Trust in the Banking, Financial Services, and Insurance (BFSI) industry is critical – and this amplifies the value of stolen data and fuels the motivation of malicious actors. Ransomware attacks continue to escalate, underscoring the need for fortified backup, encryption, and intrusion prevention systems. Similarly, phishing schemes have become increasingly sophisticated, placing a burden on BFSI cyber teams to educate employees, inform customers, deploy multifactor authentication, and implement fraud detection systems. While BFSI organisations work to fortify their defences, intruders continually find new avenues for profit – cyber protection is a high-stakes game of technological cat and mouse!
Some of these challenges inherent to the industry include the rise of cryptojacking – the unauthorised use of a BFSI company’s extensive computational resources for cryptocurrency mining.
Building Trust Amidst Expanding Threat Landscape
BFSI organisations face increasing complexity in their IT landscapes. Amidst initiatives like robo-advisory, point-of-sale lending, and personalised engagements – often facilitated by cloud-based fintech providers – they encounter new intricacies. As guest access extends to bank branches and IoT devices proliferate in public settings, vulnerabilities can emerge unexpectedly. Threats may arise from diverse origins, including misconfigured ATMs, unattended security cameras, or even asset trackers. Ensuring security and maintaining customer trust requires BFSI organisations to deploy automated and intelligent security systems to respond to emerging new threats.
Ecosystm research finds that nearly 70% of BFSI organisations have the intention of adopting AI and automation for security operations, over the next two years. But the reality is that adoption is still fairly nascent. Their top cyber focus areas remain data security, risk and compliance management, and application security.
Addressing Alert Fatigue and Control Challenges
According to Ecosystm research, 50% of BFSI organisations use more than 50 security tools to secure their infrastructure – and these are only the known tools. Cyber leaders are not only challenged with finding, assessing, and deploying the right tools, they are also challenged with managing them. Management challenges include a lack of centralised control across assets and applications and handling a high volume of security events and false positives.
Software updates and patches within the IT environment are crucial for security operations to identify and address potential vulnerabilities. Management of the IT environment should be paired with greater automation – event correlation, patching, and access management can all be improved through reduced manual processes.
Security operations teams must contend with the thousands of alerts that they receive each day. As a result, security analysts suffer from alert fatigue and struggle to recognise critical issues and novel threats. There is an urgency to deploy solutions that can help to reduce noise. For many organisations, an AI-augmented security team could de-prioritise 90% of alerts and focus on genuine risks.
Taken a step further, tools like AIOps can not only prioritise alerts but also respond to them. Directing issues to the appropriate people, recommending actions that can be taken by operators directly in a collaboration tool, and rules-based workflows performed automatically are already possible. Additionally, by evaluating past failures and successes, AIOps can learn over time which events are likely to become critical and how to respond to them. This brings us closer to the dream of NoOps, where security operations are completely automated.
Threat Intelligence and Visibility for a Proactive Cyber Approach
New forms of ransomware, phishing schemes, and unidentified vulnerabilities in cloud are emerging to exploit the growing attack surface of financial services organisations. Security operations teams in the BFSI sector spend most of their resources dealing with incoming alerts, leaving them with little time to proactively investigate new threats. It is evident that organisations require a partner that has the scale to maintain a data lake of threats identified by a broad range of customers even within the same industry. For greater predictive capabilities, threat intelligence should be based on research carried out on the dark web to improve situational awareness. These insights can help security operations teams to prepare for future attacks. Regular reporting to keep CIOs and CISOs informed of the changing threat landscape can also ease the mind of executives.
To ensure services can be delivered securely, BFSI organisations require additional visibility of traffic on their networks. The ability to not only inspect traffic as it passes through the firewall but to see activity within the network is critical in these increasingly complex environments. Network traffic anomaly detection uses machine learning to recognise typical traffic patterns and generates alerts for abnormal activity, such as privilege escalation or container escape. The growing acceptance of BYOD has also made device visibility more complex. By employing AI and adopting a zero-trust approach, devices can be profiled and granted appropriate access automatically. Network operators gain visibility of unknown devices and can easily enforce policies on a segmented network.
Intelligent Cyber Strategies
Here is what BFSI CISOs should prioritise to build a cyber resilient organisation.
Automation. The volume of incoming threats has grown beyond the capability of human operators to investigate manually. Increase the level of automation in your SOC to minimise the routine burden on the security operations team and allow them to focus on high-risk threats.
