Ecosystm recently partnered with Asavie to conduct a study into the opportunity and outlook for the “Branch of One”. One of the challenges was actually defining what the Branch of One is. Here’s what we came up with:
Branch of One enables Office Anywhere by delivering secure, frictionless access to all business resources, with full mobility – meeting the security and manageability requirements of CIOs and CISOs.
Basically it is all the data and systems you need to get your job done, in your pocket. Secure. Easy to manage.
What I really like about the idea is that it describes what business is trying to achieve and it gives a common language and outcome for IT and business leaders. Consider all the things that IT and security teams need to do to enable access to applications and data in remote branches – from connectivity to security to data and system access. Often it takes days, weeks or months to open a new office or branch, or to provision a new retail store. Now, imagine having the ability to roll out all of these systems and services in seconds. To a single user or to thousands. Without consideration for location. Business leaders will understand this benefits and will support it.
It also has the opportunity to help nearly every business today. Of the 1005 businesses we interviewed across the globe in our Global CxO Study 2020, 44% admitted to suffering cyber-attack incidents during COVID-19 due to employees working from home – and over half of these attacks were on mobile devices. Compromised devices were the number one target for cyber-attacks in 2020.
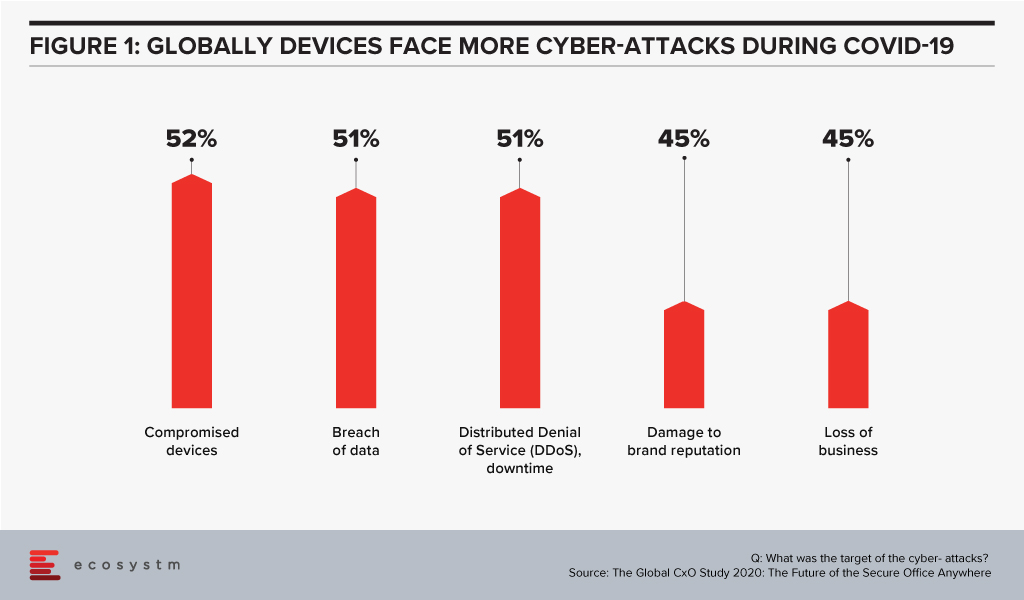
Businesses need a new way to manage the devices and applications of their remote employees. They need to be able to extend the benefits of the WAN to them without the downsides of VPNs. Every business we interviewed saw benefits of bringing devices, locations and offices inside the WAN. Turning every device and office into a Branch of One.
