, they execute a malicious malware on the target device. Common file types are .doc, .docx, .xls, .xlsx, .ppt, .pptx, .jpg, .jpeg, .gif, .mpg, .mp4, .wav
- OAuth Token Theft. OAuth is commonly used on the internet to authenticate a user to a wide variety of other platforms. This attack technique uses OAuth tokens generated by a platform and shares with other platforms. An example of this is a website that asks users to authenticate using their Facebook or Google accounts in order to use its own services. Faulty implementation of OAuth renders such integration to cyber-attacks.
- Link Shimming. The technique includes using email tracking services to launch an attack. The attackers send fake emails with valid looking links and images inside, using email tracking services. Once the user receives the email, it tracks the actions related to opening the email and clicking on the links. Such tracking services can reveal when the email was opened, location data, device used, links clicked, and IP addresses used. The links once clicked-on, can in- turn, lead to malicious software being stealthily downloaded on the target system and/or luring the user for credential harvesting.
How do you safeguard against Cyber-Attacks?
The most common vectors for such cyber-attacks are lack of user awareness AND/OR exploitable internet-facing systems and applications. Unpatched or out-of-support internet-facing systems, application or system misconfiguration, inadequate or poorly maintained device security controls and weak threat detection and response programs, compound the threat to your organisation.
Governments across the world are coming up with advisories and guidelines to spread cybersecurity awareness and prevent threats and attacks. ACSC’s Australian Signals Directorates ‘Essential 8’ are effective mitigations for a large majority of present-day attacks. There were also guidelines published earlier this year, specifically with the COVID-19 crisis in mind. The Cyber Security Agency in Singapore (CSA) promotes the ‘Go Safe Online’ campaign that provides regular guidance and best practices on cybersecurity measures.
Ecosystm’s ongoing “Digital Priorities in the New Normal” study evaluates the impact of the COVID-19 pandemic on organisations, and how digital priorities are being initiated or aligned to adapt to the New Normal that has emerged. 41% of organisations in Asia Pacific re-evaluated cybersecurity risks and measures, in the wake of the pandemic. Identity & Access Management (IDAM), Data Security and Threat Analytics & Intelligence saw increased investments in many organisations in the region (Figure 1).
However, technology implementation has to be backed by a rigorous process that constantly evaluates the organisation’s risk positions. The following preventive measures will help you address the risks to your organisation:
- Conduct regular user awareness training on common cyber threats
- Conduct regular phishing tests to check user awareness level
- Patch the internet-facing products as recommended by their vendors
- Establish baseline security standards for applications and systems
- Apply multi-factor authentication to access critical applications and systems – especially internet-facing and SaaS products widely used in the organisation like O365
- Follow regular vulnerability scanning and remediation regimes
- Conduct regular penetration testing on internet-facing applications and systems
- Apply security settings on endpoints and internet gateways that disallow download and execution of files from unfamiliar sources
- Maintain an active threat detection and response program that provides for intrusion detection, integrity checks, user and system behaviour monitoring and tools to maintain visibility of potential attacks and incidents – e.g Security Information & Event Monitoring (SIEM) tools
- Consider managed services such as Managed Threat Detection and Response delivered via security operations (SOC)
- Maintain a robust incident management program that is reviewed and tested at least annually
- Maintain a comprehensive backup regime – especially for critical data – including offsite/offline backups, and regular testing of backups for data integrity
- Restrict and monitor the usage of administrative credentials

In his blog, The Cybercrime Pandemic, Ecosystm Principal Advisor, Andrew Milroy says, “Remote working has reached unprecedented levels as organisations try hard to keep going. This is massively expanding the attack surface for cybercriminals, weakening security and leading to a cybercrime pandemic. Hacking activity and phishing, inspired by the COVID-19 crisis, are growing rapidly.” Remote working has seen an increase in adoption of cloud applications and collaborative tools, and organisations and governments are having to re-think their risk management programs.
We are seeing the market respond to this need and May saw initiatives from governments and enterprises on strengthening risk management practices and standards. Tech vendors have also stepped up their game, strengthening their Cybersecurity offerings.
Market Consolidation through M&As Continues
The Cybersecurity market is extremely fragmented and is ripe for consolidation. The last couple of years has seen some consolidation of the market, especially through acquisitions by larger platform players (wishing to provide an end-to-end solution) and private equity firms (who have a better view of the Cybersecurity start-up ecosystem). Cybersecurity providers continue to acquire niche providers to strengthen their end-to-end offering and respond to market requirements.
As organisations cope with remote working, network security, threat identification and identity and access management are becoming important. CyberArk acquired Identity as a Service provider Idaptive to work on an AI-based identity solution. The acquisition expands its identity management offerings across hybrid and multi-cloud environments. Quick Heal invested in Singapore-based Ray, a start-up specialising in next-gen wireless and network technology. This would benefit Quick Heal in building a safe, secure, and seamless digital experience for users. This investment also shows Quick Heal’s strategy of investing in disruptive technologies to maintain its market presence and to develop a full-fledged integrated solution beneficial for its users.
