
A report published by PWC last year states that “While CIOs and CISOs can take care of the technological aspects and in some cases compliance, the business risk, which is now apparent after the emergence of endless breaches in large conglomerates, can best be understood and managed in the boardroom.”
While I agree that cybersecurity is both an operational and business risk, the question of understanding the threat landscape and the risk exposure/risk position of the company falls on both parts of the business. The Board is responsible for the exposure and financial remediation of cyber risk, whereas the IT management is more operationally responsible for prioritisation of actions and remedies. But they need to be able to communicate on this topic together from both sides of the equation. Ecosystm research finds that 98% of global organisations involve the Board to drive their cybersecurity vision, while 88% of organisations look to their IT teams for operational management.
So, where do these two parties meet? How does the risk position of the company get communicated to both parties in such a way that they can both take the necessary actions and prioritise the resource allocation?
Dashboards for Discussion
This is where the discussion on cyber risk dashboards comes up. It is not a new topic, but some of the more recent solutions introduced in the market move beyond penetration testing to really highlighting the risk posture of the business and where resources should be allocated, as well as where the business compares to others in their industry. I will give a specific example of one such approach a bit later in this blog post.
I find the gamification aspect (e.g. industry comparison) a real driver for the Boardroom, as it allows them to position their risk profile against others to the relevant stakeholders and regulators of the business. Actionable metrics that can also be compared to others gives a feeling of control over a situation that frequently lacks control boundaries.
Maturity models vs. risk profiles
In the PwC article I mentioned earlier [written last year by Sivarama Krishnan], the focus was on actions the Board can take, which include the usual discussions of cyber insurance, data handling policies, reporting structures and a tie into the strategy of the business overall. But at a top-level, setting these kinds of priorities can only work when you have some form of metric checking to assess how operationally these kinds of strategic decisions are working for the business.
Figure 1: Barometric Reporting Scale
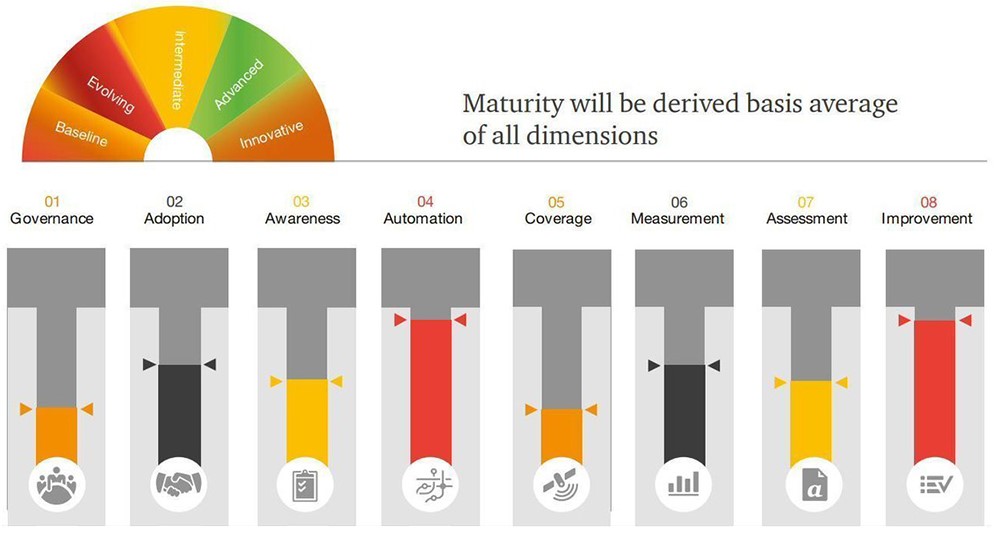
Source: PwC, March 2019
Having a reporting scale that is not only relevant and measurable but also actionable is key to tying the strategic decisions to the operational activities and overall resource and time allocations. You could use a cyber risk strategy framework, such as this one shown in Figure 1, but it needs to be fed with real-time information on the risk position of the business.
Creating actionable metrics
I mentioned previously that there is a need for solutions that create a communication point between the Board and the operational IT teams as to what risk position exists for the business, and how they compare to others in their industry.