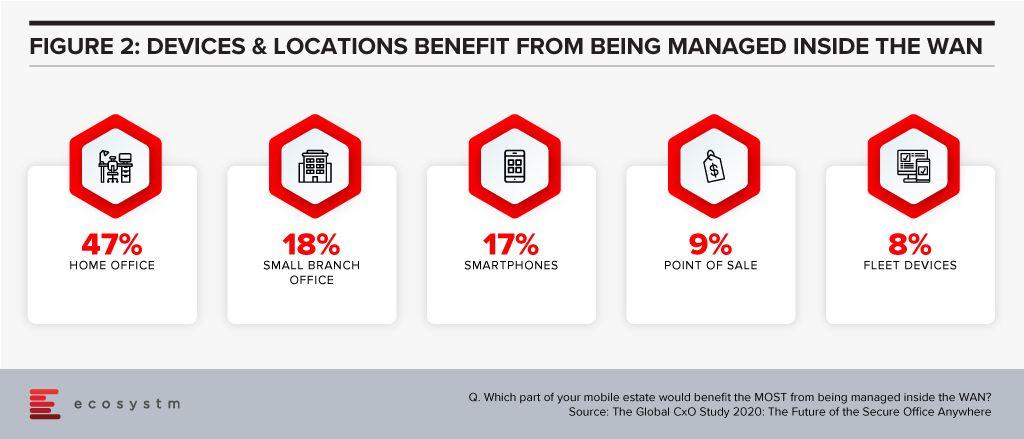
A few security and network technologies have promised this capability – SDNs can offer a similar service, but they require client software to be installed. 78% of businesses we interviewed are using VPNs to bring devices inside the WAN – but again, they require client software, and can be inconsistent (and insecure!) on mobile devices.
Companies that embrace the Branch of One can provision new users in a few clicks. No software to install, no cables to connect, no hardware to provision – it makes life easier for technology and security professionals. The Branch of One gives your employees the systems and data they need to get their job done – delivered securely across the mobile network.
Download the report based on ‘The Global CxO Study 2020: The Future of the Secure Office Anywhere’, conducted by Ecosystm on behalf of Asavie. The report presents the key findings of the study and analyses the market perceptions of Office Anywhere and the need for a ‘Branch of One’, which will be the foundation of enterprise mobile security in the future.

Last week, the Australia government joined other countries in the Asia Pacific region in highlighting the growth of attack surface in the midst of the COVID-19 pandemic.
In our recently launched study Digital Priorities in the New Normal, we find that 87% of organisations in the Asia Pacific have increased investments in one or more cybersecurity solutions. However, this has to be backed by a reassessment of organisations’ risk positions and a re-evaluation of data protection and compliance policies.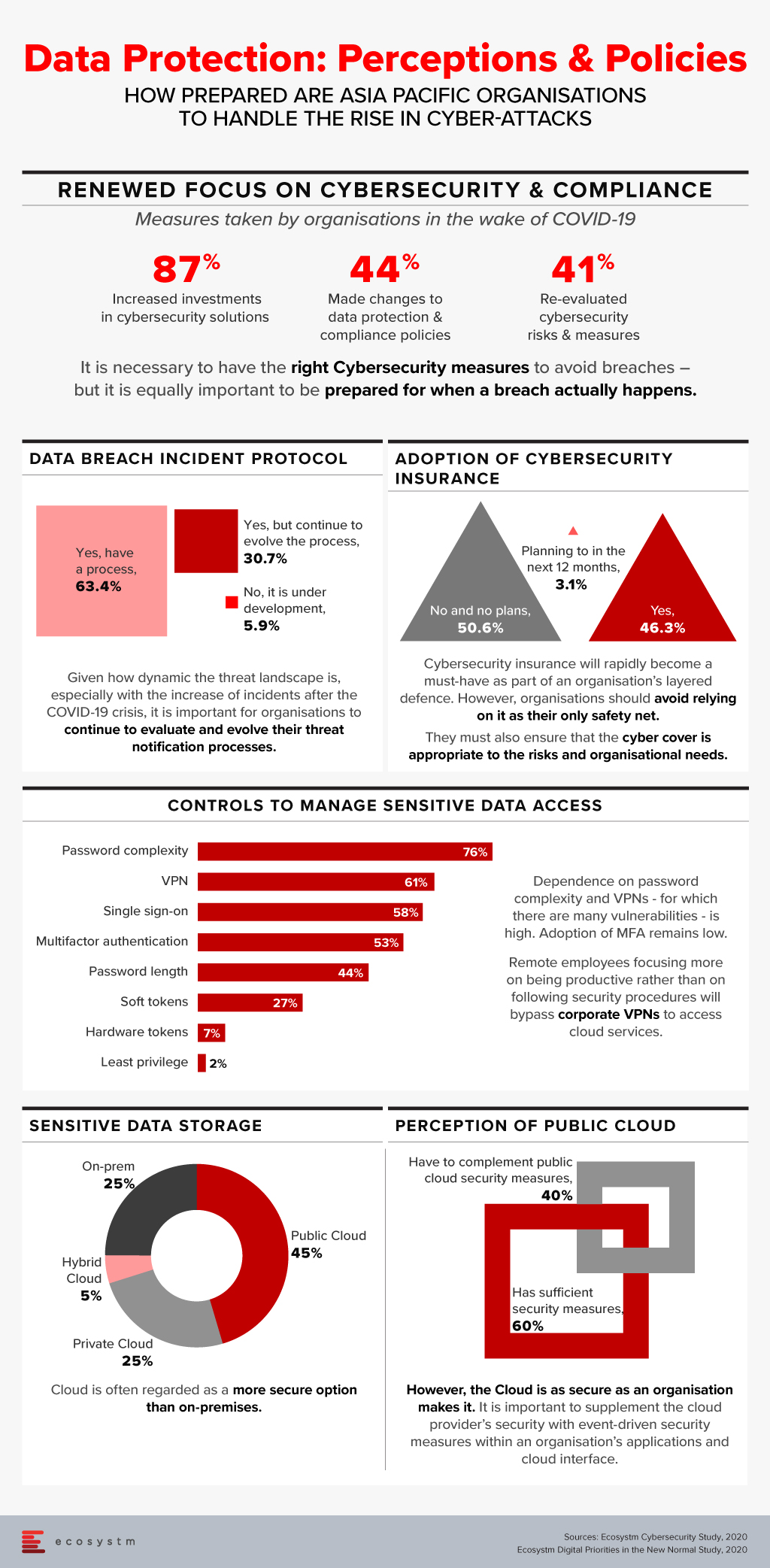

The next phase of a post-COVID world will be one of reduced physical contact, tighter regulations, and new habits and hygiene practices. This will translate into significant process changes which will be deeply enabled by mobile technology. All mobile form factors will be more integrated into how we interact. Interactional changes will be found in our homes, offices, public spaces and services.