Another interesting deal was Venafi acquiring Jetstack. Jetstack’s open-source Kubernetes certificate manager controller – cert-manager – with a thriving developer community of over 200 contributors, has been used by many global organisations as the go-to tool for using certificates in the Kubernetes space. The community has provided feedback through design discussion, user experience reports, code and documentation contributions as well as serving as a source for free community support. The partnership will see Venafi’s Machine Identity Protection having cloud-native capabilities. The deal came a day after VMware announced its intent to acquire Octarine to extend VMware’s Intrinsic Security Capabilities for Containers and Kubernetes and integrate Octarine’s technology to VMware’s Carbon Black, a security company which VMware bought last year.
Cybersecurity vendors are not the only ones that are acquiring niche Cybersecurity providers. In the wake of a rapid increase in user base and a surge in traffic, that exposed it to cyber-attacks (including the ‘zoombombing’ incidents), Zoom acquired secure messaging service Keybase, a secure messaging and file-sharing service to enhance their security and to build end-to-end encryption capability to strengthen their overall security posture.
Governments actively working on their Cyber Standards
Governments are forging ahead with digital transformation, providing better citizen services and better protection of citizen data. This has been especially important in the way they have had to manage the COVID-19 crisis – introducing restrictions fast, keeping citizens in the loop and often accessing citizens’ health and location data to contain the disaster. Various security guidelines and initiatives were announced by governments across the globe, to ensure that citizen data was being managed and used securely and to instil trust in citizens so that they would be willing to share their data.
Singapore, following its Smart Nation initiative, introduced a set of enhanced data security measures for public sector. There have been a few high-profile data breaches (especially in the public healthcare sector) in the last couple of years and the Government rolled out a common security framework for public agencies and their officials making them all accountable to a common code of practice. Measures include clarifying the roles and responsibilities of public officers involved in managing data security, and mandating that top public sector leadership be accountable for creating a strong organisational data security regime. The Government has also empowered citizens to raise a flag against unauthorised data disclosures through a simple incident report form available on Singapore’s Smart Nation Website.
Australia is also ramping up measures to protect the public sector and the country’s data against threats and breaches by issuing guidelines to Australia’s critical infrastructure providers from cyber-attacks. The Australian Cyber Security Centre (ACSC) especially aims key employees working in services such as power and water distribution networks, and transport and communications grids. In the US agencies such as the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Energy (DOE) have issued guidelines on safeguarding the country’s critical infrastructure. Similarly, UK’s National Cyber Security Centre (NCSC) issued cybersecurity best practices for Industrial Control Systems (ICS).
Cyber Awareness emerges as the need of the hour
While governments will continue to strengthen their Cybersecurity standards, the truth is Cybersecurity breaches often happen because of employee actions – sometimes deliberate, but often out of unawareness of the risks. As remote working becomes a norm for more organisations, there is a need for greater awareness amongst employees and Cybersecurity caution should become part of the organisational culture.
Comtech received a US$8.4 million in additional orders from the US Federal Government for a Joint Cyber Analysis Course. The company has been providing cyber-training to government agencies in the communications sector. Another public-private partnership to raise awareness on Cybersecurity announced in May was the MoU between Europol’s European Cybercrime Centre (EC3) and Capgemini Netherlands. With this MoU, Capgemini and Europol are collaborating on activities such as the development of cyber simulation exercises, capacity building, and prevention and awareness campaigns. They are also partnered on a No More Ransomware project by National High Tech Crime Unit of the Netherlands’ Police, Kaspersky and McAfee to help victims fight against ransomware threats.
The Industry continues to gear up for the Future
Technology providers, including Cybersecurity vendors, continue to evolve their offerings and several innovations were reported in May. Futuristic initiatives such as these show that technology vendors are aware of the acute need to build AI-based cyber solutions to stay ahead of cybercriminals.
Samsung introduced a new secure element (SE) Cybersecurity chip to protect mobile devices against security threats. The chip received an Evaluation Assurance Level (EAL) 6+ certification from CC EAL – a technology security evaluation agency which certifies IT products security on a scale of EAL0 to EAL7. Further applications of the chip could include securing e-passports, crypto hardware wallets and mobile devices based on standalone hardware-level security. Samsung also introduced a new smartphone in which Samsung is using a chipset from SK Telecom with quantum-crypto technology. This involves Quantum Random Number Generator (QRNG) to enhance the security of applications and services instead of using normal random number generators. The technology uses LED and CMOS sensor to capture quantum randomness and produce unpredictable strings and patterns which are difficult to hack. This is in line with what we are seeing in the findings of an Ecosystm business pulse study to gauge how organisations are prioritising their IT investments to adapt to the New Normal. 36% of organisations in the Asia Pacific region invested significantly in Mobile Security is a response to the COVID-19 crisis.