Cyberattack simulation exercises. Many security teams are too busy dealing with day-to-day operations to perform simulation exercises. However, they are a vital component of response planning. Organisation-wide exercises – that include security, IT operations, and communications teams – should be conducted regularly.
An AIOps topology map. Identify where you have reliable data sources that could be analysed by AIOps. Then select a domain by assessing the present level of observability and automation, IT skills gap, frequency of threats, and business criticality. As you add additional domains and the system learns, the value you realise from AIOps will grow.
A trusted intelligence partner. Extend your security operations team by working with a partner that can provide threat intelligence unattainable to most individual organisations. Threat intelligence providers can pool insights gathered from a diversity of client engagements and dedicated researchers. By leveraging the experience of a partner, BFSI organisations can better plan for how they will respond to inevitable breaches.
Conclusion
An effective cybersecurity strategy demands a comprehensive approach that incorporates technology, education, and policies while nurturing a culture of security awareness throughout the organisation. CISOs face the daunting task of safeguarding their organisations against relentless cyber intrusion attempts by cybercriminals, who often leverage cutting-edge automated intrusion technologies.
To maintain an advantage over these threats, cybersecurity teams must have access to continuous threat intelligence; automation will be essential in addressing the shortage of security expertise and managing the overwhelming volume and frequency of security events. Collaborating with a specialised partner possessing both scale and experience is often the answer for organisations that want to augment their cybersecurity teams with intelligent, automated agents capable of swiftly

There are a number of updates to regulations that will impact organisations in 2023. They will create new requirements for businesses to follow, new areas of risk, and more money and time spent adjusting to these changes.
Compliance strategies help cement trust in professional partnerships and vendor relationships. Whether organisations are trying to qualify for cyber insurance, or simply looking to obey the law and avoid fines, they are up against increasingly tough compliance measures. It is no longer sufficient to be compliant only once in a year, scramble in the two weeks before the audit, and then forget about it for the rest of the year.
What compliance tech trends should IT management adopt as they build and refine their technology roadmaps?
Let’s look at some regulatory and technology trends.
Regulations to Watch
European Union Digital Operational Resilience Act (DORA). The EU is applying regulatory pressure on the financial services industry with its Digital Operational Resilience Act (DORA). DORA is a “game changer” that will push firms to fully understand how their IT, operational resilience, cyber and third-party risk management practices affect the resilience of their most critical functions as well as develop entirely new operational resilience capabilities.
One key element that DORA introduces is the Critical Third Party (CTP) oversight framework, expanding the scope of the financial services regulatory perimeter and granting the European Supervisory Authorities (ESAs) substantial new powers to supervise CTPs and address resilience risks they might pose to the sector.
Germany’s Supply Chain Due Diligence Act (SCDDA). On January 1, 2023, the Supply Chain Due Diligence Act took effect. It requires all companies with head offices, principal places of business, or administrative headquarters in Germany – with more than 3,000 employees in the country – to comply with core human rights and certain environmental provisions in their supply chains. SCDDA is far-reaching and impacts multiple facets of the supply chain, from human rights to sustainability, and legal accountability throughout the third-party ecosystem. It will address foundational supply chain issues like anti-bribery and corruption diligence.
From 2024, the number of employees will be lowered from 3,000 to 1,000. And Switzerland, The Netherlands, and the European Union also have similar drafts of regulation in the books.
PCI DSS 4.0. Payment Card Industry Data Security Standard (PCI DSS) is the core component of any credit card company’s security protocol. In an increasingly cashless world, card fraud is a growing concern. Any company that accepts, transmits, or stores a cardholder’s private information must be compliant. PCI compliance standards help avoid fraudulent activity and mitigate data breaches by keeping the cardholder’s sensitive financial information secure.
PCI compliance standards require merchants to consistently adhere to the PCI Standards Council’s guidelines which include 78 base requirements, more than 400 test procedures, and 12 key requirements.
Looking at how PCI has evolved over the years up to PCI 4.0, there is a departure from specific technical requirements toward the general concept of overall security. PCI 4.0 requirements were released in March 2022 and will become mandatory in March 2024 for all organisations that process or store cardholder data.
The costs of maintaining compliance controls and security measures are only part of what businesses should consider for PCI certification. Businesses should also account for audit costs, yearly fees, remediation expenses, and employee training costs in their budgets as well as technical upgrades to meet compliance standards.