In this blog post I address two fundamental questions as a technologist on the underpinnings of this shift:
- How can enterprises find ways of rebuilding and cementing trusted relationships using mobile technology?
- How does our infrastructural foundations support mobile technology for contactless transactions? (privacy, two-factor authentication, data quality and so on)
Situational shift to mobile
Given the rapid shifts in the last six months in how we can interact with each other, enterprises will have to be agile and flexible in process design going forward to optimize opportunities for customer engagements.
We will continue to have further disruptions on how we live and work in the next 12 to 18 months and potentially beyond. Some of the shifts towards mobile have been expected for a while, yet this crisis has pushed the timeline ahead as to how we engage.
Use cases in the “new normal”
Here are some use case examples in this next phase of business where mobile enables the transaction between consumer and environment:
Education. The reskilling and training certification that will be necessary to address unemployment, will be on Mobile First. Because of bandwidth, learner attention span, and form factor, there will be retooling of educational programs to be bite-sized and more media oriented.
Retail. Retail and delivery businesses shifting to remote first, with drop-off points that use mobile for contactless signatory and payment.
Healthcare. Telemedicine primarily by mobile devices (phone, laptop, phablet). Personal medical data sharing over mobile will require enhanced data encryption and two-factor authentication, which needs addressing via encryption and authentication.