Dashboards that create an overview of the risk portfolio exist, but they do not always tie to specific financial impacts to the business. Integrated risk management platforms, such as the one from CyberSaint Security, prioritise cybersecurity as a business risk and give access to the Board to have the ability to drill down into their compliance and risk posture across business units, asset types, projects and regions.
But one of the more concerning aspects of cybersecurity recently is ransomware, which locks up operations until a ransom is paid. One such solution that focuses specifically on the financial impact on the bottom line of ransomware comes from RiskSense and was launched last month. As a background, the RiskSense Platform utilises machine learning, risk-based scoring and analytics combined with technology-accelerated penetration testing, and then identifies and prioritises remediation of critical vulnerabilities that place organisations at risk.
Given the concern at the Board level on Ransomware, RiskSense decided to focus on the very vulnerabilities that make ransomware attacks possible. They recently announced their RiskSense Ransomware Dashboard which reveals all assets within the IT structure that are at risk to active exploits used by ransomware in the wild. This Dashboard examines the vulnerabilities used by ransomware based on risk factors including the presence of dangerous remote code execution (RCE) and privilege escalation (PE) capabilities, as well as vulnerabilities that are “trending” to narrow and identify which should be prioritised for immediate remediation.
Figure 2: RiskSense Executive Dashboard
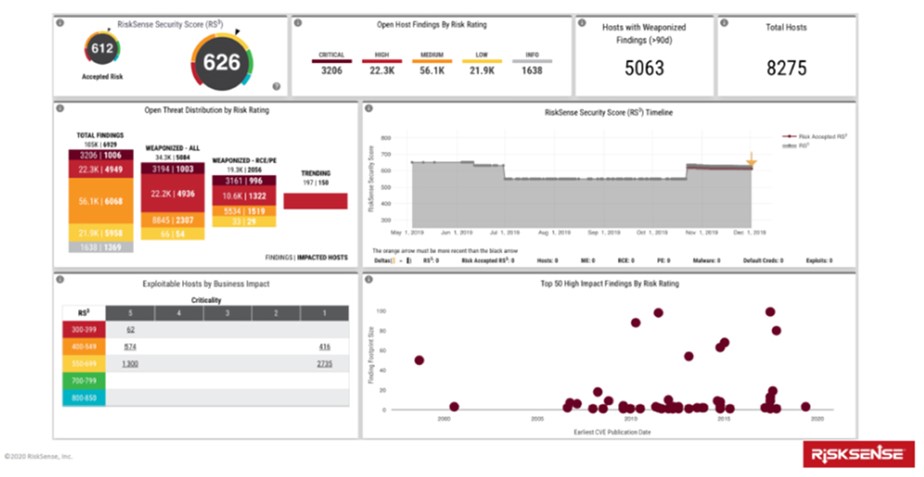
Source: RiskSense, January 2020
In my opinion, this specific example highlights the two unique features of the RiskSense Ransomware Dashboard. For IT management, it is its ability to contextualise the threat landscape to highlight priorities and position the current security posture of the company. And for the Board, it is to compare the situation of the company to others in their industry to benchmark within the industry domain how effectively their cybersecurity efforts have been deployed. It puts the security team in more of an offensive (vs. defensive) mode towards its cybersecurity efforts and outcomes. And it allows the IT team to be able to communicate the risk position of the business to the Board with a series of actionable steps to address the vulnerability.
So from a communications aspect, and that of a shared resource to view vulnerabilities and actions, the introduction of the RiskSense Ransomware Dashboard makes financial risk sense, if you will pardon the pun.
Risk transparency
For both regulatory and financial reasons, Board-level executives need to have cyber risk information for business decisions. This means having access to drill-down capabilities that show gap analyses from the category to the control level for various frameworks or standards. This might include either the NIST Cybersecurity Framework, CIS Critical Security Controls, ISO27002 or various privacy standards such as the NIST Privacy Framework and emerging California Consumer Privacy Act (CCPA).
Dashboards that tie to these frameworks do exist, but they need to be able to be used for communication of actionable activities and resource allocation, not just as a reporting mechanism for regulatory bodies and shareholders. The RiskSense Ransomware Dashboard discussed above is one good example of making transparency actionable and comparable. We need more of those in the industry to keep the communication flowing.







Great content! Super high-quality! Keep it up! 🙂