Tech Trend Changes
Zero Trust presents a shift from a location-centric model to a more data-centric approach for fine-grained security controls between users, systems, data, and assets. Zero Trust as a model assumes all requests are from an open network and verifies each request this way. PCI 4.0 does not mention Zero Trust architecture specifically, but it is evident that the Security Standards Council is going that way as a future consideration.
Passwordless authentication has gained a lot of attention and traction recently. large tech providers such as Google, Apple, and Microsoft, are introducing passwordless authentication based on passkeys. This is a clear sign that the game is about to change. As the PCI DSS focuses on avoiding fraudulent activity, so does newer authentication protocol approaches to verify and confirm identity.
Third-party risk management is quickly evolving into third-party trust management (TPTM), with the SCDDA creating a clear line in the sand for global organisations. TPTM is a critical consideration when standing up an enterprise trust strategy. Enterprise trust is a driver of business development that depends on cross-domain collaboration. It goes beyond cybersecurity and focuses on building trusted and lasting third-party relationships across the core critical risk domains: security, privacy, ethics & compliance, and ESG.
Final thought – Cyber Insurance in 2023
If some of these compliance drivers lead to a desire for financial protection, cyber insurance is one mitigation element for strategy to address C-level concerns. But wait – this is not as easy as it used to be.
Five years ago, a firm could fill out a one-page cyber insurance application and answer a handful of questions. Fast forward to today’s world of ransomware attacks and other cyber threats – now getting insurance with favourable terms, conditions, pricing, coverage and low retention is tough.
Insurance companies prefer enterprises that are instituting robust security controls and incident response plans — especially those prepared to deep dive into their cybersecurity architectures and with planned roadmaps. In terms of compliance strategy development, there needs to be a risk-based approach to cybersecurity to allow an insurer to offer a favourable insurance option.
In the rush towards digital transformation, individual lines of business in organisations, have built up collections of unconnected systems, each generating a diversity of data. While these systems are suitable for rapidly launching services and are aimed at solving individual challenges, digital enterprises will need to take a platform approach to unlock the full value of the data they generate.
Data-driven enterprises can increase revenue and shift to higher margin offerings through personalisation tools, such as recommendation engines and dynamic pricing. Cost cutting can be achieved with predictive maintenance that relies on streaming sensor data integrated with external data sources. Increasingly, advanced organisations will monetise their integrated data by providing insights as a service.
Digital enterprises face new challenges – growing complexity, data explosion, and skills gap.
Here are 5 ways in which IT teams can mitigate these challenges.
- Data & AI projects must focus on data access. When the organisation can unify data and transmit it securely wherever it needs to, it will be ready to begin developing applications that utilise machine learning, deep learning, and AI.
- Transformation requires a hybrid cloud platform. Hybrid cloud provides the ability to place each workload in an environment that makes the most sense for the business, while still reaping the benefits of a unified platform.
- Application modernisation unlocks future value. The importance of delivering better experiences to internal and external stakeholders has not gone down; new experiences need modern applications.
- Data management needs to be unified and automated. Digital transformation initiatives result in ever-expanding technology estates and growing volumes of data that cannot be managed with manual processes.
- Cyber strategy should be Zero Trust – backed by the right technologies. Organisations have to build Digital Trust with privacy, protection, and compliance at the core. The Zero Trust strategy should be backed by automated identity governance, robust access and management policies, and least privilege.
Read below to find out more.
Download The Future of Business: 5 Ways IT Teams Can Help Unlock the Value of Data as a PDF

Organisations in Australia and New Zealand (ANZ) are focusing their digital transformation efforts on continued innovation in the experiences they deliver to their customers and employees.
Innovation has been at the core of organisations’ survival strategies – now it will be the means to gain competitive advantage and is getting prioritised over resiliency, business continuity and compliance.
Here are 5 insights on where ANZ organisations are headed in the tech priorities and investments, based on the findings of the Ecosystm Digital Enterprise Study, 2022.
- Tech Teams in ANZ are restructuring after a two-year struggle and as they face skills shortage.
- Tech investments are focusing on experience and digital workplace and customer experience technologies are seeing continued growth.