The same study reveals that nearly 40% of organisations in the region have also increased investments in Threat Analysis & Intelligence. At the Southern Methodist University in Texas, engineers at Darwin Deason Institute for Cybersecurity have created a software to detect and prevent ransomware threats before they can occur. Their detection method known as sensor-based ransomware detection can even spot new ransomware attacks and terminates the encryption process without relying on the signature of past infections. The university has filed a patent for this technique with the US Patent and Trademark Office.
Microsoft and Intel are working on a project called STAMINA (static malware-as-image network analysis). The project involves a new deep learning approach that converts malware into grayscale images to scan the text and structural patterns specific to malware. This works by converting a file’s binary form into a stream of raw pixel data (1D) which is later converted into a photo (2D) to feed into image analysis algorithms based on a pre-trained deep neural network to scan and classify images as clean or infected.

While Vodafone remains one of the leading global telecommunications providers, they face the need to transform their services and reach out to a wider audience. The customer base of a typical telecom provider is shifting, and they can no longer afford to just focus on consumers and need to include enterprises in their go-to-market strategy. Beyond the usual offerings of connectivity and mobile plans, Vodafone Business has solutions for Unified Communications, IoT and Cloud, to help grow their enterprise customer base. Ecosystm Principal Advisor, Tim Sheedy says, “Vodafone is one of the most successful telecom providers in the business space. Vodafone Business already represents around 30% of the Vodafone Group revenue, and unlike most in the telecommunications sector, they are showing growth (albeit moderate!).”
The Role of Telecom Providers in the Cybersecurity Market
An area where enterprises continue to need guidance and support is cybersecurity. The results of the UK Government’s Cyber Security Breaches Survey 2019 found that 32% of UK businesses had experienced a cyber-attack in the previous 12 months. More than a third of UK organisations have made changes in their cyber policies because of the GDPR – a majority focusing on policies first. It is not surprising therefore that Vodafone should identify cybersecurity as the next area of focus for their enterprise offerings.
Sheedy says, ”Cybersecurity services are one of the fastest-growing areas in technology. But because of this, it is a also a crowded market with everyone – from the big telecom providers, IT services providers, big audit firms, mid-sized technology providers down to the smaller cybersecurity experts – playing for this growing spend. It can, however, be argued that telecom providers have some of the deepest experience in cybersecurity and managing the risks – their networks are probably the most targeted by hackers and malicious actors. Telecom providers have massive teams just to stop threats from one or two countries. With all the work they do to protect their own network, they should have the skills to help protect the networks and assets of their clients.”
Ecosystm Principal Advisor, Alex Woerndle concurs, “Telecom providers are perfectly positioned to transition into managed security service providers (MSSPs). They already have the experience in providing a range of managed services, the ability to scale to support clients and some ready-made expertise internally in their in-house cybersecurity capabilities.”
Vodafone’s Foray into Cybersecurity
Vodafone Cyber Enhanced focuses on selected cybersecurity areas – threat analysis and intelligence, managed firewall and managed security services. The global Ecosystm Cybersecurity study finds that the solutions that organisations will invest in most in 2020 are Security Operations (SecOps) & Incident Response (by a third of global organisations) and Threat Analysis & Intelligence (by 20% of global organisations).
Commenting on the areas Vodafone is focusing on, Woerndle says, “Threat analysis and intelligence is where a lot of established SecOps providers and MSSPs are really focusing now. Previously it was simply a matter of monitoring alerts and reporting. Businesses and in-house security teams are now seeking more proactive assistance in searching for threats, before they become attacks. The challenge they face is catching up – effectively jumping from just being another SecOps centre (SOC) monitoring and reporting alerts, to matching the more mature SOCs with proactive threat intelligence to help clients mitigate before an attack is launched. This takes time, as it needs maturity of the SOC and the team, and also data, which established providers have accrued plenty of, over an extended period. While a managed firewall is not really a new service, it makes some sense to couple it with other managed security services to deliver a broader program. Vodafone is absolutely targeting the areas that businesses are looking into presently.”
Woerndle adds, “MSSPs will be crucial to the security sector moving forward. There has been a rapid growth of vendor solutions creating a very confusing market for tech buyers. This is coupled with a tight labour market for skilled people who can manage the tools. It is not surprising , therefore, that 86% of organisations across the world will look to engage with an MSSP when deploying a cybersecurity solution, according to Ecosystm research.”
Sheedy sees an opportunity for Vodafone to go global with their cybersecurity capabilities. “If Vodafone can compete with the bigger players (and perhaps partner with or complement the offerings of the smaller ones), then they should find a significant opportunity, especially within their larger clients – particularly as they move into the software-defined networking space. However, given the confusion around cybersecurity, they should expand their focus beyond larger enterprises to businesses over about 100 employees. As one of the largest global telecom providers, with one of the largest networks, they can be an important player in the cybersecurity space – growing the spend in their business clients. And while this is a UK play for now, one assumes that they will look to expand across their operating countries as Vodafone Cyber Enhanced gains traction.”




