Entrepreneurship. More side hustles that are mobile-based and mobile administered. Any authorization and transaction-oriented activities will be driven by mobile.
Government. Requests for document renewal or identity authentication for approval or submission of materials, with one-touch request.
Supply chain. Visibility and tracking of inbound and outbound materials. One-click reordering, and contactless payment verification.
Workplace. Contactless engagement with mobile as authentication of actions (coffee machine payment, copier usage, keyless office, meeting room allocation).
Facilities management. Hygiene controls with personnel health detail tracking (who cleans what room when). Deep cleaning management tools for audit trails, liability.
Role of mobile in creating engagement
Building trust
As we filter through the level of rubbish coming at us via social media, websites and our email, most of us are looking for a trusted information source. Our mobile is our window to the world, and many are applying appropriate filtration to make that world a bit more manageable.
The reason that people did previously download an app was partly based on what information had to be handed over in terms of permissions. The app builder needs to build a trusted relationship on benefit, not on what can be leveraged from the consumer.
To build that trust and create a closer engagement – albeit driven by situational need vs. consumer want – app developers need to consider these consumer needs:
- Level of trust in quality of information provided (e.g. weather info vs something more critical)
- Trust in app data usage and functionality (does it work?)
- Privacy of data being used and being held (statements and auditability)
- Location of data (on whose device: client or server)
- Speed and reaction time (Is there edge computing or the use of IoT to help push mobile information quickly?)
- Loss of data or loss of device and the impact on app access (More than lost passwords, lost processes and lost data)
Technological foundations for mobile usage
Network and bandwidth
We have all experienced bandwidth issues in the last few months, either sharing bandwidth with loved ones in lockdown to peak periods of video conferencing activity across geographic regions. Entertainment content providers such as Netflix and Disney+ were asked to lower the quality of the data streaming.
But then what online activity will take priority? Will we start to see pricing differentials for guarantees of availability? What about subscription models with platinum, gold and silver memberships (as in frequent flyer programmes) as to the network bandwidth you or your activity is allocated? Will things be done over VPN not only for privacy but for priority? I also see VPN as a possible solution towards issues like Zoom bombing and other intrusions to daily business operations.
We come to the role of a pandemic in 5G investment, which is similar to the role of investment in R&D during an economic downturn. Clearly, the world needs better bandwidth with more agility and future-proofed for functionality. You cannot drive a fast car on a bumpy road with potholes.
But for countries losing thousands of citizens to a virus with critical infrastructure at risk, where is the priority of a better telecom infrastructure? My colleague Shamir Amanullah wrote a report prior to the pandemic about the Race for 5G in Southeast Asia which is a good barometer for other regions. There is a good CNBC article from Todd Wassermann on the US situation, and a rather excellent survey on consumer sentiment on 5G from February 2020 by Politico.
Role of data quality and its security
Going back to my previous statement about rubbish and social media, the validation and quality of data exchange is part of the value proposition of using mobile technology.
What aspects of our current IT infrastructure create that ‘data value add’?
IoT and Edge Computing. Most of us are not going to be comfortable in crowds going forward. If I can reserve a space, or I can use a sensor to see how full an environment currently is, it will impact my decision to go somewhere. The faster that real-time information is processed and available, the better the outcome.
Blockchain technology is functioning enough to address the challenge of how to secure the data and prevent malicious cyber-attacks. This includes medical data hacking, supply chain theft, and other data-oriented safety issues on hygiene and product providence that we are experiencing now.
Final thoughts
At Ecosystm, we highlight how and where enterprises plan to invest and adopt technology while adding insights and expertise on to the use cases and trends. We are also able to reflect upon the agility of the same enterprises to make that technology investment count towards the next phase of their business model. In a post-COVID situation we see inventive ways enterprises are using technology. This is not only for societal benefit, but to make a difference in the marketplace. And mobile plays a key role in this next phase of engagements.