- Hybrid cloud investments are focused on augmenting existing infrastructure – whether public or on-prem
- Sales & Marketing are leveraging data & AI solutions the most; IT Ops and SecOps will see un uptick in 2023
- Cybersecurity practices are not evolving fast enough with only 9% of organisations having implemented Zero Trust
More insights into the ANZ tech market below.
Click here to download The Future of the Digital Enterprise – Australia & New Zealand as a PDF

Against a backdrop of extended disruption, cybersecurity risks are expanding rapidly and current defences are inadequate. Ransomware attacks are increasing in frequency and impact, focusing more on targets where outages are not an option, such as critical infrastructure and hospitals. Supply chain attacks are creating chaos and has led to a much-needed focus on supply chain vulnerabilities.
As digitalisation continues at a faster pace, cybersecurity is too often, a secondary concern.
With the acceleration of cloud adoption; widespread remote working; the resulting proliferation of endpoints; and the expansion of attack surface for malicious actors, this is the time for organisations to transform their cybersecurity approaches.
Here are the 5 steps that you should consider:
- Having CISOs report directly into top management – bypassing CIOs
- Focusing on configuration management
- Building resilience against ransomware attacks
- Migrating away from a legacy perimeter-based approach
- Shifting to Policy-as-Code
In 2022, attacks on organisations will grow in frequency and intensity. Organisations need to transform their approaches to cybersecurity. This involves embracing new concepts such as zero-trust and Secure Access Service Edge (SASE) as well as a stronger focus on policy as code and human factors.
Click here to download Shaping your Cyber Practice in 2022 as a PDF

One of the main questions that I have faced over the past week, since I wrote the Ecosystm Insight – Welcome to the Great Bounce Forward – is “How is this different to the “New Normal”? Many have commented that the concept of the Great Bounce Forward is more descriptive and more positive than the term “New Normal” – but I believe they are different, and require different strategies and mindsets.
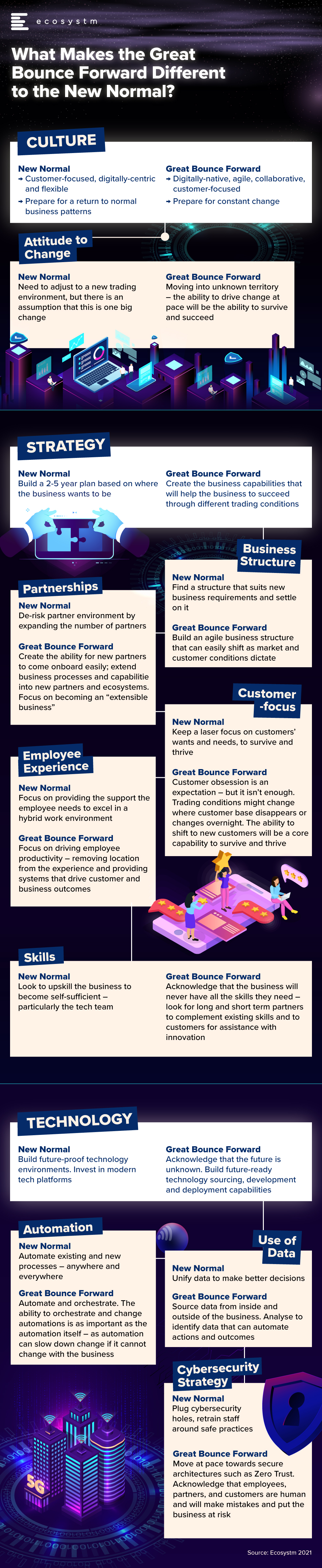
This is a brief summary of some of the major differences between the New Normal and the Great Bounce Forward. I look forward with excitement and some trepidation towards this future. One where business success will be dictated not only by our customer obsession, but also the ability of our business to pivot, shift, change and adapt.
I can’t tell you what will happen in the future – a green revolution? Another pandemic? A major war? A global recession? Market hypergrowth? All the people living life in peace? Imagine that…
What I can tell you is what your organisation needs to do to be able to meet all of these challenges head-on and set yourself up for success. And to me, that won’t look like the new normal. There is nothing normal about these business capabilities at all.

Ecosystm research finds that 47% of organisations re-evaluated cybersecurity risks and management making it the biggest measure undertaken by IT Teams when COVID-19 hit. There is no denying any more that cybersecurity is a key business enabler. This year witnessed cybercrime escalating in all parts of the world and several governments issued advisories warning enterprises and citizens of the increase in the threat landscape, during and post COVID-19. Against this backdrop, Ecosystm Advisors, Alex Woerndle, Andrew Milroy, Carl Woerndle and Claus Mortensen present the top 5 Ecosystm predictions for Cybersecurity & Compliance in 2021.
This is a summary of the predictions, the full report (including the implications) is available to download for free on the Ecosystm platform here.
The Top 5 Cybersecurity & Compliance Trends for 2021
- There will be Further Expansion of M&A Activities Through 2021 and Beyond
As predicted last year, the market is set to witness mergers and acquisitions (M&As) to consolidate the market. The pandemic has slowed down M&A activities in 2020. However, the market remains fragmented and there is a demand for consolidation. As the cyber market continues to mature, we expect M&A activities to ramp up over the next couple of years especially once we emerge from COVID-19. Some organisations that understand the full impact of the shift to remote working and the threats it creates have embraced the opportunity to acquire, based on perceived value due to COVID-19. The recent acquisition of Asavie by Akamai Technologies is a case in point. Asavie’s platform is expected to strengthen Akamai’s IoT and mobile device security and management services.
- After a Year of Pandemic Leniency, Regulators will Get Stricter in 2021
The regulators in the EU appear to have gone through a period of relative leniency or less activity during the first few months of the pandemic and have started to increase their efforts after the summer break. Expect regulators – even outside the EU – to step up their enforcement activities in 2021 and seek larger penalties for breaches.
Governments continue to evolve their Compliance policies across broader sectors, which will impact all industries. As an example, in Australia, the Federal Government has made changes to its definition of critical infrastructure, which brings mandates to many more organisations. Governments have shown an acute awareness of the rise in cyber-attacks highlighted by several high-profile breaches reported in mainstream media. Insider threats – highlighted by Tesla, where an employee raised the allegations of bribery by unknown third parties in exchange for exfiltrating corporate information – will also lead regulators to double down on their enforcement activities.
- The Zero Trust Model Will Gain Momentum
Remote working has challenged the traditional network security perimeter model. The use of personal and corporate devices to access the network via public networks and third-party clouds is creating more opportunity for attackers. Organisations have started turning to a Zero Trust security model to mitigate the risk, applying advanced authentication and continuous monitoring. We expect the adoption of the Zero Trust model to gain momentum through 2021. This will also see an increase in managed services around active security monitoring such as Threat Detection & Response and the increased adoption of authentication technologies. With an eye on the future, especially around quantum computing, authentication technologies will need to continually evolve.
- The Endpoint Will be the Weakest Link
The attack surface continues to grow exponentially, with the increase in remote working, IoT devices and multicloud environments. Remote endpoints require the same, if not higher levels of security than assets that sit within corporate firewalls, and it will become very clear to organisations that endpoints are the most vulnerable. Remote workers are often using unsecure home Wi-Fi connections and unpatched VPNs, and are increasingly vulnerable to phishing attacks. IoT device passwords are often so weak that brute-force attackers can enter networks in milliseconds.
Although endpoint security can be dealt with through strict policies together with hardware or software authentication, the difficult part is to adopt an approach that retains a relatively high level of security without having a too negative an impact on the employee experience. Experience shows that if the security measures are too cumbersome, employees will find ways to circumvent them.
- Hackers Will Turn the Table on AI Security
Cybersecurity vendors are increasingly offering solutions that leverage AI to identify and stop cyber-attacks with less human intervention than is typically expected or needed with traditional security approaches. AI can enhance cybersecurity by better predicting attacks enabling more proactive countermeasures, shortening response times, and potentially saving cybersecurity investment costs. The problem is that the exact same thing applies to the hackers. By leveraging AI, the costs and efforts needed to launch and coordinate large hacker attacks will also go down. Hackers can automate their attacks well beyond the use of botnets, target and customise their attacks with more granularity than before and can effectively target the biggest weakness of any IT security system – people.
Already, phishing attacks account for many of the breaches we see today typically by employees being tricked into sharing their IT credentials via email or over the phone. As we move forward, these types of attacks will become much more sophisticated. Many of the deepfake videos we see have been made using cheap or free AI-enabled apps that are easy enough for even a child to use. As we move into 2021, this ability to manipulate both video and audio will increasingly enable attackers to accurately impersonate individuals.